This is the third post in a series of blogs looking at cybersecurity focusing on Critical National Infrastructure (CNI) organizations. This post identifies where Red Hat can help organizations reduce their risk using their technology, training, and services.
- Enterprise security challenges for CNI organizations: Overview
- Enterprise security challenges for CNI organizations: People and processes
- Enterprise security challenges for CNI organizations: Technical solutions
How can Red Hat help ?
Red Hat provides trusted open source software that helps organizations implement security, in a layered approach, across the infrastructure and application stack and lifecycle to better secure workloads on-premise, in the cloud, or on the edge. Specifically, we will look at Red Hat’s newest approaches to addressing emerging IT security challenges for CNI. At Summit 2023, Red Hat announced, as a service preview, a number of new cloud service offerings under the umbrella of the Red Hat Trusted Software Supply Chain.
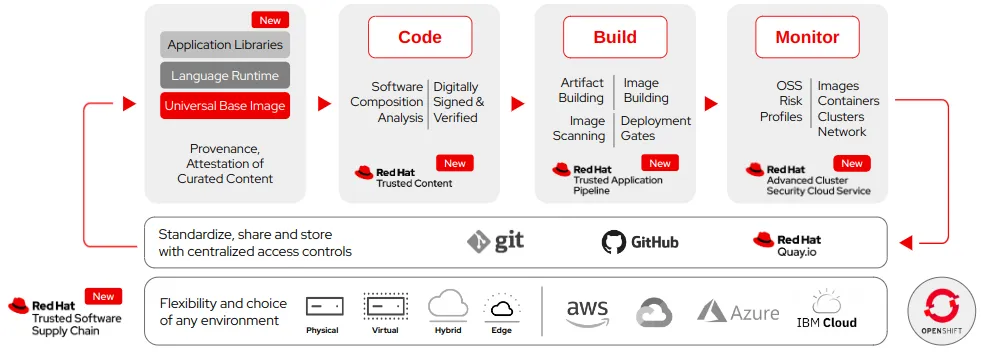
It comprises a number of software security solutions and cloud services, including:
Red Hat Trusted Content
Red Hat Trusted Content, a cloud service preview offering that’s a part of Red Hat Trusted Software Supply Chain, helps to identify transitive dependencies and security vulnerabilities, enabling you to better detect and mitigate known software risks and vulnerability exposures earlier in the development process. This helps remove manual toil and avoid costly rework.
By implementing trusted software supply chain technologies, you can follow through on IT security best practices without incurring additional work by:
- Reducing development times through access to a trusted content repository that lets your developers choose reusable components delivered with provenance, signatures, and attestation.
- More quickly identifying transitive dependencies and potential vulnerabilities in the code source by running real-time software composition analysis (SCA) directly from your local IDE.
- More readily finding Vulnerability Exploitability eXchange (VEXs) and Software Bill of Materials (SBOMs) for Red Hat products and packages.
- Gaining greater insights about dependencies and vulnerabilities by uploading your own SBOM for analysis.
Red Hat Trusted Application Pipeline
Available as a cloud service preview, Red Hat Trusted Application Pipeline helps enterprises successfully adopt DevSecOps practices, consume open source code and third-party dependencies safely, and build security into the software development life cycle. We integrate security guardrails at every phase of a DevSecOps framework to offer teams accelerated time to value for a trusted software supply chain.
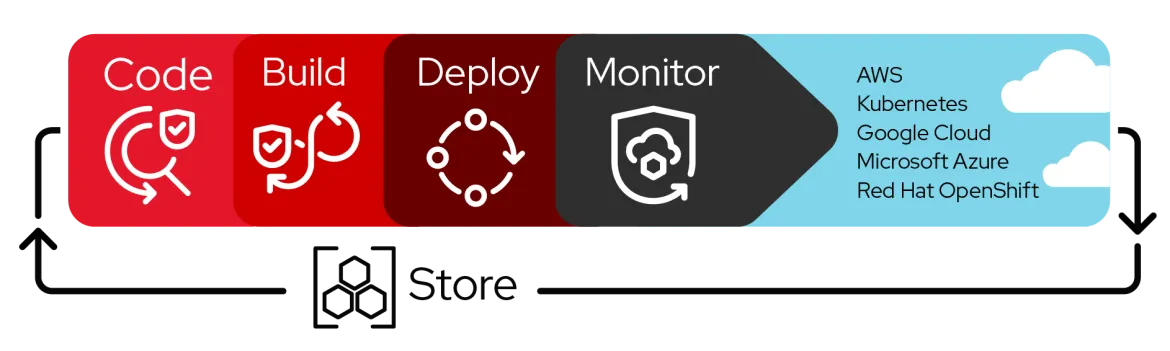
Red Hat Trusted Application Pipeline allows teams to build applications using automated, security-focused CI/CD workflows with continuous images scanning, provenance checks, attestations, and auto-generation of SBOMs that comply with industry standards and regulations. IT organizations can use Red Hat Trusted Application Pipeline to build an accurate inventory of their software components, while improving their development efficiency and productivity.
