We're thrilled to unveil our latest release: Red Hat Advanced Cluster Security for Kubernetes 4.5. Following last year's 4.0 release, our team has been hard at work enhancing the essential workflows that businesses depend upon to safeguard their Kubernetes and container environments. The 4.5 release marks a significant milestone for our security solution, and coincides with our SaaS offering, Red Hat Advanced Cluster Security Cloud Service’s graduation from limited availability to general availability.
The 4.5 release includes the general availability of key new enhancements as well as significant feature updates to core functionality. These updates include:
- Vulnerability Management 2.0 general availability (GA)
- Scanner V4 general availability (GA)
- Compliance enhancements
- Hardening Red Hat Advanced Cluster Security integrations
Additional Red Hat Advanced Cluster Security platform updates include:
- Red Hat Advanced Cluster Security on Red Hat OpenShift Service on AWS (ROSA) hosted control planes (HCP)
- Built-in email notifier in Red Hat Advanced Cluster Security Cloud Service
- Extended Github action support in roxctl
As always, you can find more information about the release in the Red Hat Advanced Cluster Security documentation and release notes, and you can explore the new SaaS version of Red Hat Advanced Cluster Security through the 60-day, no-cost trial.
Vulnerability management 2.0 (GA)
The new Red Hat Advanced Cluster Security vulnerability management 2.0 dashboard enhances the vulnerability management workflow. With Red Hat Advanced Cluster Security 4.5, this dashboard is now generally available and integrates exception management, vulnerability reporting, and the workload CVEs page into the vulnerability management 2.0 framework, while retaining the original dashboard during the transition period.
The graduation of the vulnerability management 2.0 dashboard signifies the consolidation of all underlying dashboards into a unified vulnerability management dashboard.
Key features in vulnerability management 2.0 include:
- Platform and node CVE workflows tab, providing identical functionality as the previous vulnerability management dashboard.
- Enhanced filtering capabilities have been implemented, allowing for the prioritization of remediation by focusing on fixable critical and important CVEs.
- Administrators can discover CVEs and prioritize remediation efforts through namespace views to help manage multi-tenant environments.
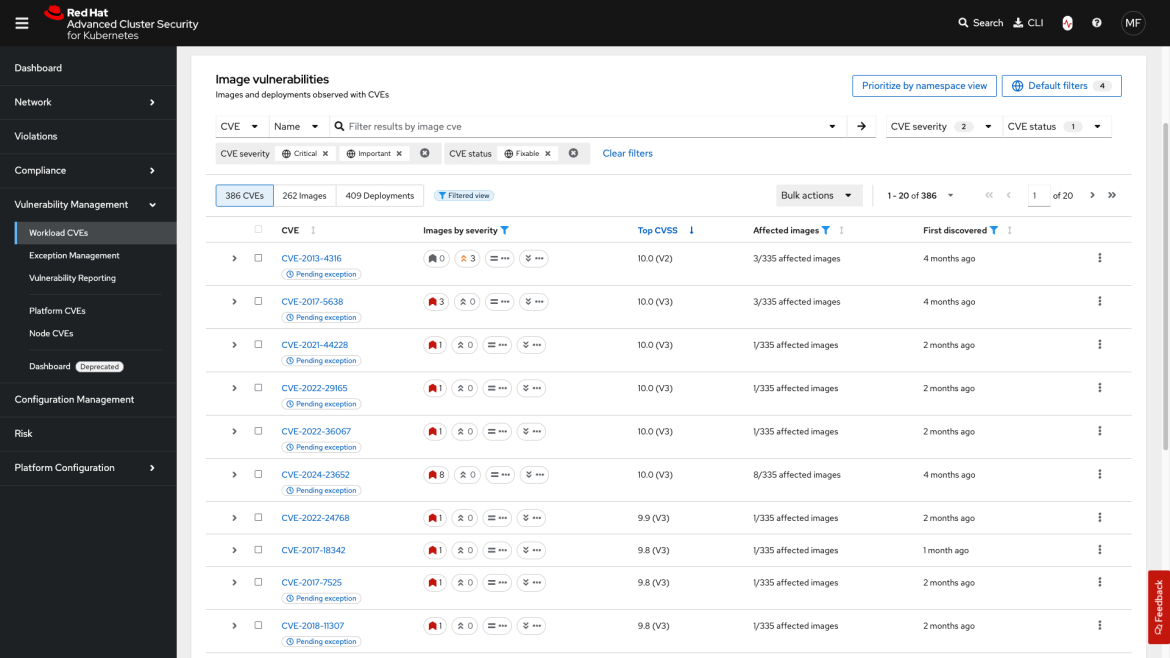
This updated dashboard aims to enhance user capability by identifying vulnerabilities and their specific locations with increased speed and efficiency. It also provides clearer differentiation between CVEs associated with nodes, platforms and workloads.
Vulnerability scanner V4 general availability (GA)
In version 4.4, we introduced a substantial update to core vulnerability management workflows with the release of Red Hat Advanced Cluster Security scanner V4 in tech preview (TP). Red Hat Advanced Cluster Security scanner V4 merges the previous StackRox scanner with the upstream Clair V4 scanner from Red Hat Quay, delivering consistent scan results across offerings, broader language and operating system support, and access to an expanded vulnerability database built from the following sources: Red Hat’s vulnerability feed, osv.dev, NVD and more.
