As more and more organizations adopt cloud-native technologies, being able to leverage multiple cloud environments is becoming increasingly important. As such, being able to achieve cohesive security positions across those environments is equally important. Through close collaboration with Paladin Cloud, and by leveraging the strengths of Red Hat Advanced Cluster Security and Paladin Cloud's extensive Cloud Security Posture Management, the collaboration has yielded a solution that bridges the gap between multi and hybrid cloud environments across infrastructure and Kubernetes that delivers a unified platform tailored to managing cloud security risks more effectively.
Power through collaboration
Red Hat Advanced Cluster Security delivers Kubernetes-native security capabilities across environments and Kubernetes platforms, including support for Amazon EKS, Google GKE, Microsoft AKS and Red Hat OpenShift. Red Hat Advanced Cluster Security helps users to manage vulnerabilities by identifying and fixing vulnerabilities in both container images and Kubernetes across the entire software development lifecycle. It also enables users to adhere to compliance standards by auditing your systems against CIS Benchmarks, NIST, PCI, and HIPAA, with interactive dashboards and one-click audit reports, allowing you to see all your deployments ranked by risk level, using context from Kubernetes’ declarative data to prioritize remediation.
With Red Hat Advanced Cluster Security you can also visualize existing vs. allowed network traffic and enforce network policies and tighter segmentation using Kubernetes-native controls. Using our Configuration Management feature, you can apply best practices to harden your Kubernetes environments and workloads for a security-focused, more stable application. Additionally, you can use rules, allowlists, and baselining to identify suspicious activity to take action to thwart attacks, using Kubernetes for enforcement.
But what about the underlying infrastructure? This is where Red Hat's collaboration with Paladin Cloud comes in. By identifying the multi and hybrid cloud assets, along with the Kubernetes deployments via the Red Hat Advanced Cluster Security plugin, Paladin Cloud's Cloud Security Posture Management helps further secure the underlying infrastructure where Kubernetes workloads run.
Connecting Red Hat Advanced Cluster Security with Paladin Cloud
Connecting is simple. Here's a step-by-step guide:
1. Prerequisites
- To set up a connection between these security platforms, you will need to have a Paladin Cloud instance and be running Red Hat Advanced Cluster Security.
- Next, you need two pieces of data so they can talk to one another. This is your Red Hat Advanced Cluster Security instance ID & an Authentication Token. The ID lets Paladin Cloud know where to pull the data from, and the authentication token makes sure Paladin Cloud has the needed access.
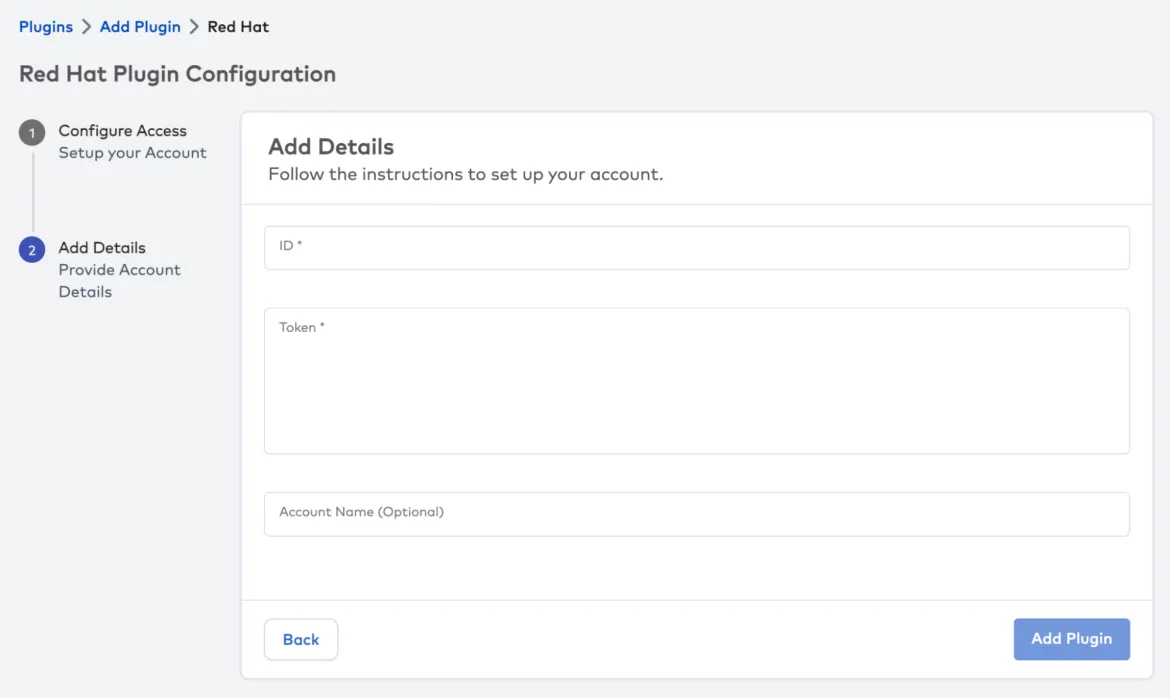
- In Paladin Cloud, go to the plugin page under Admin (You will need Admin permissions)
- Choose Add Plugin and select the Red Hat Advanced Cluster Security plugin.