Powered by Red Hat OpenShift, Red Hat Trusted Software Supply Chain brings together trusted cloud services and prescriptive workflows. AppDev leaders can now release applications in less time while meeting security requirements. This means businesses improve their supply chain resiliency to keep pace with their innovation cycles. They keep and grow their user trust to avoid reputational damage, customer churn, and revenue loss.
Event-Driven Ansible
Outside of software supply chain security, automation provides a powerful starting point for an IT security strategy. Event-driven automation is the next step in the journey to end-to-end automation. It answers the need to connect intelligence, analytics, and service requests for an environment to automate actions so that activities can take place in a single motion. This model is ideal for high-volume, routine tasks as well as ITSM actions and more.
Event-Driven Ansible connects sources of events with corresponding actions using rules. Its decision-making capabilities receive an event from a monitoring tool and trigger the required action. Ansible Rulebooks define the source of the event and explain the action to take — in the form of “if-this-then-that” instructions — when the event is encountered. Ansible Rulebooks
map event conditions to an action, like running a playbook or directly executing a module.
Red Hat Ansible Automation Platform can play a significant role in addressing cybersecurity threats by providing:
- Real-time monitoring: Connect Ansible Automation Platform up to existing monitoring security tools to automate end-to-end monitoring, such as triggering conditional events and defining actions that can automatically respond
- Intrusion detection and response: Automate tasks like isolating compromised systems, applying patches, and notifying security teams
- Vulnerability management: Schedule regular scans and automatically remediate any identified vulnerabilities
- Security compliance: Simplify system hardening and compliance and automatically respond to any drift away from the desired state
Event-Driven Ansible is comprised of three main components:
Sources
These define which event source plugins will be used. Commonly these are monitoring tools, but they can also be custom integrations you create to any event source important to you. These source plugins are created by partners, the Ansible community, Red Hat, or you. There are some common source plugins that are available already, including webhooks, Kafka, Azure service bus, file watch, url_check, Prometheus alertmanager, and others, including partner-specific plugins.
Rules
These define conditionals that will be matched from the event source. Should the condition be met, an action can be triggered.
Actions
An action triggers what needs to happen should a condition be met. Some of the current actions include running a playbook, running a module, setting a fact, posting an event, or debugging. The rules will look for certain situations where specific conditions are met and then kick off an action to address the event for which the decision system has identified a required action.
Red Hat often recommends a "start small, think big" approach to automation, and Event-Driven Ansible is no exception. If you are learning how Event-Driven Ansible works, we suggest some simple use cases, such as gathering facts. From there you can grow your use of this automation to more sophisticated automated actions and broader applications across your operation — from network to infrastructure to cloud and DevSecOps, and more.
About the author
Chris Jenkins is an experienced EMEA based Chief Technologist who provides a broad range of technical and and non-technical skills to enterprise customers.
More like this
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Original shows
Entertaining stories from the makers and leaders in enterprise tech
Products
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Cloud services
- See all products
Tools
- Training and certification
- My account
- Customer support
- Developer resources
- Find a partner
- Red Hat Ecosystem Catalog
- Red Hat value calculator
- Documentation
Try, buy, & sell
Communicate
About Red Hat
We’re the world’s leading provider of enterprise open source solutions—including Linux, cloud, container, and Kubernetes. We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge.
Select a language
Red Hat legal and privacy links
- About Red Hat
- Jobs
- Events
- Locations
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit

