This is a guest post written by Jim Armstrong of Snyk.
Containers are the building blocks of modern applications, so securing them is crucial for today’s enterprises. Scanning images directly within your container registry is a critical step in the path to ensure your containerized applications are secure across different code repositories and development teams.
Red Hat Quay is a popular choice for creating a secure, private container registry that can be installed on your own infrastructure or run as a service on Quay.io. And now, Snyk Container’s new integration with Quay helps developers fix vulnerabilities in images stored within Quay, no matter which deployment option you choose.
In this post, we will walk through setting up Quay within Snyk for container scanning. More specifically, we will cover how to connect Quay to Snyk, the options for processing images, and what to expect from the results.
Getting Started With Red Hat Quay
Snyk’s Red Hat Quay integration can be initiated directly within the Snyk console. If you do not already have a Snyk account, you can sign up for a free account today.
From the Integrations tab, select Quay under the Container Registries section to begin the connection process.
You will then need to enter your Quay credentials to give Snyk permission to pull images from the registry. There is also an option to detect application vulnerabilities, extending the scanning to open source dependency issues as well. Snyk will then use your credentials to test the connection to Quay.
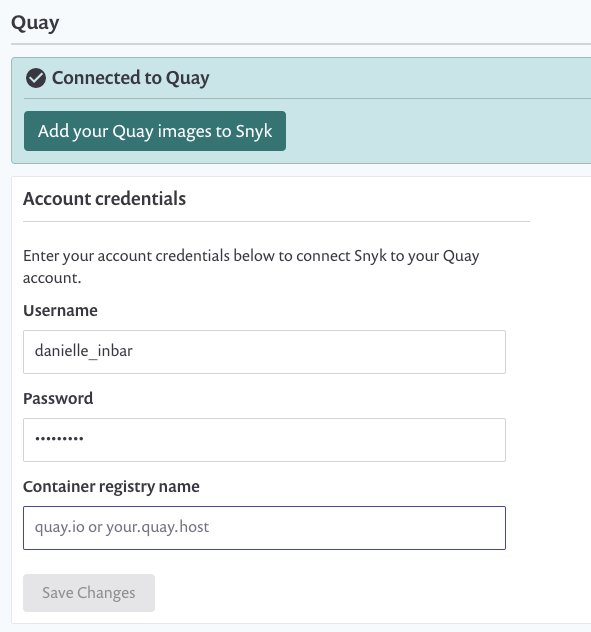
Once you have connected Snyk with Quay, you can select the images you want to scan from the Quay registry. You can also choose to import entire repositories into Snyk. These images will be added to the queue for scanning.
Snyk Deployment Options for Scanning Container Images
For most Snyk users, the integration above is all you need. Scanning is handled by Snyk, so there is no additional processing or overhead in Quay, and you can scan any image from your public or private Quay registry. Snyk does not store your images, only the metadata required to show your results and keep you informed if there are any new vulnerabilities discovered that affect your image.
However, some prefer to keep all scanning functionality within their own network boundaries, and you can use Snyk Container in these scenarios as well. For companies running a private Quay registry concerned with releasing image information to Snyk, you can use an on-premise broker service to scan images locally. Snyk can still track the image dependency information and monitor the image over time, but the image scanning is performed on your network.
You can set up the SaaS option of our Quay integration with any Snyk plan, but the brokered service requires a Business or Enterprise plan. You will also need to install the Snyk broker client and agent, which are delivered as two container images. The broker client and agent will have limited access to your private container registry and only send the scan results back to the Snyk backend.

Analyzing the Results
Once the container images have been processed, the scan results show up in the Snyk interface under Projects. The key security areas Snyk container scanning focuses on are base images and third-party dependencies.
Snyk will provide alternative base image recommendations to dramatically reduce the number of vulnerabilities in your containers with a single change. For popular Docker images, there are often multiple alternative images available, but Snyk organizes them into minor, major, or alternative upgrades. This allows you to strike the right balance between an easier change and fewer vulnerabilities.

Within the Snyk console, you can also review vulnerability data that’s organized by priority score, which takes into account the CVSS score, known exploits, and many other characteristics. You can also filter the results to only show high severity issues, vulnerabilities that have a fix, or other options to help prioritize remediation.

Using this simple integration, Snyk has made it as easy as possible to surface and remediate vulnerabilities in container images stored within Quay. That way, your organization can continue to improve its security posture without facing developer friction.
About Snyk, a Red Hat-Certified Partner
Snyk is a developer-first cloud native application security company that offers tight integrations into existing developer workflows, source control, and CI/CD pipelines to enable efficient security workflows and help customers reduce mean-time-to-fix.
Snyk has also been recognized as a Red Hat-certified Partner and Red Hat Marketplace seller, keeping customers at ease about Snyk’s interoperability with Red Hat’s hybrid cloud portfolio, and in some cases, helping customers centralize their billing mechanisms by purchasing Snyk software using their allocated Red Hat budget.
Want to learn more about Quay container scanning? See our full documentation to get started.
About the author
Red Hatter since 2018, technology historian and founder of The Museum of Art and Digital Entertainment. Two decades of journalism mixed with technology expertise, storytelling and oodles of computing experience from inception to ewaste recycling. I have taught or had my work used in classes at USF, SFSU, AAU, UC Law Hastings and Harvard Law.
I have worked with the EFF, Stanford, MIT, and Archive.org to brief the US Copyright Office and change US copyright law. We won multiple exemptions to the DMCA, accepted and implemented by the Librarian of Congress. My writings have appeared in Wired, Bloomberg, Make Magazine, SD Times, The Austin American Statesman, The Atlanta Journal Constitution and many other outlets.
I have been written about by the Wall Street Journal, The Washington Post, Wired and The Atlantic. I have been called "The Gertrude Stein of Video Games," an honor I accept, as I live less than a mile from her childhood home in Oakland, CA. I was project lead on the first successful institutional preservation and rebooting of the first massively multiplayer game, Habitat, for the C64, from 1986: https://neohabitat.org . I've consulted and collaborated with the NY MOMA, the Oakland Museum of California, Cisco, Semtech, Twilio, Game Developers Conference, NGNX, the Anti-Defamation League, the Library of Congress and the Oakland Public Library System on projects, contracts, and exhibitions.
More like this
How llm-d brings critical resource optimization with SoftBank’s AI-RAN orchestrator
MCP security: Implementing robust authentication and authorization
Post-quantum Cryptography | Compiler
Understanding AI Security Frameworks | Compiler
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Virtualization
The future of enterprise virtualization for your workloads on-premise or across clouds
