Enterprise customers who adopt cloud are dealing with using multiple cloud providers, dynamic cloud environments, and need to meet enterprise security requirements and regulatory compliance requirements. Customers prefer open source, and not proprietary solutions. Hence, an approach that enables continuous security and audit readiness for open, hybrid multicloud is needed. Multicluster management requires a centralized approach to operate to enterprise and regulatory compliance standards. Our approach to achieve this goal is policy-based governance which uses policies to represent best practices and automated remediation of policy violations when possible. This blog-series focuses on policy-based governance for multicluster management to achieve security and compliance in a multicloud environment.
First, let's review some introductions about the governance architecture and some general concepts. Then, learn how to write and use the different kinds of policies. See some examples about different options to monitor those policies.
Red Hat Advanced Cluster Management for Kubernetes enables cluster, application, and the security lifecycle of hybrid and multicloud environments. Enterprises must meet internal standards for software engineering, secure engineering, resiliency, security, and regulatory compliance for workloads hosted on private, multi and hybrid clouds. Teams that provide enterprise cloud platforms, as well as application business units that run their business applications on simliar cloud platforms, can use Red Hat Advanced Cluster Management for Kubernetes governance capability. Use the governance capability to gain visibility and drive remediation for various security and configuration aspects to help meet such enterprise standards.
Governance architecture
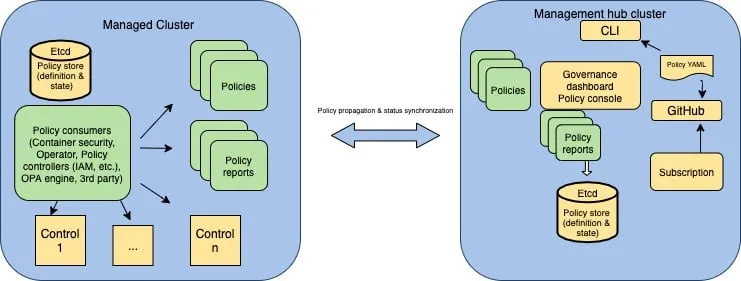
Governance is a structured way of operating an IT infrastructure based on defined policies, processes, and procedures. View the following diagram of the governance architecture:
The governance architecture is composed of the following components:
- Dashboard: Provides a summary of your cloud governance and risk details, which include policy violations.
- Policy UI, CLI, GitOps: Support policy creation and deployment to various managed clusters based on attributes associated with clusters, such as a geographical region.
- Policy store: Uses Kubernetes etcd to store policies as CustomResourceDefinition (CRD) objects.
- Controls: Security and configuration controls are designed for various enterprise standards.
- Policy consumers: Evaluates one or more policies on the managed cluster against your specified control, and generates Kubernetes events for violations. Violations are propagated to the hub cluster.
When you apply the governance architecture to your cluster, your cluster governance meet the following functionalities:
- Extensible policy framework that allows creation and distribution of policies to managed clusters from the hub cluster.
- Ability to integrate multiple policy languages, such as Open Policy Agent.
- Collection of policy violation details from the hub cluster.
- Customization of policies by customers by annotating compliance standards, control categories, and controls
- Policy dashboard is accessible for customers to customize their view and show policy violations by compliance standards and control categories.
Governance Lifecycle
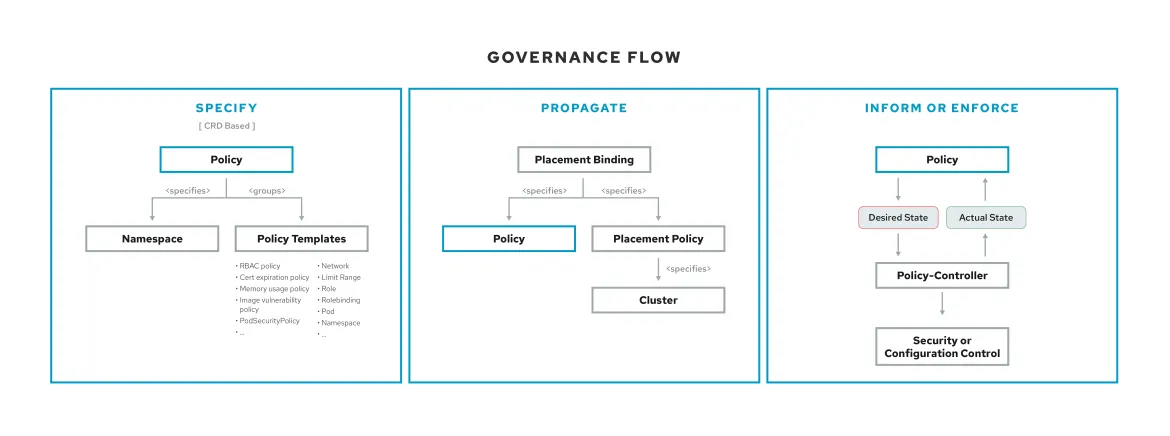
View the following diagram and a description of the governance flow:
Let's describe the flow a bit more:
-
Initially, policies are created and propagated to managed clusters using the Red Hat Advanced Cluster Management for Kubernetes console, command line interface (CLI), or GITOPS.
