The Quay team is thrilled to introduce a suite of new features in the 3.12 release aimed at enhancing security, streamlining efficiency and aligning with the latest container industry standards.
Significant updates include:
Features
- API token ownership transfer
- Image expiration alerts
- Default auto-pruning policy
- Open Container Initiative referrers & pagination compliance
General improvements
- Quay logging exception
- Repository list API efficiency
- Global read-only superuser (increased scope)
API token ownership transfer
Red Hat Quay 3.12 introduces API token ownership transfer which allows for the provisioning of API tokens to ensure appropriate usage of tokens by designated members of your organization. This change helps enhance security and auditing accuracy by allowing flexible API token allocation. Organization owners can more easily prevent unauthorized access and increase access management control, which can be especially useful in restricted security-conscious environments. This feature will enable setting ownership during API token creation, with accurate audit log tracking, thus ensuring permission controls keep up with your organization’s dynamic needs. Check out the demo of how this works here.
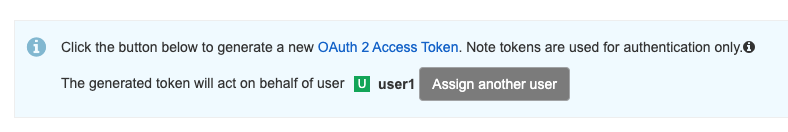
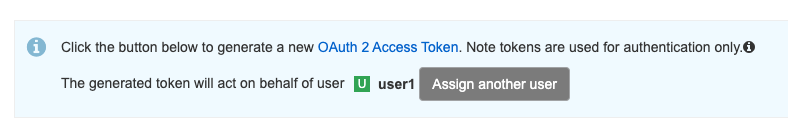
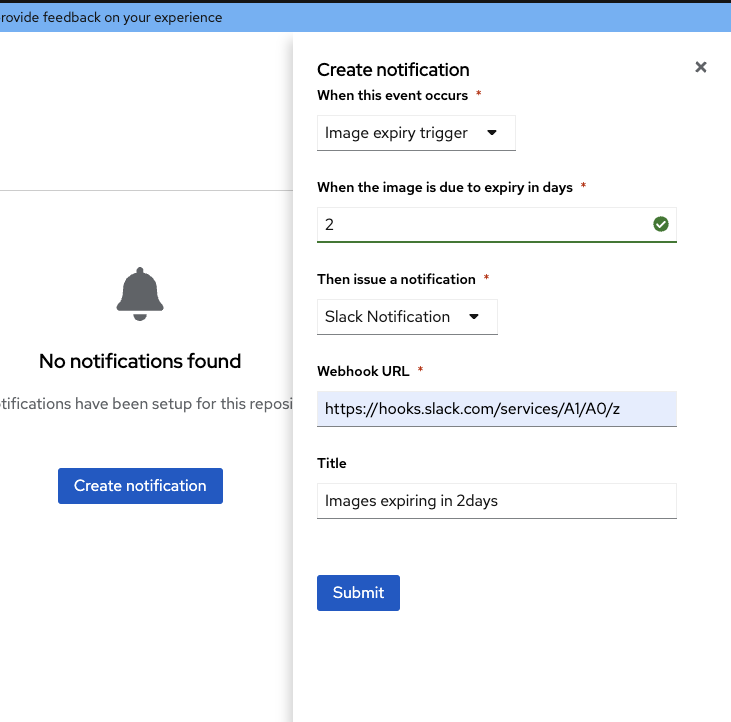
Image expiration alerts
In version 3.12, alerts will notify users before an image expires to help prevent unexpected pull failures. This proactive notification system helps ensure that critical images are available when needed in a non-interruptive manner. This feature will make it easier to manage image lifecycles through individual tag and image expiration notifications. Check out the demo of how this works here.
Default global auto-pruning policy
Quay 3.12 aims to build on the previous delivery of granular repository-level auto-pruning with global default auto-pruning policy. Through automatic management of old or unused images across the entire registry, users can ensure that outdated images are pruned regularly, keeping storage costs more predictable and manageable. We will continue to gradually build on auto pruning capabilities to fit our users’ needs. Check out the demo of how this works here.