- This will give you the latest instructions to configure the account.
2. Retrieve your Red Hat Advanced Cluster Security instance ID
- Log in to the Red Hat Console.
- Access the ACS Instance page by selecting `Advanced Security Cluster` in the side menu. Click on the ACS instance you want to link with Paladin Cloud.
- Copy the `ID` from the `Instance Details` card inside the chosen Red Hat Advanced Cluster Security instance.
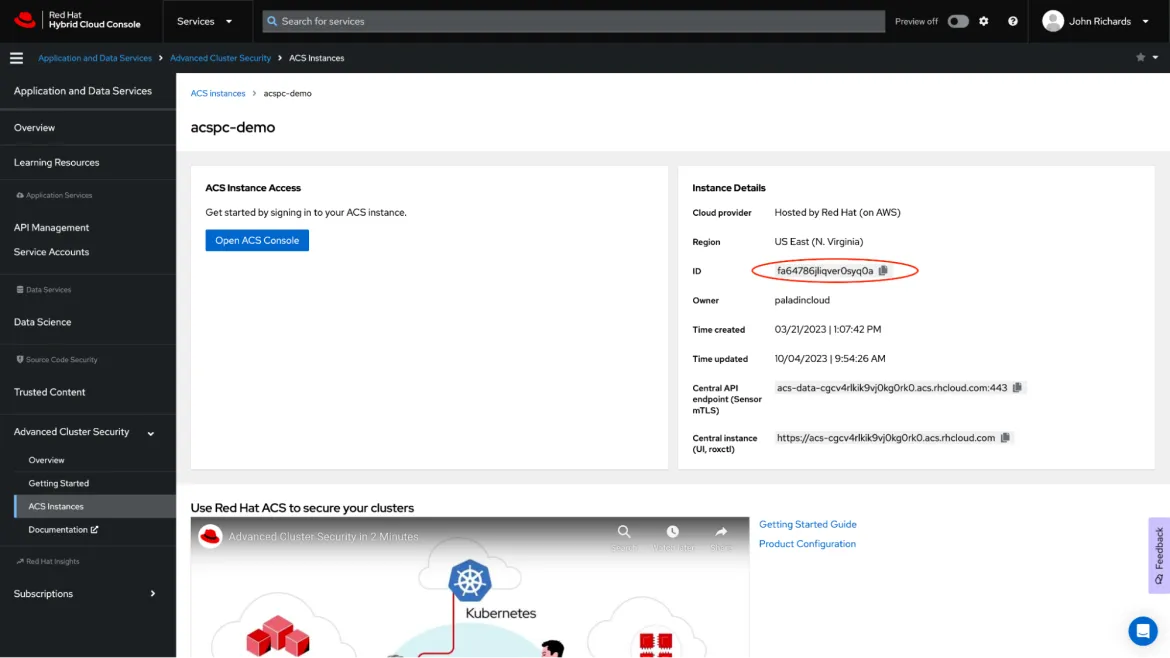
- Switch to the Paladin Cloud application, and hit next to go to the Add Details page. Paste in the copied `ID` into the `ID Field`.
3. Setup an authentication token
- Return to the Red Hat Advanced Cluster Security Instance page and click the “Open ACS Console” button.
- Access Platform Configuration from the side menu and choose the 'Integrations' option.
- Scroll down to the 'Authentication Tokens' section.

- Select 'API Token'. You'll be taken to the 'Integration API Tokens' page, which lists previously generated tokens (if any).
- Click the 'Generate Token' button.
- Name the token and choose the Analyst role.
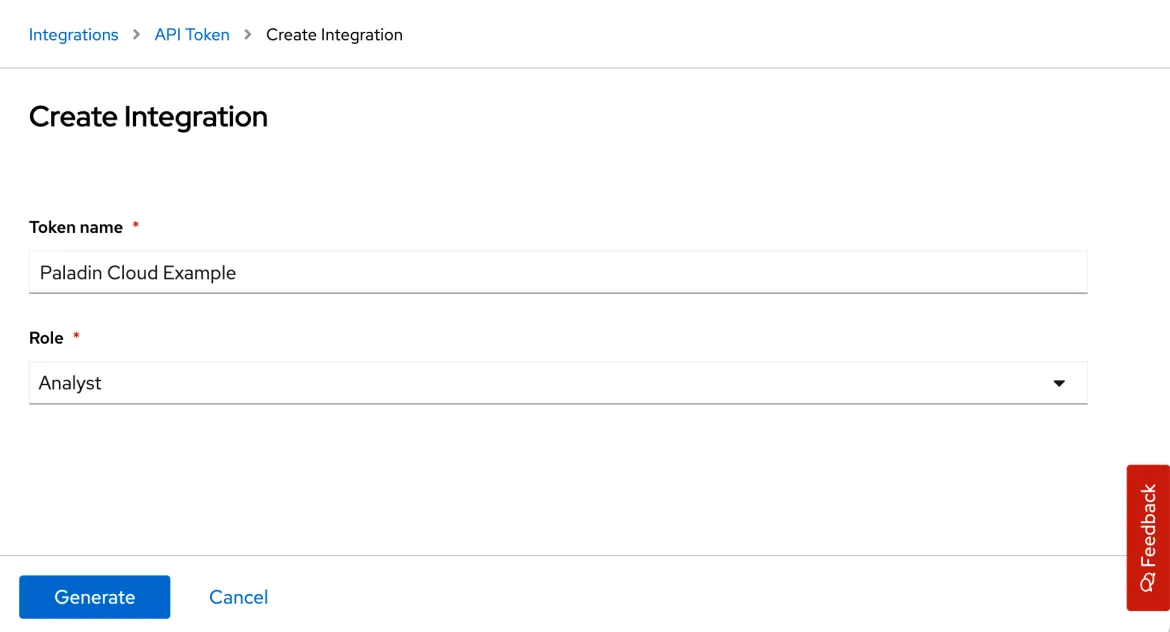
- Copy and paste the generated token into the token input field within the Red Hat Plugin in the Paladin Cloud application.
IMPORTANT: Be sure to store the copied token safely. Once generated, it won't be visible again for security reasons.
4. Validate the configuration
- Hit the 'Validate' button to confirm the setup was successful. If so, this will add the plugin to Paladin Cloud.
- If you get a success message, you should see data begin to populate within 30 minutes.