Note: Any Kubernetes (K8S) object including custom resource definitions (CRDs), can be represented as an object template within the specification section of a policy. More than one object template CRD can be specified in a single policy. When the policy is deployed to managed clusters, it can be enforced by either K8S, operators, or policy controllers that process the respective object template CRDs.
-
Policy controllers are deployed on managed clusters for various security controls.
-
Policy controllers periodically check specified policies against control state and remediate the violation. When the controller is set to
inform, a report of the violations is created. When the controller is set toenforceviolations are remediated as specified in the policy. -
The policy status is propagated to the hub cluster from each managed cluster.
-
The hub cluster displays policy violations organized by managed clusters, policies, and also by compliance standards and control categories.
-
Policies can be added by third party control providers and clients with no changes to the Red Hat Advanced Cluster Management for Kubernetes policy framework.
Open source community
Red Hat Advanced Cluster Management for Kubernetes policy framework, policy controllers, and policies are apart of the following open source project: open-cluster-management. You can use the open source policies to create custom annotations within the policy templates to specify one or more compliance standard, control category, and control.
This open source policy framework can be used as the foundation to develop policies for virtual machines, containers, middleware, applications, and hardware root of trust.
Security standards and control categories
When you create a policy, you can select a compliance standard, control category, and control. The following standards are predefined: HIPAA, NIST, PCI or PCI-DSS, and FISMA.
You can also define your own standard, for example Common Criteria. For more information, see Common Criteria.
A control category represents the presence of specific requirements for one or more controls, for example, System and Information integrity. This category might indicate that this policy contains a data transfer protocol protecting personal information, as required by the HIPAA and PCI standards. You can create a new label for your control categories by adding it directly to the YAML file.
View the following table for an example of policy templates for NIST 800-53 specification:
| NIST 800-53 Control family | Policy templates |
|---|---|
| Access control | Limit users with clusteradmin role, K8S role, K8S rolebinding |
| System and communications protection | Certificate management (expiration of certs) |
| System and information integrity | SCC, K8S pod security policy |
| Configuration | K8S resource limits, namespace, and pod |
Governance and risk
Let's discuss different monitoring options for the Governance and risk dashboard.
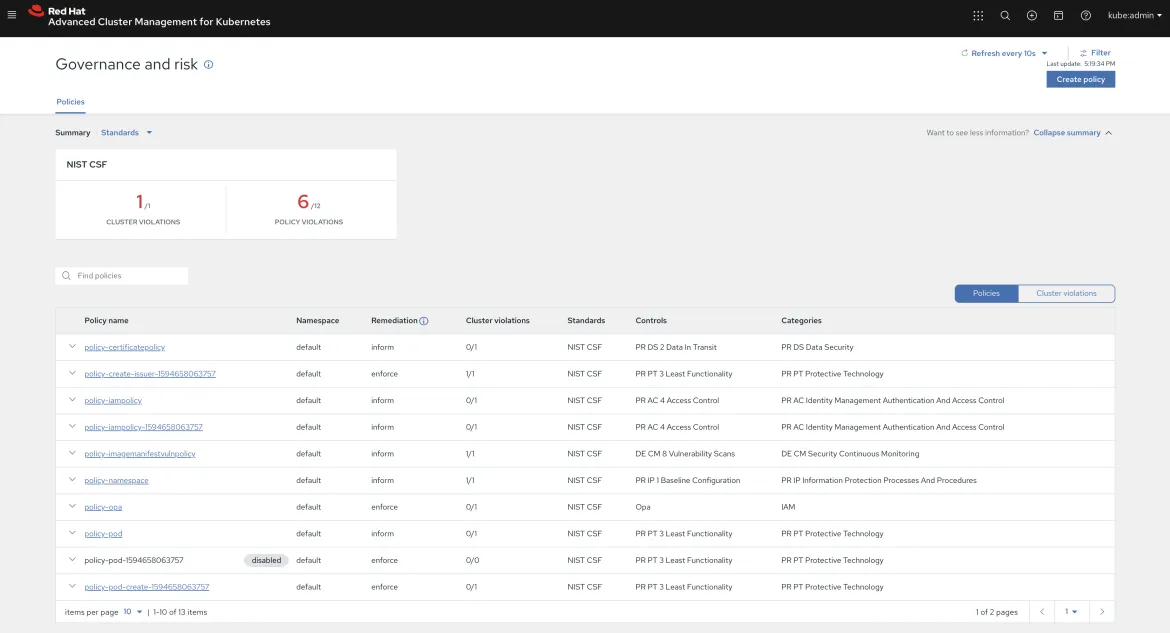
You can view an overview of your cluster violations and policy violations from the Governance and risk dashboard. The Policies page displays a table list view of all of the policy violatiions. You can filter the view of your cluster and policy violations for your tabled list.