Optimizing for OCI compliance
OCI 1.1 Referrers support
We are implementing the OCI spec 1.1, the largest change to the registry API since the initial release of OCI distribution spec 1.0. This includes support for artifact manifests, reference types, and the referrers API. Check out the demo of how this works here.
OCI referrers enable trusted supply security systems like Konflux to produce and link artifacts such as signatures, SBOMs, and attestations to container images. Tools like cosign and skopeo offer first-class support for these enhancements, efficiently linking or finding these artifacts. These improvements will enable Quay’s support for Konflux, a project aimed at enhancing the security and efficiency of build systems by leveraging SigStore, an open-source project that provides tools for signing, verifying, and protecting software supply chains. Stay tuned for a dedicated blog on the OCI referrers work and partnership updates.
OCI content discovery compliance
This improvement is aimed to enable Quay compliance with the most current OCI standards. We recognize it is essential for seamless integration with other OCI-compliant tools and services, enhancing your overall user experience. The OCI specification addresses how clients process responses when asking the registry for all image tags in a given repository. In the past, the pagination parameters defined by the spec for this use case were not supported by Quay but instead Quay sent a URL back to the client where to go for the next set of tags. Since such a response header is optional, by the spec, some registry clients had to implement special behavior for Quay and Quay.io.
With this update, Red Hat Quay and Quay.io are now supporting tag listing according the OCI specification, which ensures compatibility across the ecosystem of container registry clients. If you are developing an OCI compatible registry client, we would like you to be aware of a recent change in the OCI spec regarding tag list pagination: Clients will now have to respect a Link response header in case the amount of tags returned is lower than the requested amount.
Additional improvements
- Quay logging exception: We addressed an issue where Quay would raise a long error message in the container logs when attempting to cache large vulnerability reports if the value exceeded a specific size. This fix prevents log-space from filling up quickly due to these error messages.
- Repository list API efficiency: We improved the repository list API to efficiently use database requests when quota is enabled, which is essential for larger Quay deployments.
- Global read-only superuser feature has increased in scope, now providing comprehensive read access across all entities and API endpoints in Quay without write permissions. This is crucial for security auditing, allowing superusers to monitor all activities within Quay without the risk of unauthorized changes. Users can now ensure thorough oversight while maintaining the integrity of their registry.
- Support for Splunk HTTP event collectors as storage for Quay audit log events, in addition to the existing Splunk Enterprise support
- Efficient audit logging failures to avoid that requests to the registry fail if audit events could not be stored, which is useful when an external service is used for audit log storage (controlled via the ALLOW_WITHOUT_STRICT_LOGGING configuration directive).
Quay’s future enhancements
We plan to continue adopting OCI features, improve image lifecycle at scale, and support software supply chain tooling that best optimize your containerization workflows. Additionally, we plan to revisit the UI work with the aim to default to the new UI experience in 2024+.
Overall, these updates reflect our continued commitment to provide a security-forward, efficient and compliant container registry. By enhancing API token management, OCI standards compliance, improving image lifecycle automation, and including comprehensive security auditing, we are making Quay easier to integrate in a modern software supply chain and user-friendly. Stay tuned for demos and more updates on features as we work towards a fully optimized and user-friendly experience in the year ahead. Learn more about Red Hat Quay and how these new features can benefit your organization!
As always, leave us feedback by opening up a ticket, reaching out via email (quay-sig@googlegroups.com) and/or chiming in our UI survey. We look forward to improving Quay’s product experience with your needs in mind!
About the author
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Original shows
Entertaining stories from the makers and leaders in enterprise tech
Products
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Cloud services
- See all products
Tools
- Training and certification
- My account
- Customer support
- Developer resources
- Find a partner
- Red Hat Ecosystem Catalog
- Red Hat value calculator
- Documentation
Try, buy, & sell
Communicate
About Red Hat
We’re the world’s leading provider of enterprise open source solutions—including Linux, cloud, container, and Kubernetes. We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge.
Select a language
Red Hat legal and privacy links
- About Red Hat
- Jobs
- Events
- Locations
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit