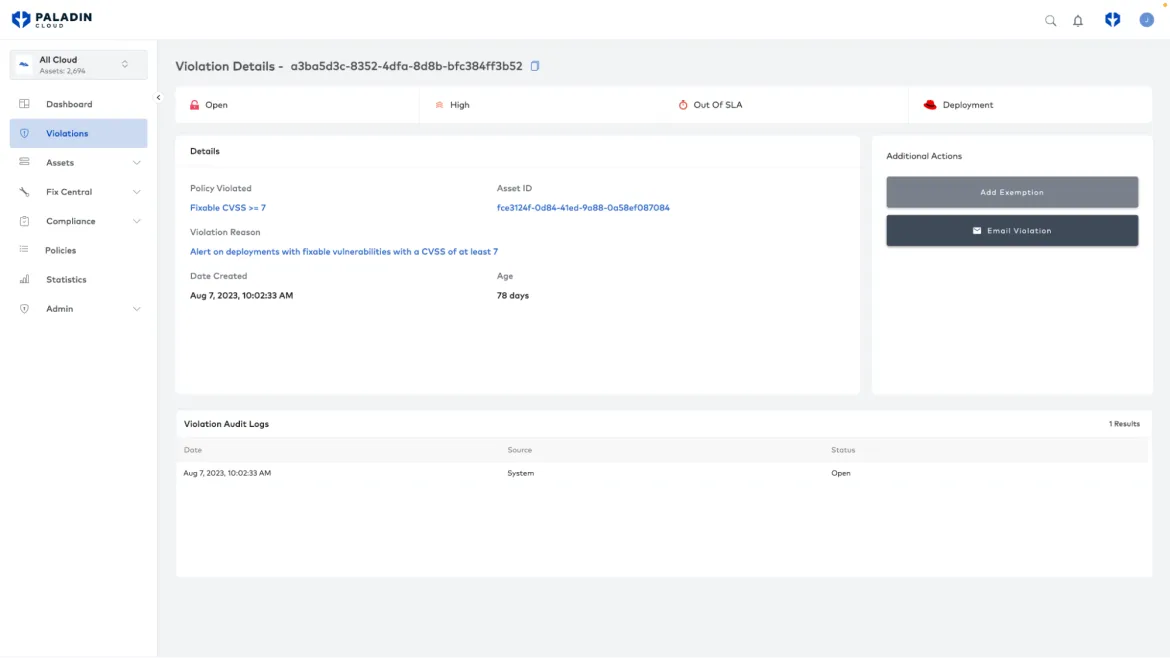
- Go to the Asset Group Selector and choose Red Hat to see a dashboard on your OpenShift assets.
- You can view your Kubernetes deployments and the risks Red Hat Advanced Cluster Security has identified.
- For any Advanced Cluster Security violations, you can click through the corresponding link to go directly to that finding in Advanced Cluster Security for further details on risk and steps on remediation.
Moving forward
By leveraging our partner ecosystem we continue to be able to offer increased choice and flexibility providing our customers the best, enterprise-grade, open source solutions to meet their needs. Our collaboration with Paladin Cloud is continuous and we have more integrations planned for the future.
À propos de l'auteur
Sean Rickerd, a distinguished professional in the technology and security domain, seamlessly blends his extensive career journey with a commitment to excellence. From his early days at SUSE to his current role as Principal Technical Marketing Manager at Red Hat, Sean's writing reflects a dedication to continuous learning. With a focus on authoring about cutting-edge fields like DevSecOps and Kubernetes security, he stands at the forefront of driving innovation and elevating security practices.
Parcourir par canal
Automatisation
Les dernières nouveautés en matière d'automatisation informatique pour les technologies, les équipes et les environnements
Intelligence artificielle
Actualité sur les plateformes qui permettent aux clients d'exécuter des charges de travail d'IA sur tout type d'environnement
Cloud hybride ouvert
Découvrez comment créer un avenir flexible grâce au cloud hybride
Sécurité
Les dernières actualités sur la façon dont nous réduisons les risques dans tous les environnements et technologies
Edge computing
Actualité sur les plateformes qui simplifient les opérations en périphérie
Infrastructure
Les dernières nouveautés sur la plateforme Linux d'entreprise leader au monde
Applications
À l’intérieur de nos solutions aux défis d’application les plus difficiles
Programmes originaux
Histoires passionnantes de créateurs et de leaders de technologies d'entreprise
Produits
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Services cloud
- Voir tous les produits
Outils
- Formation et certification
- Mon compte
- Assistance client
- Ressources développeurs
- Rechercher un partenaire
- Red Hat Ecosystem Catalog
- Calculateur de valeur Red Hat
- Documentation
Essayer, acheter et vendre
Communication
- Contacter le service commercial
- Contactez notre service clientèle
- Contacter le service de formation
- Réseaux sociaux
À propos de Red Hat
Premier éditeur mondial de solutions Open Source pour les entreprises, nous fournissons des technologies Linux, cloud, de conteneurs et Kubernetes. Nous proposons des solutions stables qui aident les entreprises à jongler avec les divers environnements et plateformes, du cœur du datacenter à la périphérie du réseau.
Sélectionner une langue
Red Hat legal and privacy links
- À propos de Red Hat
- Carrières
- Événements
- Bureaux
- Contacter Red Hat
- Lire le blog Red Hat
- Diversité, équité et inclusion
- Cool Stuff Store
- Red Hat Summit

