Kubernetes adoption, security, and market trends report 2024
Executive summary
Our 2024 edition of the State of Kubernetes security report delves into the latest findings from our annual survey around cloud-native security, focusing on containerized workloads and Kubernetes. This report is based on a survey of 600 DevOps, engineering, and security professionals from across the globe spanning large enterprises and small-to-medium sized organizations. The report examines some of the most common cloud-native security challenges, trends, and business influences that organizations experience today.
Report highlights:
- Two-thirds of respondents reported delaying or slowing down application deployment due to Kubernetes security concerns.
- Almost half of respondents report numerous adverse effects as a result of container and Kubernetes security and compliance incidents, including revenue loss and fines.
- Vulnerabilities and misconfigurations are top security concerns within container and Kubernetes environments.
- 90% of respondents have a DevSecOps initiative underway.
Using our survey results, you can evaluate your own Kubernetes security to find areas of improvement and gain insights for reducing security gaps.
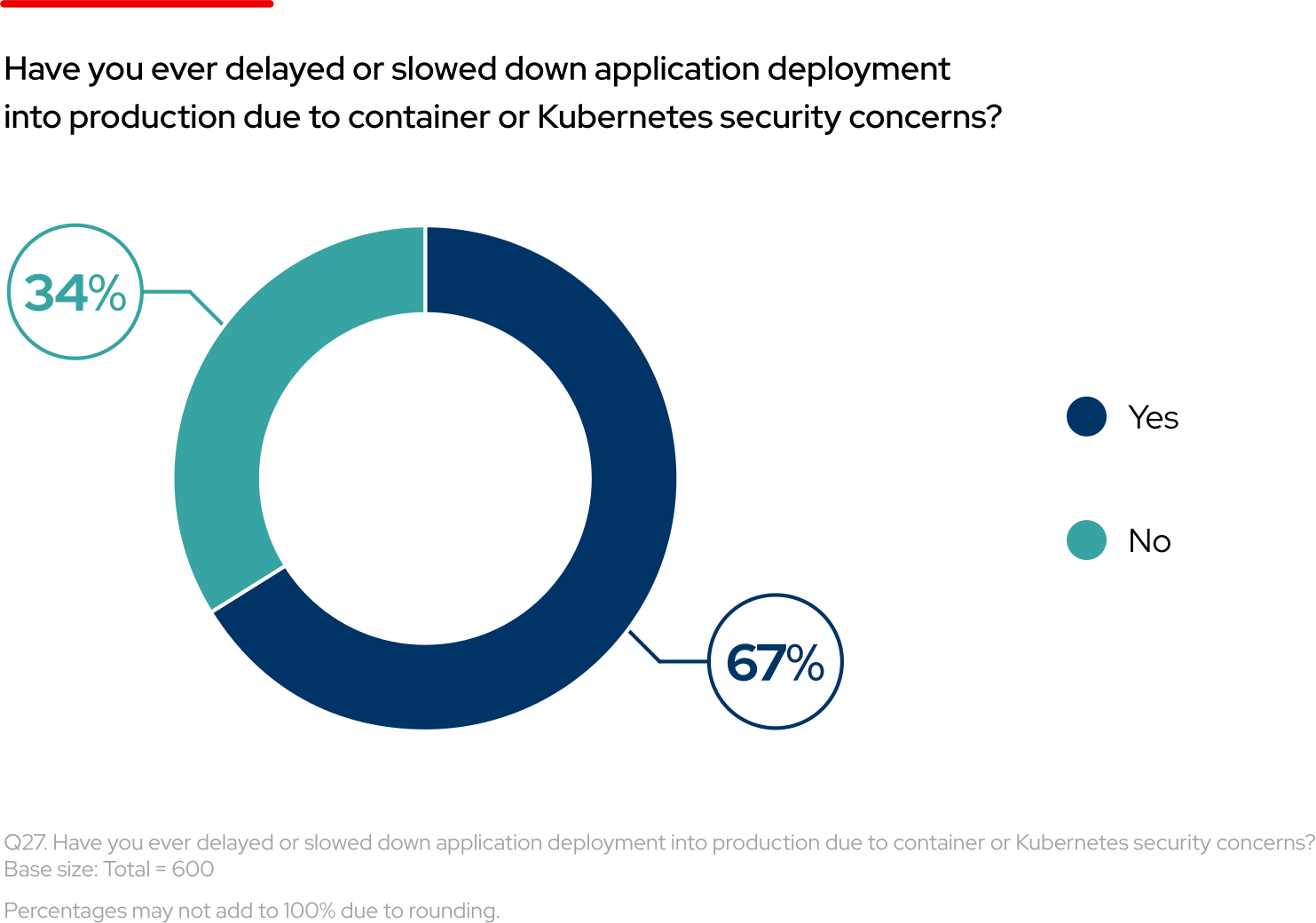
Security issues forced 67% of companies to delay or slow down application deployment
Worldwide, organizations adopt cloud-native technologies like Kubernetes and microservices-based architectures to transform how they build, run, and scale applications. While some organizations develop all new software as microservices, many refactor existing applications using container-based technologies. In either case, containers can speed development and release cycles while increasing flexibility to run and manage applications across hybrid environments.
However, incomplete security throughout the application lifecycle—from development to deployment and maintenance—can diminish these valuable benefits of containerization. Our survey found that 67% of respondents have delayed or slowed down deployment of container-based applications due to security concerns.
