Overview
Red Hat's product security response team has handled vulnerability management for over 20 years. Red Hat doesn't just handle vulnerabilities; we work with the whole of the product supply chain to ensure security is embedded at every step before and during release. Product Security uses processes and plans that result in the best security practices and standards to protect our customers, contributors, and partners from digital security threats.
Security in engineering standards
Red Hat's internal technical standard, Secure Software Management Lifecycle (SSML), provides a clear set of engineering requirements that enables Red Hat software or services to meet security industry regulations and standards. The SSML:
Aligns with the Secure Software Development Framework (SSDF) and Supply chain Levels for Software Artifacts (SLSA), clearly conveying the Red Hat standards that apply to each SSDF or SLSA task.
Includes references to industry-recognized and known good security development practices and controls to better codify the expectations for standards and evidence.
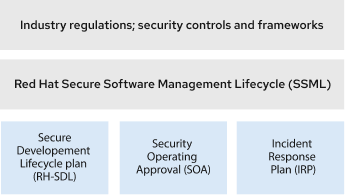
Red Hat implementation guidance based on the SSML must be followed by all Red Hat software or services:
Red Hat's Secure Development Lifecycle (SDL) clearly defines for engineering how the SSML's secure-development standards should be met: what needs to be done, by whom, and how. The RH-SDL's set of practices ensures that security is integrated into every stage of the software development process.
The Security Operating Approval (SOA) is the review of Red Hat infrastructure and affiliated tooling involved in Red Hat productization pipelines to measure adherence to security controls, policies, and procedures. This ensures the curation, creation, and delivery of quality products and services.
- The Vulnerability and Incident Response Plan (IRP) proactively prepares Red Hat via Product Security to effectively handle security incidents. The IRP ensures security issues are handled in a timely manner as they relate to Red Hat Products and services.
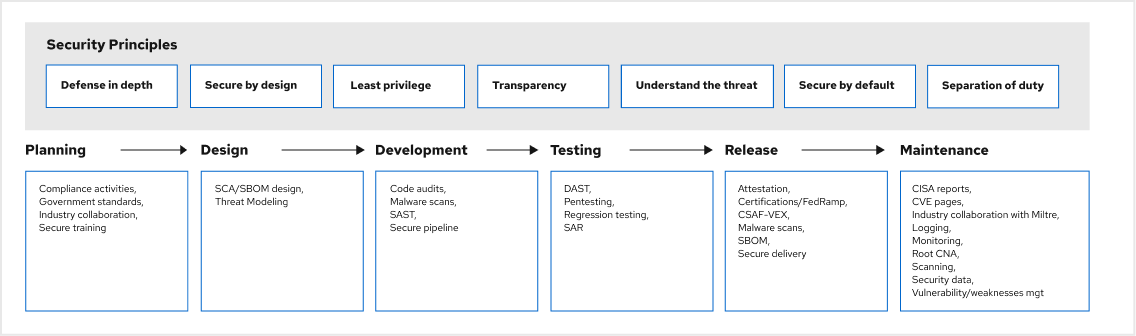
Security in the product pathway
At Red Hat, security is applied in every phase; we see security as a process, not a product. The diagram below provides a high-level view of Red Hat's security controls in the product pathway.