In this post:
-
Learn to install OpenSCAP and the SCAP security guide on RHEL
-
Add RHEL hosts to Red Hat Insights compliance policies
-
Create a report to determine compliance with SCAP policies for your systems
Sysadmins trying to ride herd over tens, hundreds or thousands of systems need tools to help keep systems in compliance with policies and security standards. In this post we'll look at using Red Hat Insights compliance service to manage compliance at scale.
Verifying that your organization's systems satisfy your compliance requirements is something that takes time and effort. Too often it's only done on an ad hoc basis. That approach may work for organizations with a limited number of hosts, but performing this task at scale is problematic with complex environments and limited resources.
Fortunately, organizations that use Red Hat Enterprise Linux (RHEL) in a standard operating environment (SOE) can take advantage of Red Hat Insights and its Compliance service to proactively and efficiently manage their regulatory compliance requirements at scale.
Combining Red Hat Insights with Red Hat Smart Management and the Red Hat Ansible Automation Platform to create an automated process for compliance configuration, validation, and remediation can lessen the administrative burden of your compliance workload.
Red Hat Insights Compliance overview
Red Hat Insights uses Security Content Automation Protocols (SCAP) Policies certified by the National Institute of Standards and Technology (NIST) as the basis for ensuring RHEL hosts maintain compliance with defined policies. These policies are implemented in RHEL using OpenSCAP System Security Guides (SSG). While this post describes how to use the SCAP System Security Guides, the details of the rules contained within the SSGs are outside the scope of this post.
The instructions contained in this post assume that the reader has basic knowledge of Red Hat Insights and its implementation within the Hybrid Cloud Console.
This is the first of a series of planned posts that will take you through a process that demonstrates:
-
How to prepare your hosts and Red Hat Insights for compliance automation.
-
Performing compliance remediations on your hosts using both Smart Management and the Ansible Automation Platform.
-
Using the Red Hat Insights application programming interface (API) to ready your hosts for compliance during a SOE deployment.
Preparing your hosts
The Compliance service within Red Hat Insights has greatly simplified the processing of RHEL hosts in Compliance Reporting. The first step in the process is to ensure that your hosts are configured to accept an OpenSCAP SSG.
Installing the SCAP System Security Guide
An SOE is a Red Hat-recommended practice for deploying hosts. With an SOE, you can be more confident that your hosts match your organization's standards including operating system versions and patch levels, required add-on packages and security controls, among others. While an SOE is not required to participate in Red Hat’s Compliance service, it is mentioned here as a best practice.
In order for your hosts to participate in this automated compliance process, it is necessary that the hosts:
-
Be registered with Red Hat Insights.
-
Have OpenSCAP installed.
-
Have the SCAP Security Guide installed.
Registering a RHEL 8 system with Red Hat Insights is straightforward, as the Insights client is installed by default. I recommend that you register your hosts with Red Hat Insights during deployment by using the RHEL System Role. When I build my SOE for my hosts, I include the following task in an Ansible Playbook:
- include_role: name: redhat.insights.insights_client
This will execute a RHEL System Role that will install Insights (on RHEL 7 hosts) and register the Insights client (on RHEL 7 and RHEL 8 hosts) with the Red Hat Insights for Red Hat Enterprise Linux service
Additionally, as part of your SOE the OpenSCAP packages must be installed from the RHEL 8 appstream repo. To do this, add the following task to your SOE package install playbook.
tasks:
- name: install insights compliance
import_role:
name: redhat.insights.compliance
tasks_from: install
The task used from this role installs the following packages:
-
openscap
-
scap-security-guide
-
openscap-scanner
Adding a host to a compliance policy
Once your host is prepared, it must be assigned a compliance policy.
Please note: While these instructions demonstrate a somewhat manual process, I plan to cover how to use the Insights API to automate the process in a future post.
The Compliance service is accessed from the Security Insights navigation pane.
The creation of an SCAP Policy is a straightforward process. The next few screenshots will take you through the process.
