Security-Enhanced Linux (SELinux) is a form of mandatory access control (MAC) that helps Linux systems enforce file and process permissions. It's a default subsystem on Red Hat Enterprise Linux (RHEL), CentOS, Fedora, and many other Linux distributions.
SELinux is built around the concept of security labels and types. When you give a file an SELinux label of one type, then a process bearing a label of a different type cannot interact with it, even though the file's permissions on disk might be as permissive as 777 (which provides read, write, and execute permissions for owners, groups, and others).
SELinux uses policies to decide what labels and types are compatible with one another. For instance, if your system has the default policy that disallows an HTTP daemon to interact with users' home directories, then user home directories are essentially untouchable by httpd even though you may have a config file saying otherwise.
Read the full Red Hat documentation to gain a complete understanding of SELinux. Considerable work is put into SELinux policies by the time you install a system, but you can control policy decisions through SELinux booleans.
List booleans with semanage
The semanage command is an SELinux policy management tool. You can use it to view available boolean options:
$ sudo semanage boolean --list | head
SELinux boolean State Default
abrt_anon_write (off , off)
abrt_handle_event (off , off)
abrt_upload_watch_anon_write (on , on)
antivirus_can_scan_system (off , off)
antivirus_use_jit (off , off)
auditadm_exec_content (on , on)
authlogin_nsswitch_use_ldap (off , off)
authlogin_radius (off , off)
[...]
[ Improve your skills managing and using SELinux with this helpful guide. ]
If you've changed any booleans, you can view your custom settings with the --locallist or -C option:
$ sudo semanage boolean -l -C
SELinux boolean State Default
virt_sandbox_use_all_caps (on , on)
virt_use_nfs (on , on)
zebra_write_config (on , on)
When to use a boolean
The most common way to find out that a boolean has been designed to prevent an interaction is with SELinux Troubleshooter. When SELinux registers an attempted violation of a policy, it logs the decision as an Access Vector Cache (AVC). The Troubleshooter app spawns desktop notifications any time there's an AVC denial so that you can review the decision and override or report it as appropriate.
That's the main way you're alerted about SELinux activity, and many times it's the way you solve an issue.
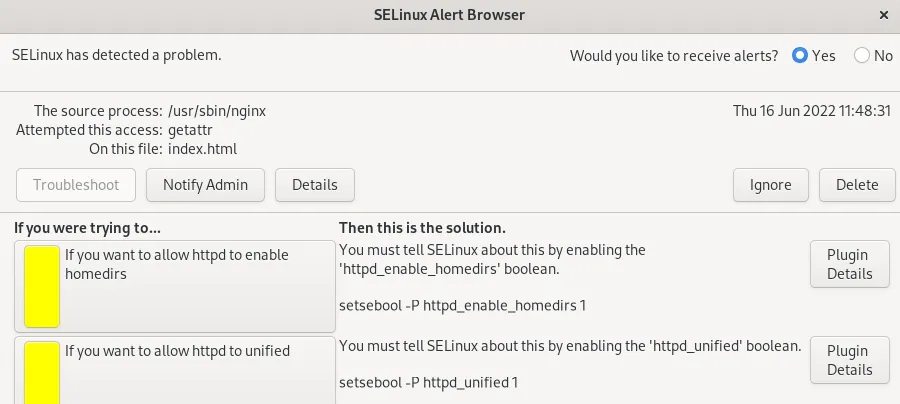
In the example of an Nginx web server attempting to access a home directory, SELinux Troubleshooter suggests that you enable the httpd_enable_homedirs boolean. It even gives you a command you can use.
Should SELinux Troubleshooter fail to notify you about a denial (or if you don't have it installed), you may still be able to look through available booleans and find the one that makes sense for you to activate or deactivate. Most booleans are named in the interest of clarity. If you're diagnosing an error with NFS, for instance, you can list booleans, grep for nfs, and you'll likely find the boolean you're looking for.
If you don't have SELinux Troubleshooter installed, you can install it with:
$ sudo dnf install setroubleshoot
Set a boolean with semanage or setsebool
To modify an SELinux boolean, you can use semanage --modify along with either --on or --off. For instance, here's how to modify the httpd_allow_homedirs boolean:
$ sudo semanage boolean --modify --on http_allow_homedirs
If you prefer, you can use setsebool, which arguably has a simpler syntax:
$ sudo setsebool -P httpd_enable_homedirs 1
The setsebool command is a tool for quickly and easily setting SELinux booleans. The -P option makes your decision persistent across reboots, and the 1 makes the boolean true.
SELinux booleans in the filesystem
All SELinux boolean values are viewable as a file in your filesystem. They're expressed as files in the /sys/fs/selinux/booleans directory:
$ cat /sys/fs/selinux/booleans/httpd_use_nfs
0 0
$ cat /sys/fs/selinux/booleans/httpd_enable_homedirs
1 1
SELinux booleans
SELinux booleans allow you to control specific attributes of SELinux policies. Change them thoughtfully and because you understand why you want to override them. Policies exist for good reasons, but you also have control over them because you're the expert on your own system. Using semanage, setsebool, and SELinux Troubleshooter, you can make intelligent and quick decisions about what files and processes are allowed to interact.
Sobre el autor
Seth Kenlon is a Linux geek, open source enthusiast, free culture advocate, and tabletop gamer. Between gigs in the film industry and the tech industry (not necessarily exclusive of one another), he likes to design games and hack on code (also not necessarily exclusive of one another).
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Programas originales
Vea historias divertidas de creadores y líderes en tecnología empresarial
Productos
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Servicios de nube
- Ver todos los productos
Herramientas
- Training y Certificación
- Mi cuenta
- Soporte al cliente
- Recursos para desarrolladores
- Busque un partner
- Red Hat Ecosystem Catalog
- Calculador de valor Red Hat
- Documentación
Realice pruebas, compras y ventas
Comunicarse
- Comuníquese con la oficina de ventas
- Comuníquese con el servicio al cliente
- Comuníquese con Red Hat Training
- Redes sociales
Acerca de Red Hat
Somos el proveedor líder a nivel mundial de soluciones empresariales de código abierto, incluyendo Linux, cloud, contenedores y Kubernetes. Ofrecemos soluciones reforzadas, las cuales permiten que las empresas trabajen en distintas plataformas y entornos con facilidad, desde el centro de datos principal hasta el extremo de la red.
Seleccionar idioma
Red Hat legal and privacy links
- Acerca de Red Hat
- Oportunidades de empleo
- Eventos
- Sedes
- Póngase en contacto con Red Hat
- Blog de Red Hat
- Diversidad, igualdad e inclusión
- Cool Stuff Store
- Red Hat Summit

