In the dynamic world of container orchestration, Kubernetes has emerged as the de facto standard for managing containerized applications. However, as organizations increasingly rely on Kubernetes to power their applications, the need for robust security solutions becomes paramount.
We recognize this necessity and offer a powerful toolset to enhance Kubernetes security: Red Hat Advanced Cluster Security for Kubernetes (RHACS). In this blog post, we will explore how this solution helps deliver greater security to Kubernetes environments and provide context around the Compliance Operator for Red Hat OpenShift, a key component of how Red Hat approaches cloud-native security.
These demands are extremely important as our public sector customers continue to adopt Kubernetes-based deployments to support their missions. DISA has even released a STIG for OpenShift that further enhances the ability for OpenShift clusters to be deployed for these types of missions.
Bolstering Kubernetes environments with Red Hat Advanced Cluster Security
Red Hat Advanced Cluster Security is a comprehensive Kubernetes-native security platform designed to protect containerized applications throughout their lifecycle. Let's delve into the key features and capabilities that make this an invaluable tool for Kubernetes security:
Vulnerability management: Advanced Cluster Security provides automated vulnerability scanning for container images. It identifies and prioritizes vulnerabilities in your images and provides recommendations for remediation. This proactive approach verifies that you are not deploying containers with known vulnerabilities, reducing the attack surface.
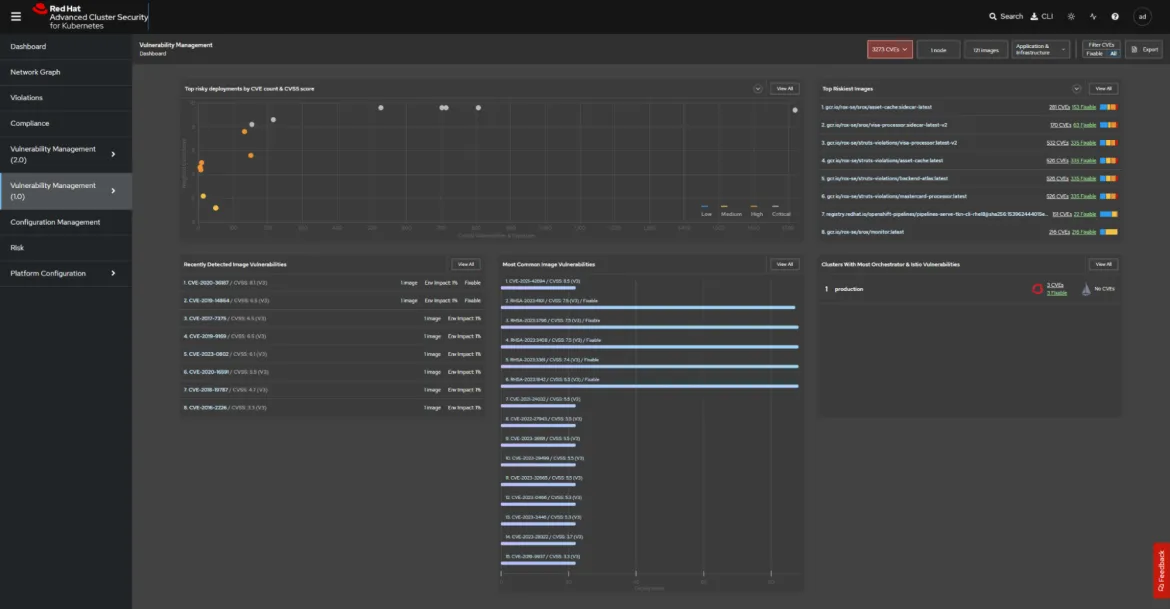
Runtime threat detection: With real-time threat detection, Red Hat Advanced Cluster Security constantly monitors your Kubernetes environment for suspicious activities and deviations from the expected behavior. It can identify and more quickly respond to runtime threats such as privilege escalations, lateral movement, and more.
Network segmentation: The solution helps enforce network segmentation policies within your Kubernetes clusters. This limits communication between containers, reducing the risk of lateral movement by attackers.