-
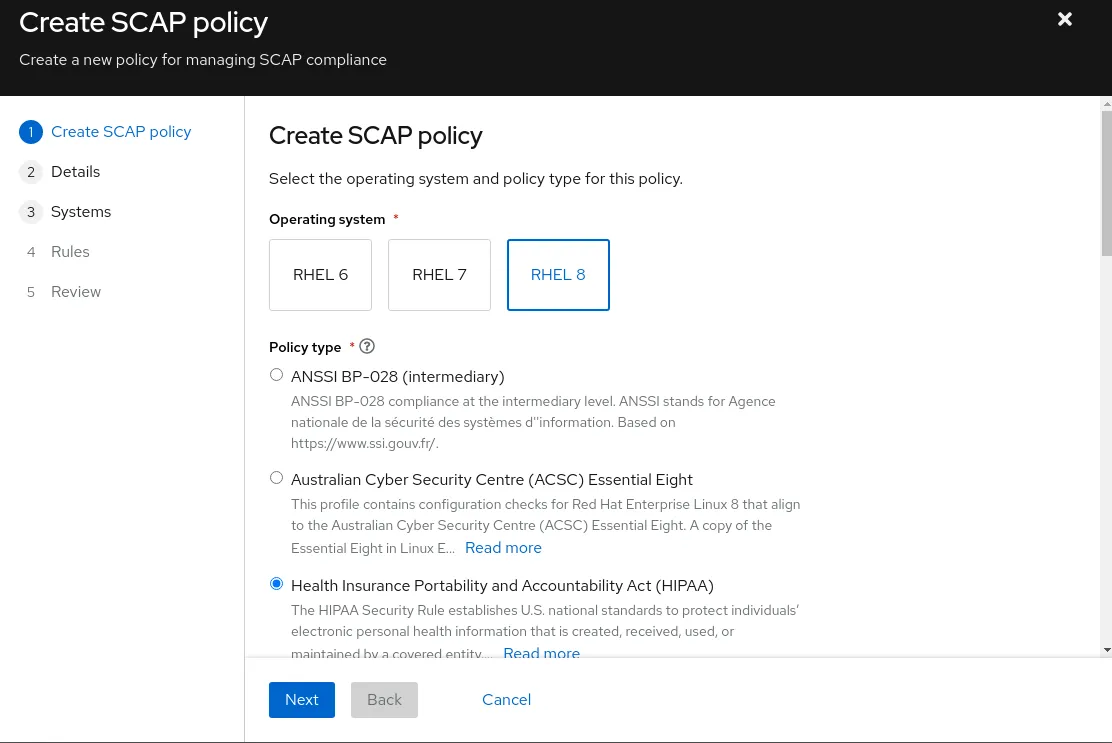
Clicking Create SCAP Policy will initiate the wizard. Please note that SCAP Policies are operating system version dependent. For this exercise, I have selected to create a RHEL 8 - Health Insurance Portability and Accountability Act (HIPAA) policy.
-
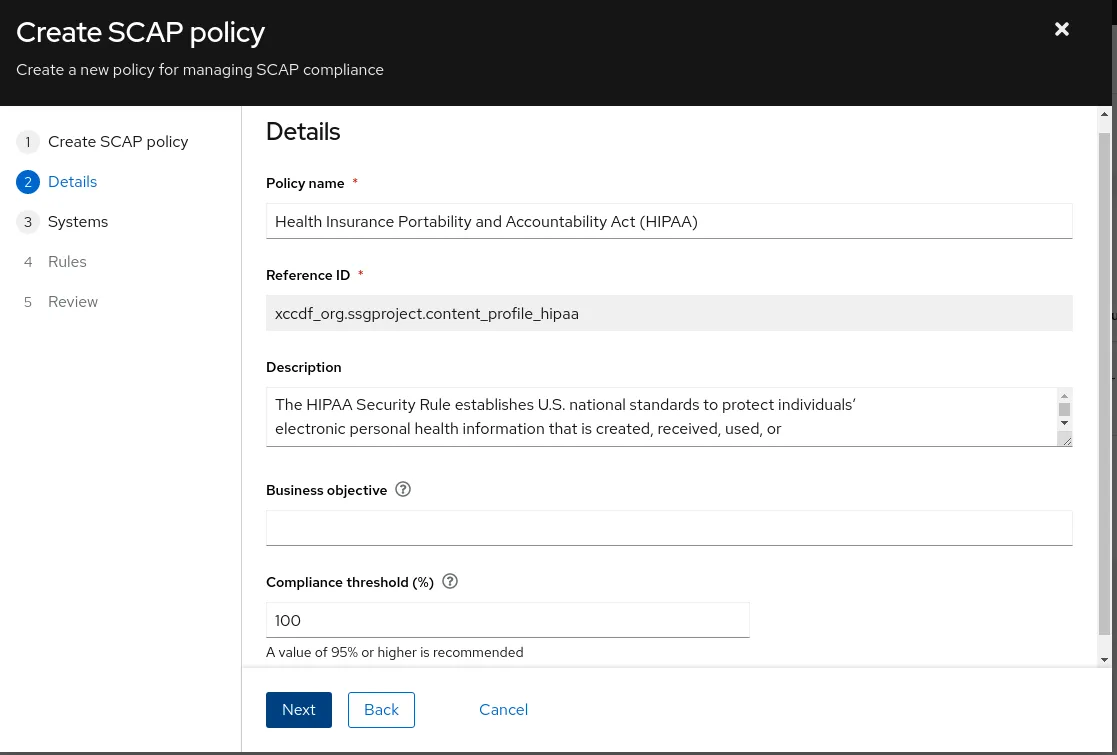
Clicking Next brings up the details page. This page allows you to set your business objective and overall acceptable compliance score. Once a host reaches that compliance score, it will be considered compliant with that policy.
-
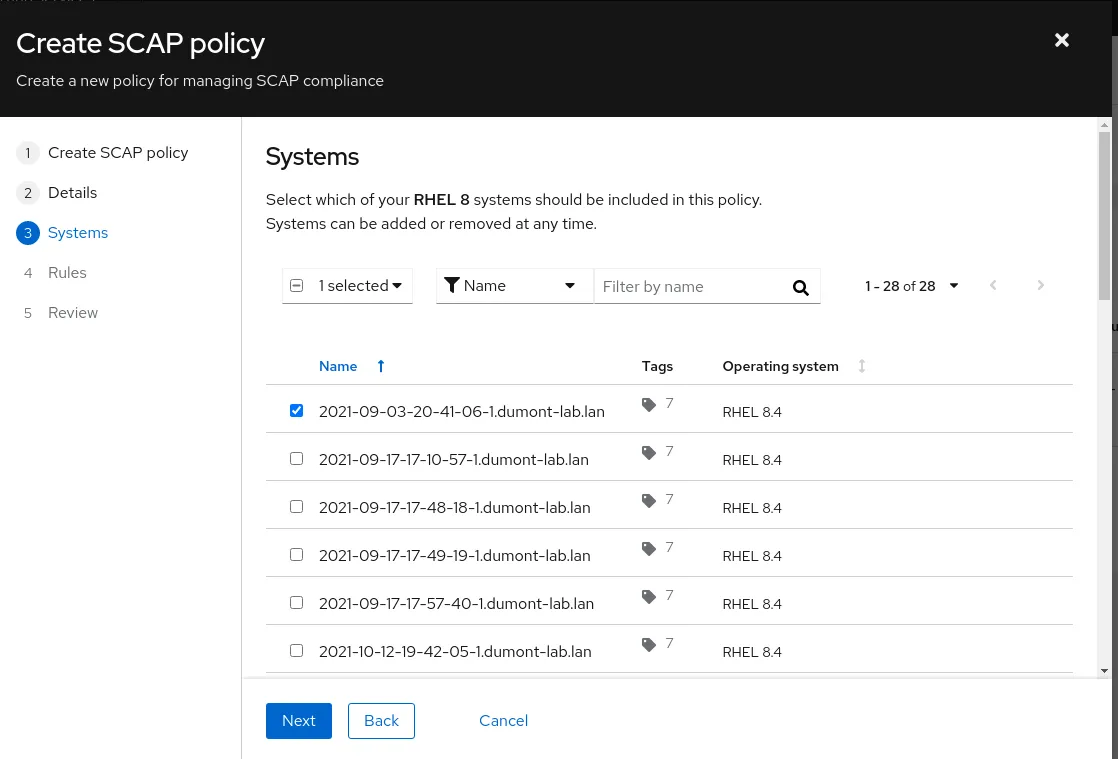
Clicking Next allows you to select the systems that will be subject to this compliance policy. This list only includes hosts that have been registered using the Insights client. In this example, I have selected a single system.
-
Clicking Next again provides you with a window to customize the standard SCAP Policy (the HIPAA policy in this instance) to your specific business objectives. While the technical process is simple to perform using this wizard, you should carefully review that any rules added or removed are consistent with your overall business goals.
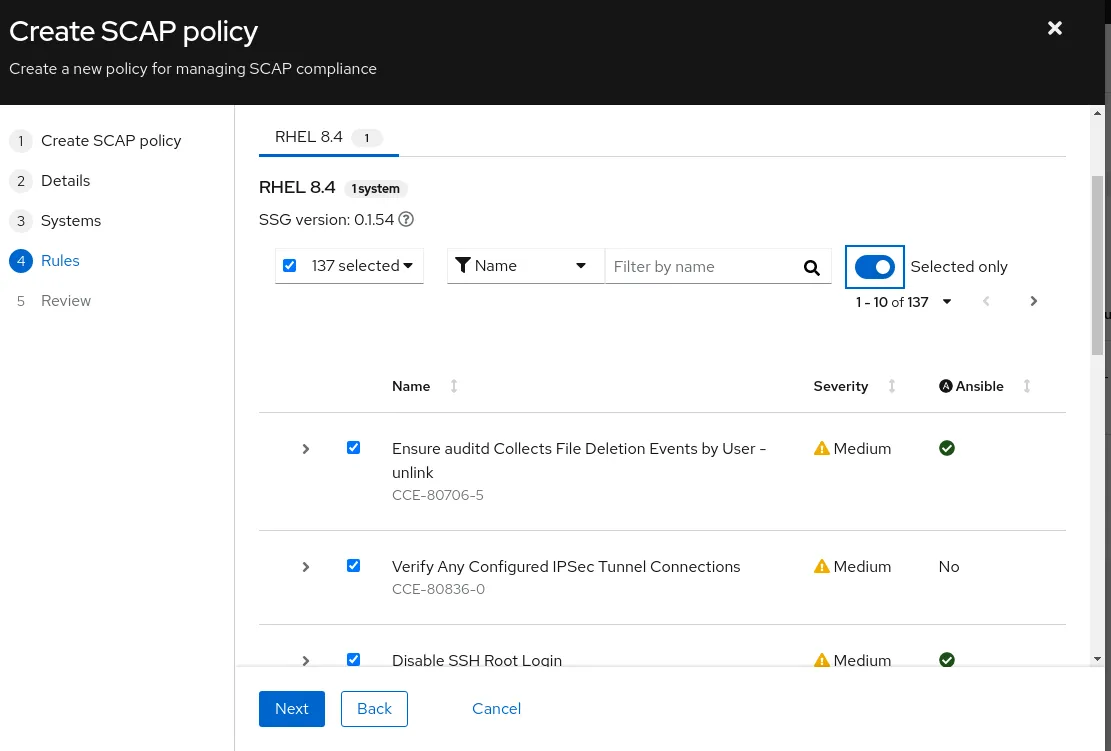
-
Clicking Next provides you with an opportunity to review the policy. Then, click Finish.