Red Hat Advanced Cluster Security scanner V4 is now generally available and fully supported in version 4.5. To ensure a seamless transition, users must explicitly enable it via the Red Hat Advanced Cluster Security Operator or Helm chart deployment options.
For more information about enabling the Red Hat Advanced Cluster Security scanner V4, see:
- “Scanner settings” in installing RHACS on Red Hat OpenShift.
- “RHACS Scanner V4” in installing RHACS on other platforms.
Compliance updates
Compliance Operator and Red Hat Advanced Cluster Security are tightly integrated to help enable customers to meet their OpenShift platform and node compliance requirements. The integration allows OpenShift users to monitor the technical controls from CIS, NERC-CIP, NIST-800-53, DISA STIG, or PCI-DSS compliance benchmarks that are critical to your operations.
The 4.5 release introduces enhanced integration with the OpenShift Compliance Operator. In Red Hat Advanced Cluster Security 4.5, you can:
- Generate weekly, daily, and hourly compliance reports for multiple OpenShift clusters simultaneously.
- Summarize compliance results for a specific profile across clusters.
- Streamline reporting workflows for compliance auditors with benchmarks and controls.
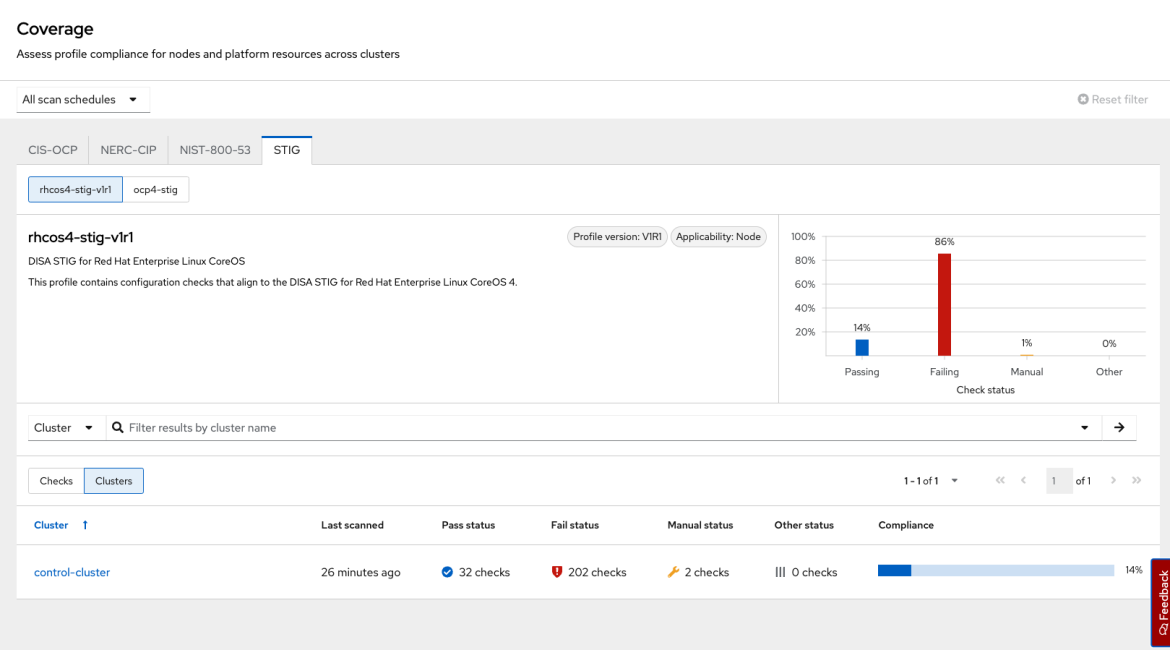
These new features and updates are under the Compliance tab in your RHACS dashboard. For more information, see the RHACS documentation.
Bring your own public key infrastructure with Cosign signature verification and enforcement
To enhance supply chain security, ensure provenance and implement SLSA-focused guardrails, Red Hat Advanced Cluster Security now supports the integration of custom public key infrastructure (PKI) with Cosign signature verification.
Red Hat Advanced Cluster Security has supported the Cosign project and integration for several years, offering flexible policies and seamless integration with Cosign. Red Hat Advanced Cluster Security 4.5 has added support for verifying Cosign signatures that are backed by an organization’s existing PKI infrastructure.
Red Hat Advanced Cluster Security incorporates these fundamental updates through its existing Cosign integration and provides customers with policy functionality, notifications and enforcement mechanisms during deployment to bolster provenance, further helping organizations meet their provenance objectives.
Try out the new updates, at no cost, for 60 days with Red Hat Advanced Cluster Security Cloud Service
The Red Hat Advanced Cluster Security team is continuously identifying how we can improve the offering to fit our users’ unique needs. If you want to check out these features yourself, sign up for our 60-day, no-cost trial today!
About the author
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Original shows
Entertaining stories from the makers and leaders in enterprise tech
Products
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Cloud services
- See all products
Tools
- Training and certification
- My account
- Customer support
- Developer resources
- Find a partner
- Red Hat Ecosystem Catalog
- Red Hat value calculator
- Documentation
Try, buy, & sell
Communicate
About Red Hat
We’re the world’s leading provider of enterprise open source solutions—including Linux, cloud, container, and Kubernetes. We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge.
Select a language
Red Hat legal and privacy links
- About Red Hat
- Jobs
- Events
- Locations
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit