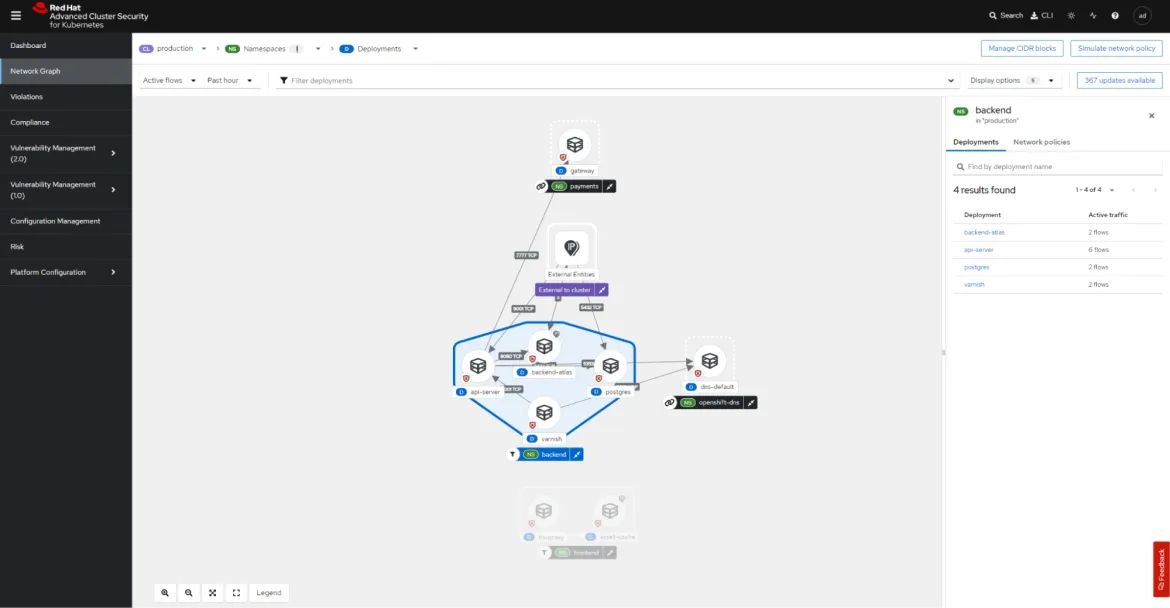
Policy enforcement: Advanced Cluster Security enables you to define and enforce security policies that align with industry best practices and regulatory requirements. Policies can cover a wide range of aspects, from container configurations to network policies. This also helps confirm that only compliant workloads are deployed and running on the cluster.
Incident response: The included incident response capabilities allow security teams to investigate and remediate security incidents more swiftly. It logs and provides visibility into runtime activities, helping security teams understand and respond to threats more effectively.
Compliance and reporting: Red Hat Advanced Cluster Security offers compliance scanning against industry standards and benchmarks, such as CIS Kubernetes Benchmark and NIST. It generates reports to demonstrate compliance to auditors and stakeholders. The reports will help to answer some of the manual questions that often happen around STIG requirements. In addition to reporting visualization, these dashboards provide quick references for the state of your security posture.
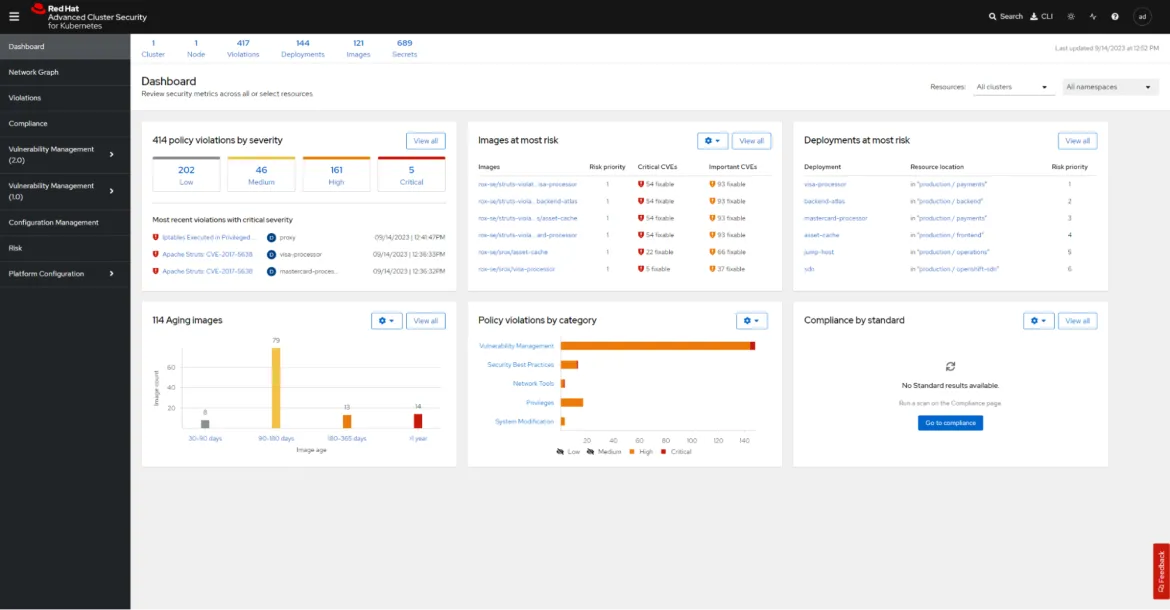
The Compliance Operator for Red Hat OpenShift
While Red Hat Advanced Cluster Security offers a robust set of features for Kubernetes security, OpenShift users can further enhance their compliance posture with the Compliance Operator. OpenShift integrates the Compliance Operator to provide a more unified approach to IT security and compliance. If you have OpenShift, you already have access to the Compliance Operator, which will assess your clusters against a variety of popular benchmarks, from DISA STIG to PCI-DSS to common hardening guidelines line CIS.