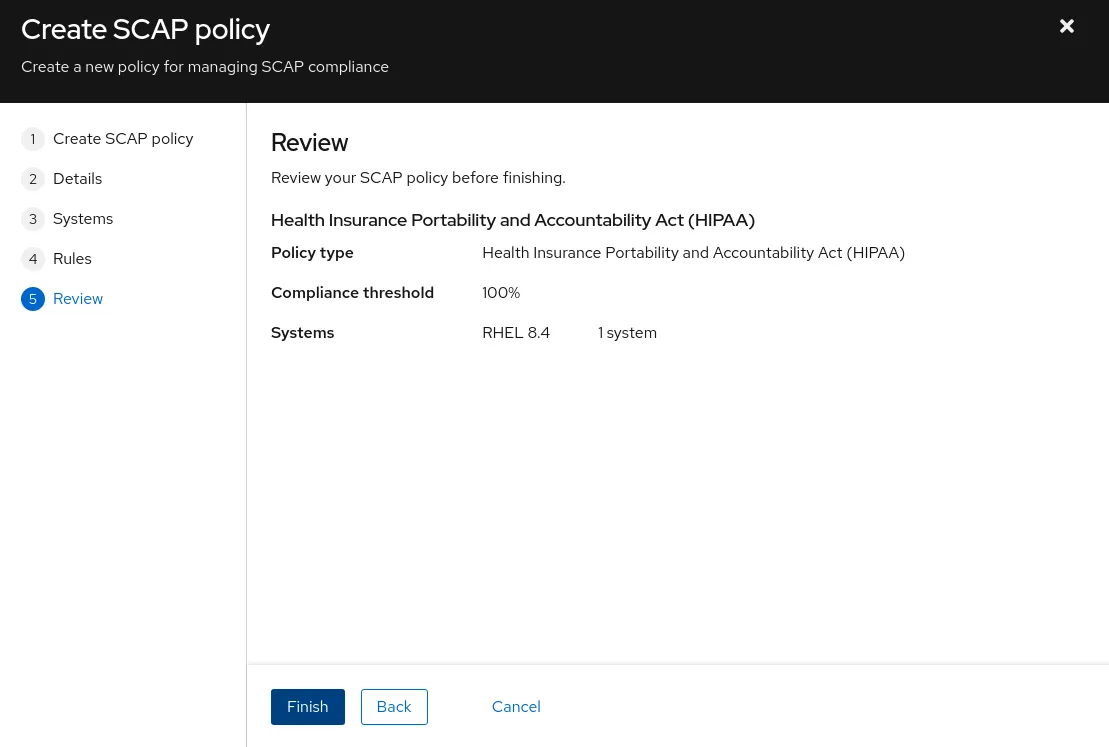
-
Once you click Finish, the policy is added to the Insights Compliance service and ready to create reports.
Reporting
Once you complete these steps, your systems are configured to report on their compliance to the specified OpenSCAP policy. However, at this point there are no reports that have been created and uploaded for the specified hosts.
Clicking into the reporting menu will show that no reports are available.
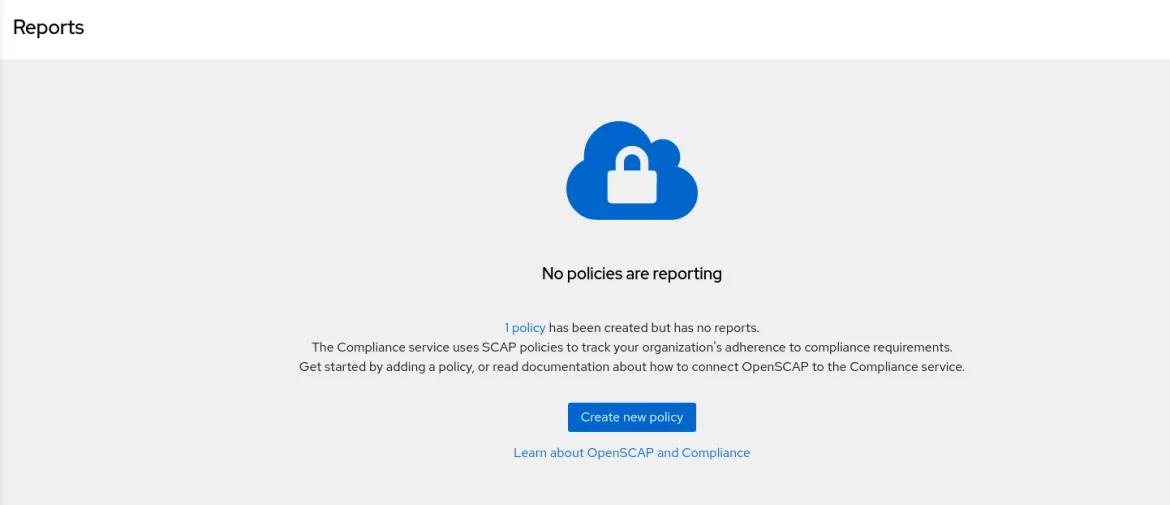
In order to get reports up to the Red Hat Insights Compliance service, the OpenSCAP Scanner needs to be run. This scanner compares the host configuration to the SSG associated with the policy.
Reporting is accomplished by running `insights-client --compliance` on each of the hosts. This is best accomplished by utilizing the Insights Role.
The Ansible playbook that allows this to be run is as follows:
tasks:
- name: run insights compliance
import_role:
name: redhat.insights.compliance
tasks_from: run
While running an Ansible playbook from the command line is effective, for most enterprises, Red Hat recommends that that the playbook be executed by the Ansible automation controller (formerly known as Ansible Tower). Please note, the process could also be executed using Red Hat Satellite.
The template that is created from that playbook is depicted here. Please note that the copliance scan must be run as a user with root privileges, therefore the privileged escalation box is checked.
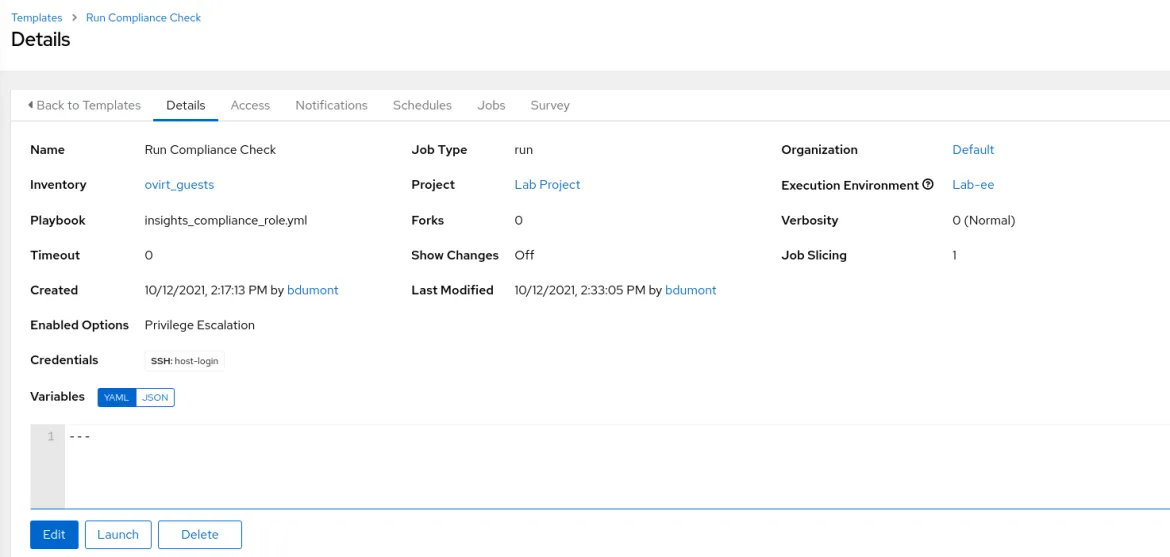
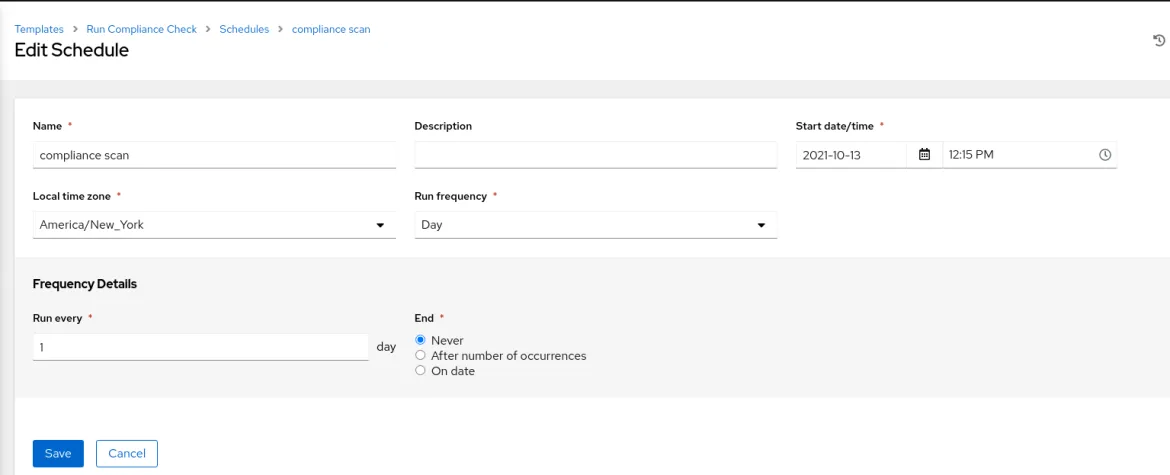
The next step in this automation process is to set up a schedule to run this template on a timeline that suits your business goals. Your compliance requirements call for quarterly reporting, however you may want to run these scans more frequently to maintain your systems in a continual compliance mode.
This is done via the scheduling function in the Ansible automation controller. In this example I have set this template to run on a daily basis at 12:15 AM.
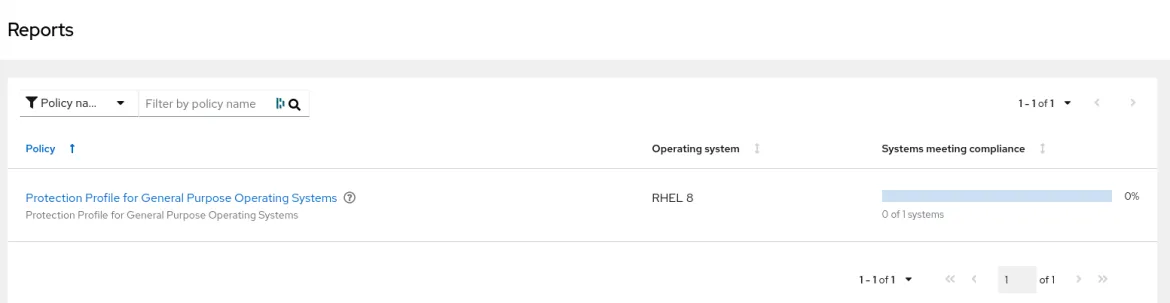
Once the scan is run, please revisit the Compliance Service -> Reports to see that a report is now available for action.