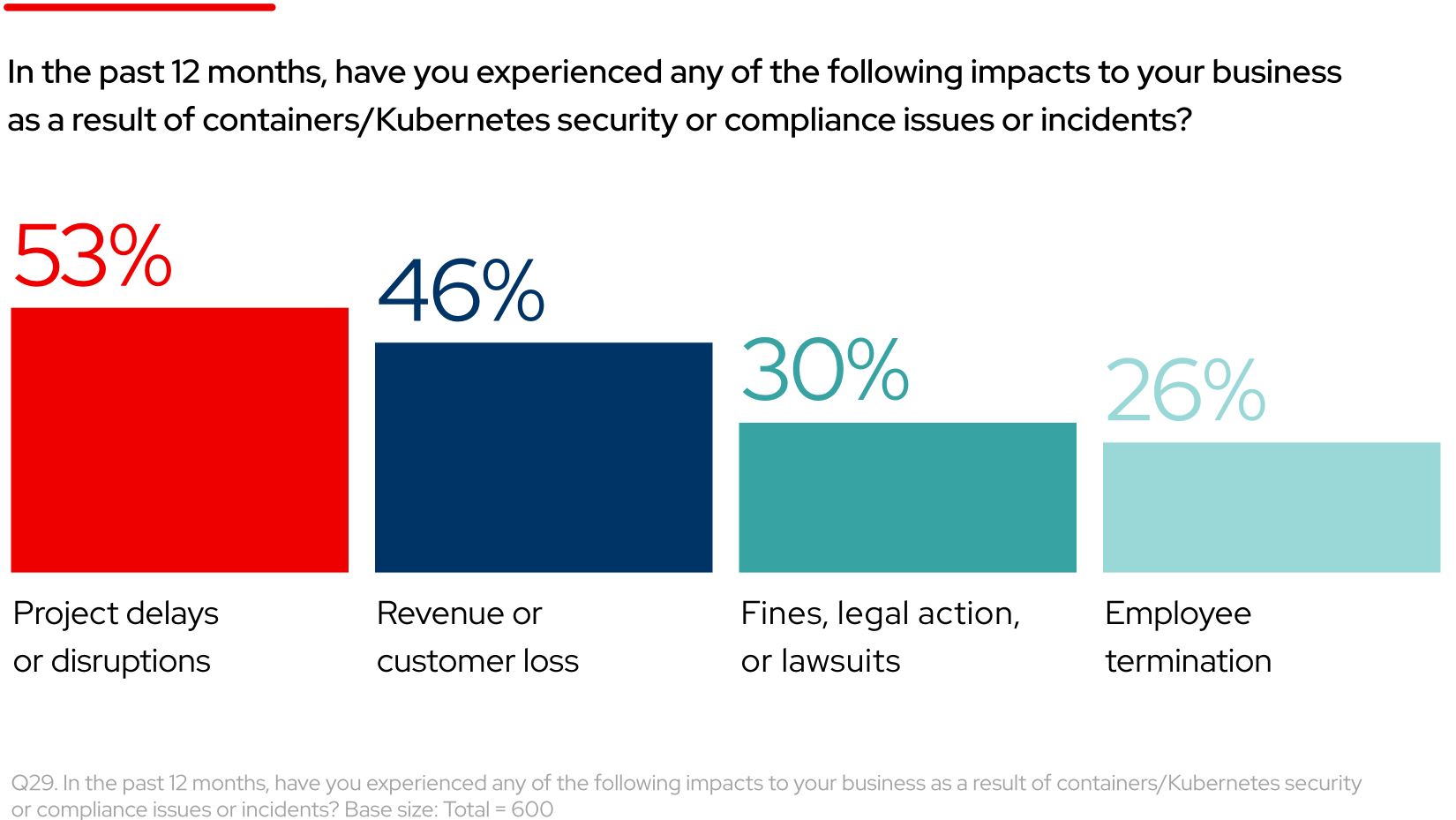
46% of respondents identified revenue or customer loss as a result of a container and Kubernetes security incident
The impact of container and Kubernetes security issues can go well beyond delayed application deployments. 26% of respondents said that a security incident led to employee termination, while 30% reported that their organization was fined as a result of the incident. In these situations, the loss of valuable talent, knowledge, and experience can significantly affect operations, while fines and negative publicity can place significant financial burdens on businesses.
46% of respondents also revealed that their organization experienced revenue or customer loss as a result of a security incident. Security breaches can slow business growth when teams delay projects or product releases while they work to remediate issues. As customers lose trust in a business’s data protection abilities, they may turn to competitors that engage in more security-focused practices.