Here's how the Compliance Operator complements Advanced Cluster Security within OpenShift:
Policy-as-code: The Compliance Operator allows you to define and enforce compliance policies as code using Kubernetes CustomResourceDefinitions (CRDs). The Compliance Operator refers to these as Rules. This means you can express your security and compliance requirements in a way that is native to Kubernetes, helping to simplify policy management.
Automated scanning: The Compliance Operator automates the scanning of OpenShift clusters against various compliance standards, including CIS benchmarks, STIG requirements, and custom policies. It continuously assesses your cluster's compliance status and provides detailed reports.
RHEL compliance for OpenShift: The Compliance Operator brings the compliance experience from Red Hat Enterprise Linux to OpenShift through a vast library of rules. You can leverage these rules through default profiles available through the operator, or in your own custom profiles that allow you to extend existing profiles or mix-and-match rules to fit your unique compliance requirements.
Alerting and remediation: When non-compliance is detected, the Compliance Operator can trigger alerts and notifications. Additionally, it offers remediations to help you bring your cluster back into compliance more quickly.
Historical data and auditing: The Compliance Operator maintains a historical record of compliance scans and remediation actions that can be reviewed by external tooling, providing a comprehensive audit trail for compliance-related activities.
Integration with RHACS: When integrated with Advanced Cluster Security, the Compliance Operator offers a holistic approach to Kubernetes security and compliance. Red Hat Advanced Cluster Security handles runtime security, while the Compliance Operator enforces cluster adherence to compliance standards.
Automated hardening: The Compliance Operator is capable of hardening OpenShift in an automated manner. This automation includes multiple profiles that are applicable to CIS, STIG, NIST and other profiles.
Installation of the Compliance Operator is as simple as visiting the Operator Hub within OpenShift and searching for "Compliance Operator". This will allow you to walk through the installation of the operator and start hardening your OpenShift cluster.
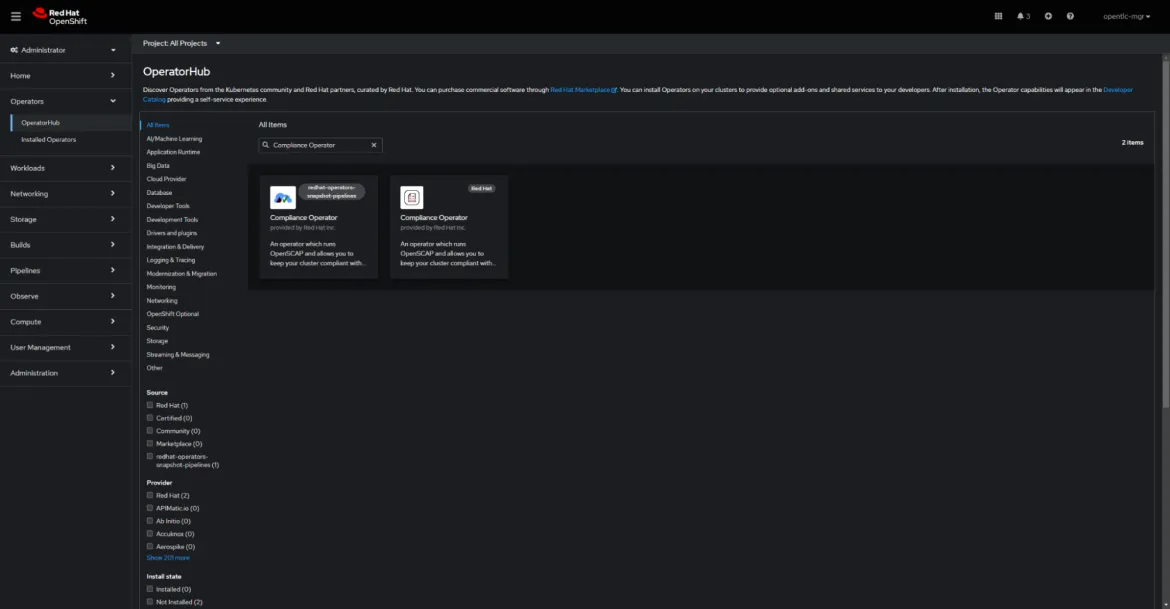
In today's landscape of rapidly evolving cyber threats, providing a more secure Kubernetes environment is essential. Red Hat Advanced Cluster Security and the Compliance Operator for OpenShift provide a powerful combination of tools to help organizations achieve this goal.