Select a specific policy to view more policy information, such as placement policy and placement binding details, violations, and the YAML file. Policy violations are reported to the Red Hat Advanced Cluster Management for Kubernetes hub cluster by the policy controllers.
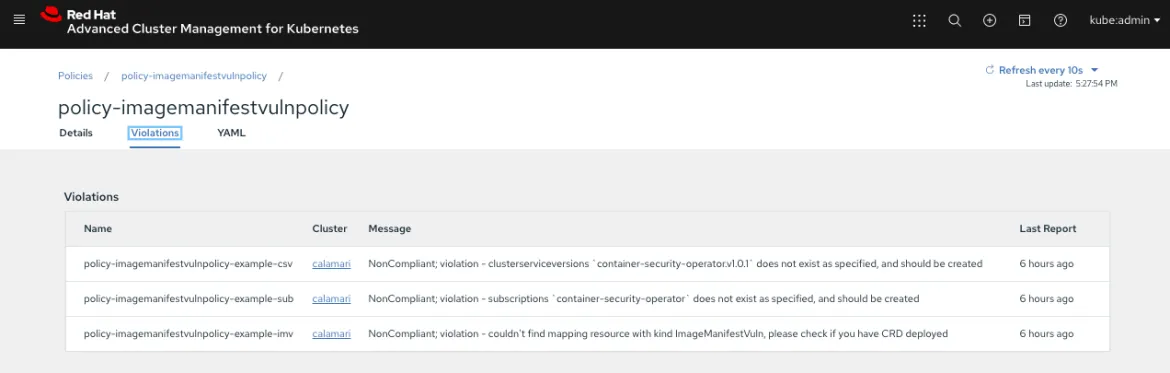
You can also create custom policies. View the following image of a custom policy that is integrated with OPA:
To learn more about creating custom policy controller, see Creating a custom policy controller in the product documentation.
Conclusion
Red Hat Advanced Cluster Management for Kubernetes governance provides an extensible framework for enterprises to introduce their own security and configuration policies. By writing a custom policy controller, enterprises can easily integrate existing enterprise security and configuration controls with Red Hat Advanced Cluster Management governance. Enterprises can also take advantage of the Governance and risk dashboard to create and manage both out-of-box policies and custom policies, monitor the policy compliance status, and take further remediation actions. To learn more, see Red Hat Advanced Cluster Management product page.
About the authors
Browse by channel
Automation
The latest on IT automation for tech, teams, and environments
Artificial intelligence
Updates on the platforms that free customers to run AI workloads anywhere
Open hybrid cloud
Explore how we build a more flexible future with hybrid cloud
Security
The latest on how we reduce risks across environments and technologies
Edge computing
Updates on the platforms that simplify operations at the edge
Infrastructure
The latest on the world’s leading enterprise Linux platform
Applications
Inside our solutions to the toughest application challenges
Original shows
Entertaining stories from the makers and leaders in enterprise tech
Products
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Cloud services
- See all products
Tools
- Training and certification
- My account
- Customer support
- Developer resources
- Find a partner
- Red Hat Ecosystem Catalog
- Red Hat value calculator
- Documentation
Try, buy, & sell
Communicate
About Red Hat
We’re the world’s leading provider of enterprise open source solutions—including Linux, cloud, container, and Kubernetes. We deliver hardened solutions that make it easier for enterprises to work across platforms and environments, from the core datacenter to the network edge.
Select a language
Red Hat legal and privacy links
- About Red Hat
- Jobs
- Events
- Locations
- Contact Red Hat
- Red Hat Blog
- Diversity, equity, and inclusion
- Cool Stuff Store
- Red Hat Summit