Nearly 9 in 10 organizations had at least 1 container or Kubernetes security incident in the last 12 months
Security incidents are not confined to the deployment phase of the application life cycle. Instead, container- and Kubernetes-related security incidents can impact all phases of the application life cycle. While 45% of respondents reported that their organizations experienced runtime incidents in the last 12 months, an almost equal number (44%) said they encountered issues in build and deployment phases, citing major vulnerabilities to remediate. At the same time, 40% said their organization detected misconfigurations in their container or Kubernetes environments, and 26% reported that their organization failed an audit.
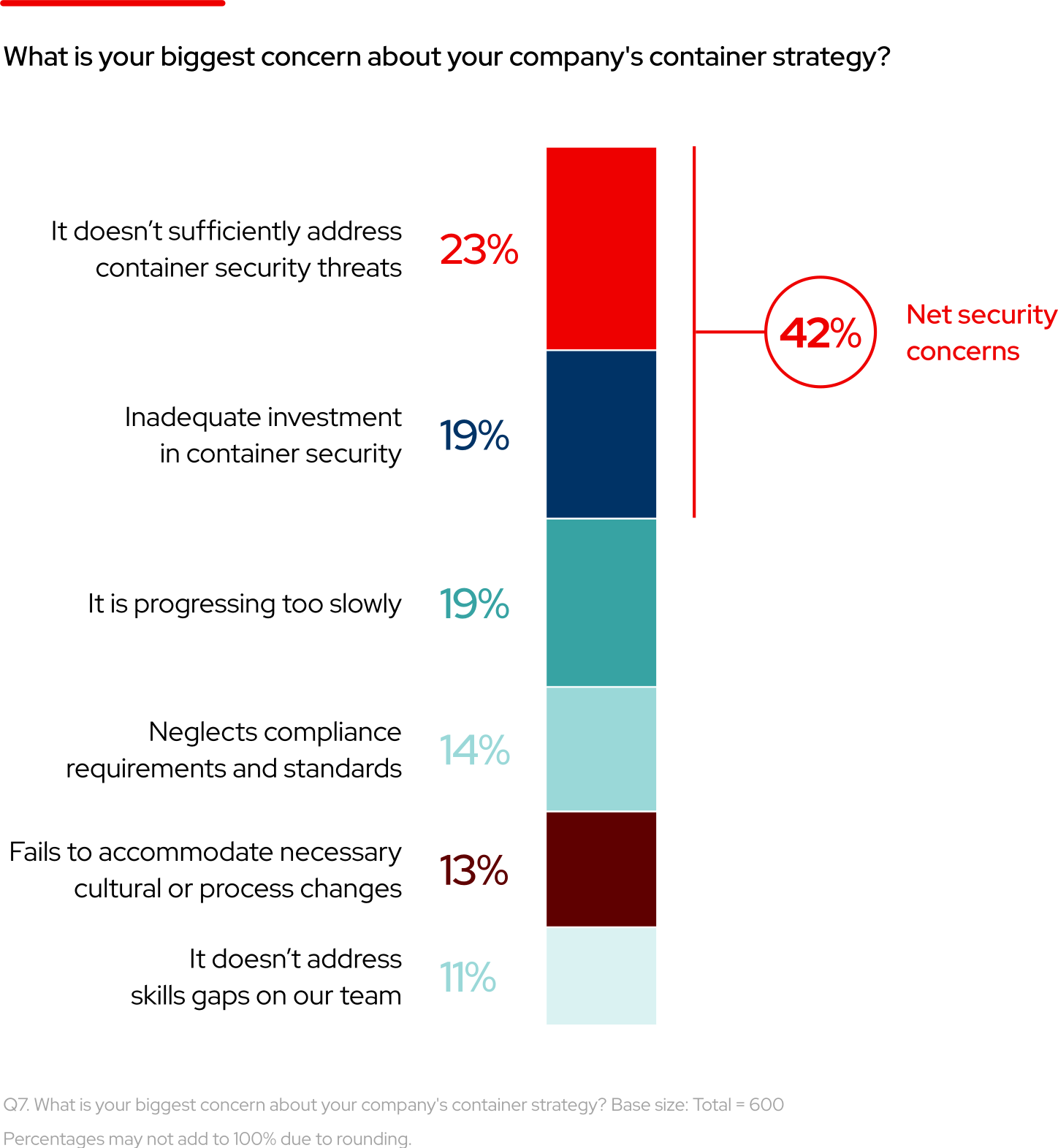
42% of respondents believe that their company does not sufficiently invest in container security or address related threats
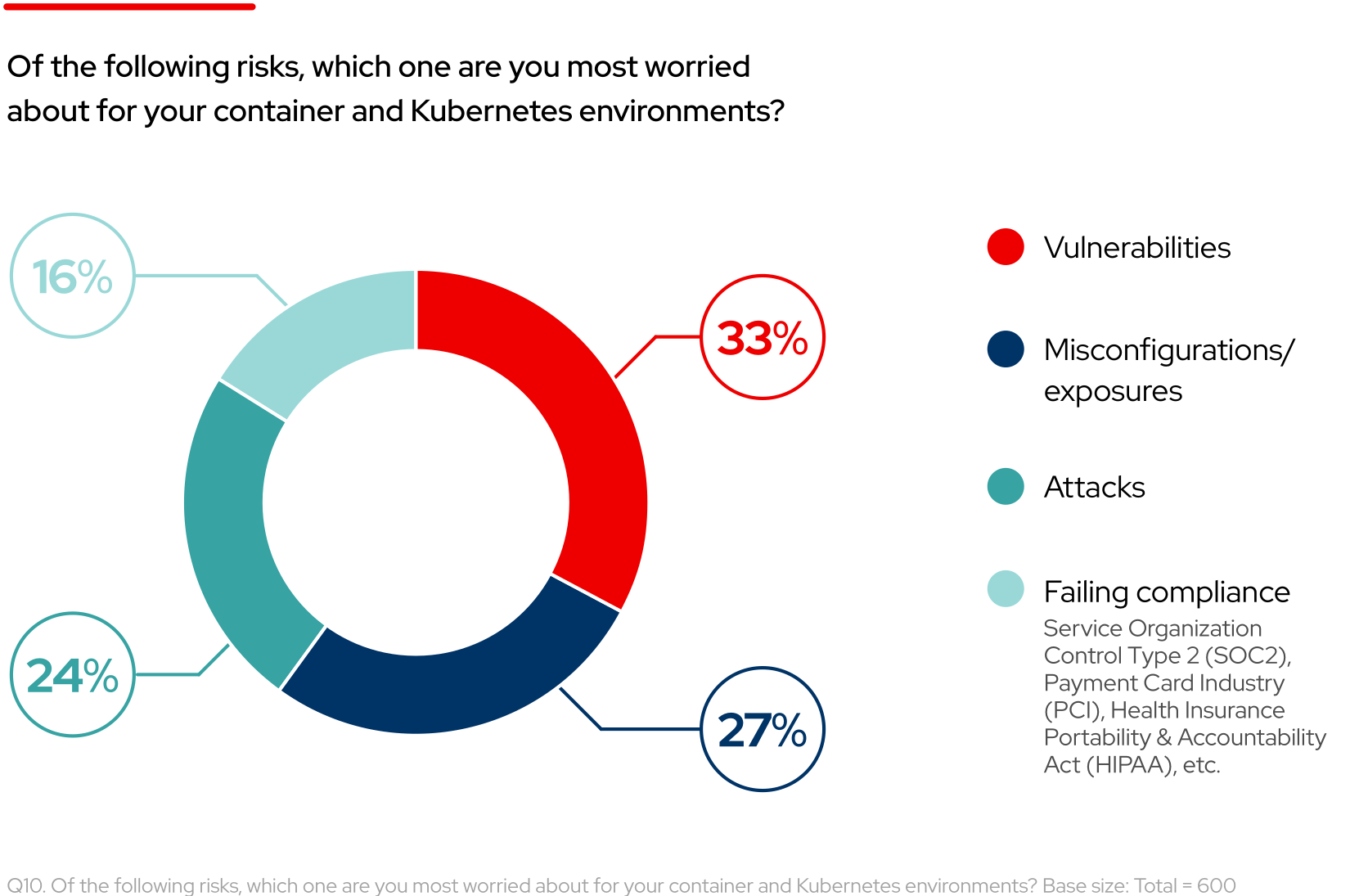
60% of respondents worry about vulnerabilities, misconfigurations and exposures in their container and Kubernetes environments
Mitigating vulnerabilities in complex, dynamic Kubernetes and container environments can be challenging and difficult to isolate. Because containers share host resources like operating system kernels, a single container vulnerability can affect multiple containers. Additionally, a vulnerability in a host itself can affect all containers deployed on the system. Respondents are clearly aware of this challenge, as 33% are most worried about vulnerabilities in their container and Kubernetes environment.
A top concern for 27% of respondents, incorrectly configured components—including base images, libraries, and dependencies—can introduce critical security issues across entire environments. If not properly validated and maintained, these components can serve as potential attack points and compromise the integrity and confidentiality of critical applications and sensitive data.