Advanced Cluster Security covers the entire container lifecycle, from image scanning to runtime threat detection, while the Compliance Operator adds a layer of compliance policy management and enforcement. Together, they create a robust security posture for Kubernetes environments, helping to protect your containerized applications against known vulnerabilities and threats while maintaining compliance with industry standards and regulations.
Deployment of Advanced Cluster Security and the Compliance Operator are the “easy button” for getting profiles like the STIG deployed, and even more importantly, maintained across the lifecycle of the Kubernetes environment. Not only do these tools help deploy the initial hardening and provide an invaluable understanding of your security posture, they allow you to more effectively and readily meet continuous monitoring requirements as part of the ATO process.
By embracing these Red Hat solutions, organizations can more confidently harness the full potential of Kubernetes for their applications while mitigating security risks and better meeting compliance requirements.
Getting started
Reach out to your Red Hat account team for more information, a demo, workshop, or even a proof of concept deployment, or deploy your own using a Red Hat provided OpenShift cluster from http://try.openshift.com.
Also don’t forget to check out the newly released Red Hat OpenShift DISA STIG.
Über den Autor
Chris Grimm is a Solutions Architect with Red Hat with over 15 years of experience in Information Systems Architecture, Engineering and Security, he has a breadth of knowledge across the IT sector. An advocate of implementing security during the design phase, he has been driving IT systems toward innovative and upcoming technology in an effort to migrate away from ailing legacy systems.
Prior to joining Red Hat, Chris was a CyberSecurity Engineer, leading accreditation and security efforts for DHA, VA and USAF systems along with extensive engineering & design support. Chris has spent a large portion of his career in the public sector supporting the defense industry as a civilian and as a United States Marine. Chris graduated from Limestone College with a Bachelor's Degree in Computer Science that included a focus on Information Systems Security.
Chris is an active member of the information security community regularly attending conferences and participating in local security events such as B-Sides Charleston where he helped develop the CTF (Capture the Flag) event and is also a Red Team member of the Palmetto Cyber Defense Competition.
Mehr davon
Nach Thema durchsuchen
Automatisierung
Das Neueste zum Thema IT-Automatisierung für Technologien, Teams und Umgebungen
Künstliche Intelligenz
Erfahren Sie das Neueste von den Plattformen, die es Kunden ermöglichen, KI-Workloads beliebig auszuführen
Open Hybrid Cloud
Erfahren Sie, wie wir eine flexiblere Zukunft mit Hybrid Clouds schaffen.
Sicherheit
Erfahren Sie, wie wir Risiken in verschiedenen Umgebungen und Technologien reduzieren
Edge Computing
Erfahren Sie das Neueste von den Plattformen, die die Operations am Edge vereinfachen
Infrastruktur
Erfahren Sie das Neueste von der weltweit führenden Linux-Plattform für Unternehmen
Anwendungen
Entdecken Sie unsere Lösungen für komplexe Herausforderungen bei Anwendungen
Original Shows
Interessantes von den Experten, die die Technologien in Unternehmen mitgestalten
Produkte
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Cloud-Services
- Alle Produkte anzeigen
Tools
- Training & Zertifizierung
- Eigenes Konto
- Kundensupport
- Für Entwickler
- Partner finden
- Red Hat Ecosystem Catalog
- Mehrwert von Red Hat berechnen
- Dokumentation
Testen, kaufen und verkaufen
Kommunizieren
Über Red Hat
Als weltweit größter Anbieter von Open-Source-Software-Lösungen für Unternehmen stellen wir Linux-, Cloud-, Container- und Kubernetes-Technologien bereit. Wir bieten robuste Lösungen, die es Unternehmen erleichtern, plattform- und umgebungsübergreifend zu arbeiten – vom Rechenzentrum bis zum Netzwerkrand.
Wählen Sie eine Sprache
Red Hat legal and privacy links
- Über Red Hat
- Jobs bei Red Hat
- Veranstaltungen
- Standorte
- Red Hat kontaktieren
- Red Hat Blog
- Diversität, Gleichberechtigung und Inklusion
- Cool Stuff Store
- Red Hat Summit