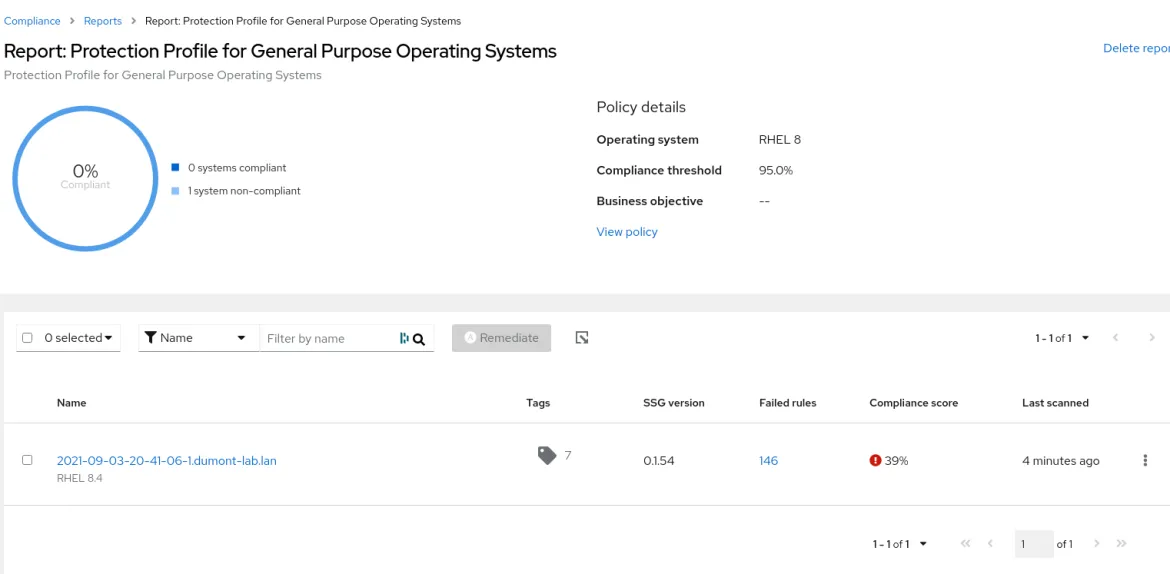
Clicking on the report will bring up the details of the scan.
What’s next?
Now that we understand our compliance score, it’s time to remediate. We plan to cover two options to remediate the issues and to bring the systems into compliance in future posts. Please visit Red Hat Insights Data & Application Security page to get common questions answered about Insights security and how your data is handled. Visit the Insights Getting Started page to learn more and get started.
À propos de l'auteur
As a Red Hat Certified Architect, Brian Dumont provides account-level technical leadership across Red Hat's product stack including OpenShift, Ansible, Satellite and Red Hat Enterprise Linux. He is responsible for understanding Red Hat's customer's business requirements and creating technology solutions to satisfy those requirements
Contenu similaire
Parcourir par canal
Automatisation
Les dernières nouveautés en matière d'automatisation informatique pour les technologies, les équipes et les environnements
Intelligence artificielle
Actualité sur les plateformes qui permettent aux clients d'exécuter des charges de travail d'IA sur tout type d'environnement
Cloud hybride ouvert
Découvrez comment créer un avenir flexible grâce au cloud hybride
Sécurité
Les dernières actualités sur la façon dont nous réduisons les risques dans tous les environnements et technologies
Edge computing
Actualité sur les plateformes qui simplifient les opérations en périphérie
Infrastructure
Les dernières nouveautés sur la plateforme Linux d'entreprise leader au monde
Applications
À l’intérieur de nos solutions aux défis d’application les plus difficiles
Programmes originaux
Histoires passionnantes de créateurs et de leaders de technologies d'entreprise
Produits
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Services cloud
- Voir tous les produits
Outils
- Formation et certification
- Mon compte
- Assistance client
- Ressources développeurs
- Rechercher un partenaire
- Red Hat Ecosystem Catalog
- Calculateur de valeur Red Hat
- Documentation
Essayer, acheter et vendre
Communication
- Contacter le service commercial
- Contactez notre service clientèle
- Contacter le service de formation
- Réseaux sociaux
À propos de Red Hat
Premier éditeur mondial de solutions Open Source pour les entreprises, nous fournissons des technologies Linux, cloud, de conteneurs et Kubernetes. Nous proposons des solutions stables qui aident les entreprises à jongler avec les divers environnements et plateformes, du cœur du datacenter à la périphérie du réseau.
Sélectionner une langue
Red Hat legal and privacy links
- À propos de Red Hat
- Carrières
- Événements
- Bureaux
- Contacter Red Hat
- Lire le blog Red Hat
- Diversité, équité et inclusion
- Cool Stuff Store
- Red Hat Summit