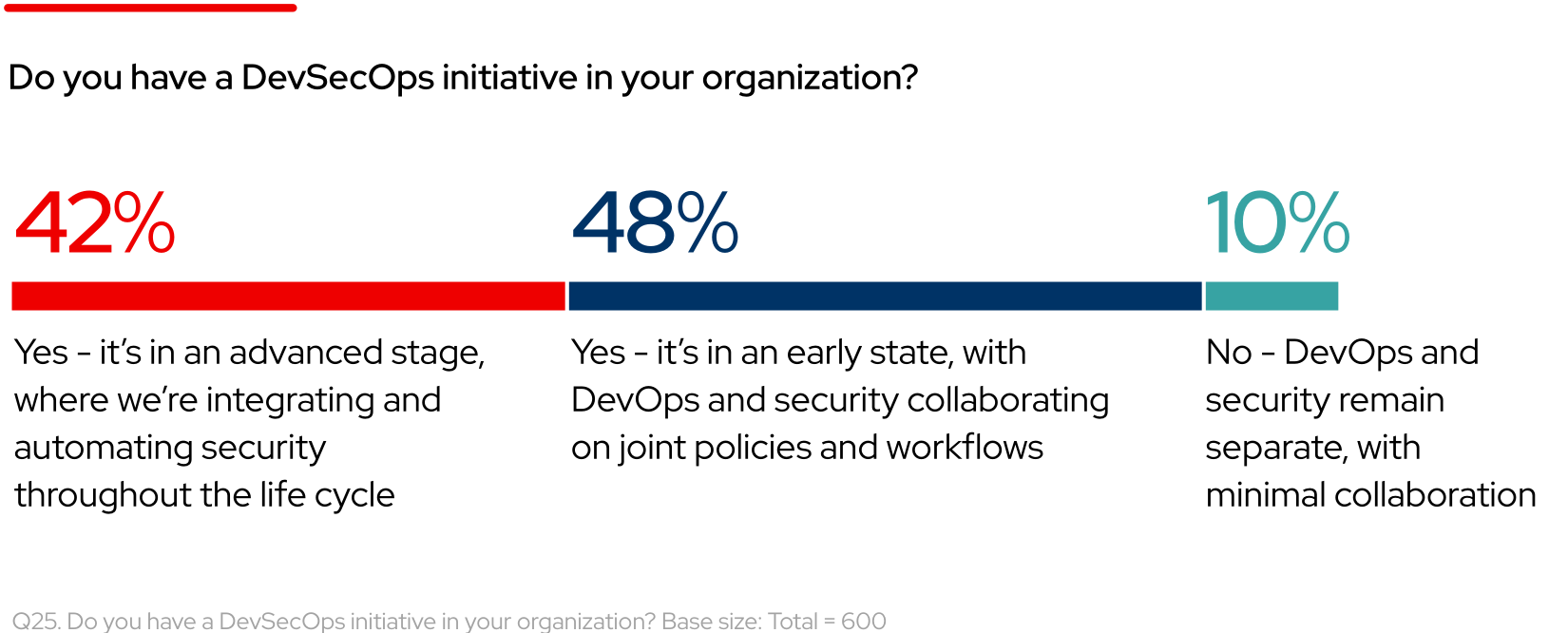
42% of respondents have a DevSecOps initiative in an advanced stage within their organization
At the same time, 48% report that their organization understands the value of DevSecOps and is in the early stages of adoption, with development, operations, and security teams collaborating on joint policies and workflows. This is a significant increase from 2023, when only 39% of respondents were at this stage. For the remaining 10% of organizations, separate DevOps and security teams may lead to reactive processes that only address vulnerabilities at deployment or runtime, resulting in decreased efficiency, speed, and software quality, along with slower application delivery.
Read the full report for tips on enhancing your container and Kubernetes security
Cloud-native technologies are changing the way organizations develop, deploy, and scale applications. The inherent scalability, agility, and flexibility of cloud infrastructure lets businesses speed time to market, improve efficiency, and enhance innovation.
However, as cyberattacks become increasingly sophisticated, robust security measures are key to safeguarding sensitive data, protecting against breaches, and complying with regulatory standards across hybrid cloud environments.
In response, many IT organizations are investing in advanced security platforms and implementing collaborative, security-focused processes to protect critical systems, workloads, and data.