As the world's leading provider of enterprise-ready open source software, Red Hat is uniquely positioned to help prepare the widely varying users of its embedded platform cryptography for the transition to a post-quantum world.
In fact, the US Government calls it "imperative" in a recent National Security Memorandum:
[Becoming quantum-ready is] imperative across all sectors of the United States economy, from government to critical infrastructure, commercial services to cloud providers, and everywhere else that vulnerable public-key cryptography is used — NSM-10
Part of Red Hat's mission is to lead the way in providing innovative solutions that prepare users across various sectors for significant technology shifts, with the quantum revolution being the most near-term. With the dramatic increase in computing capabilities posed by quantum computing, what does this mean for cybersecurity?
The risks posed by quantum
Today, the danger of encrypted data falling into the wrong hands is real. Criminals and state actors seek to capture sensitive information for future decryption and exploitation. Current cryptographic systems, such as RSA, rely on prime factorization or other mathematical systems; these systems work well with today's computing capabilities, but the power of quantum computing means that these systems can be more readily compromised. The implications for our trust in compute platforms, software distribution, data security and telecommunications are immense.
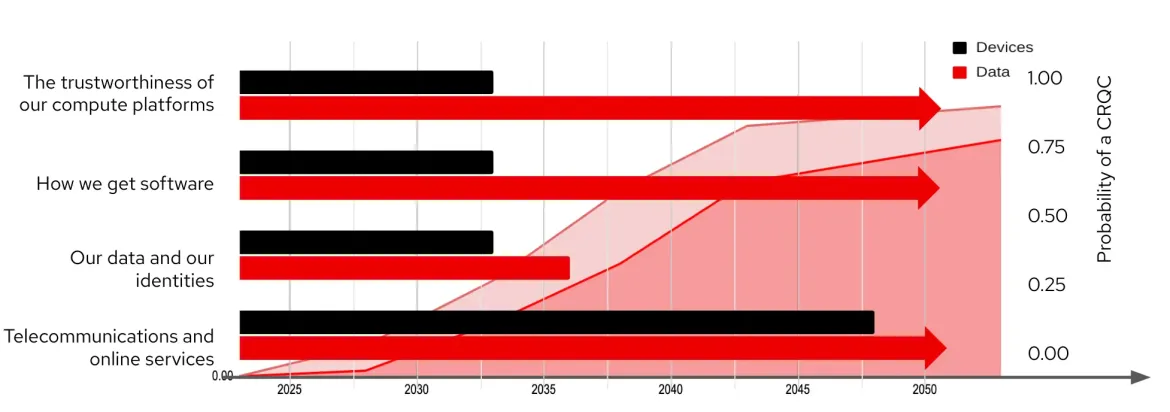
All types of information systems are vulnerable. Even systems that aren't normally considered cryptographic still use cryptography in ways that aren't direct or obvious to end users. That means that even these environments could be vulnerable to a Cryptographically Relevant Quantum Computer (CRQC). One of the biggest risks exposed by the drive towards quantum computing is the erosion of trust in compute platforms. Consider this impact on:
- Hardware roots of trust depend on Secure Boot, TPMs, FIDO and a host of cryptographically protected mechanisms which are in place to prevent data theft. This includes the edge devices running factories and collecting data from the field.
- Software distribution (include web-based services) and signing systems that instill trust for you to run and use them - but many of these systems haven't changed in decades as there hasn't been a need!
- Your data and your identity, including property, health, financial records and cryptocurrency, all of which depend on electronic records and transfer systems.
- The telecommunications and online services that form the daily fabric of web sites, e-commerce, social media, cell phones and 5G - social media and other online profiles were created to last, with Facebook alone having existed for 20 years.
The timeframes for cryptography usage are already overlapping with the probable timeframes for the introduction of CRQCs. These means that cryptography as we know it needs to evolve.
Embracing post-quantum cryptography
The world needs to analyze and, where necessary, replace vulnerable cryptosystems with post-quantum alternatives. Red Hat recognizes this need and is already working with leading organizations like NIST and IBM to standardize and implement post-quantum encryption. Unlike the powerful quantum computers still in development, post-quantum cryptography is available now. By adopting these evolutions, you can work towards better protecting your data from current and future threats.
"Determining where migration to post-quantum cryptography will be required involves certain initial discovery steps for the development of migration roadmaps. These include the identification of affected standards by standards developing organizations (SDOs) and consortia, and the identification of critical applications and protocols on both an enterprise and sector-wide basis" — NIST
Red Hat is your trusted partner
The open source community is building and testing implementations of the NIST finalist algorithms to evaluate the drop-in suitability for existing cryptosystems like RSA or ECDSA. This includes assessing performance and other characteristics of these implementations to both improve them and measure potential impacts to dependent systems. As a trusted enterprise and platform provider, Red Hat has a long history of helping organizations adopt leading enterprise IT technologies, from Linux and containers to Kubernetes and serverless; alongside these platforms, we also help IT teams build and refine their security posture around these advances.
Our approach is no different when it comes to cybersecurity in a post-quantum world. We're already updating adjacent standards and technologies and preparing our next-generation operating system and layered platforms to support and offer post-quantum cryptography. With Red Hat, you can navigate the complex transition to a quantum-ready world with less disruption while gaining a stronger security posture to address these new challenges.
An example of this drive is the openquantumsafe.org open source community, which is already testing and evaluating the performance of post-quantum cryptography (PQC) alternatives.
The challenges of quantum cryptography
The migration to post-quantum cryptography is a monumental task that requires meticulous planning and execution. Red Hat is focused on tackling these challenges head-on because of just how broadly the impact is on IT at-large. It's critical to have targeted solutions ready to address specific concerns at each phase of the migration cycle.
- As regulatory and certification organizations like NIST aren't ready to finalize algorithms and systems based on these advancements yet, early adopters must be prepared to restart or revert migrations mid-stream. Early solutions may need to focus on agility to reduce the time required to transition to alternatives and to allow for easier updates for future cryptographic standards, should the need occur.
- Modern IT is central to virtually all aspects of companies, industries and missions. IT sprawl creates a challenge of scale when it comes to transitioning to post-quantum cryptography, which means operations will include mixed and hybrid cryptographic environments some time. Automating the assessment and evaluation process can help drive priorities with data and evidence, leading to targeted migrations of individual systems.
- Being able to continue business operations during this disruptive process will be paramount. IT teams need to frequently analyze and assess the operational risk and impact to systems, which can help prevent cryptography modernization from stalling or stopping altogether. Early solutions that can layer over existing security technologies and work with existing protocols in mixed deployments will be needed, as well as specialized tools to test and validate and measure the performance, cost, scale and overall impacts of these new cryptosystems to enterprise systems
Preparing to be quantum-ready with Red Hat
Partnering with IBM and organizations like QuSecure, Red Hat is extending our ecosystem and communities to advance the enterprise approach for quantum-ready technology. The goal is to extend our existing validated solutions that help protect your data streams today while preparing you for the future.
It's important to not wait for quantum computing to pose a problem to your sensitive data. With Red Hat, you can start the journey towards a quantum-ready world today - our experts can discuss the use of cryptography in your enterprise and Red Hat estate today, and help show you how you can start down a migration path today.
Red Hat's platform experts have worked with the QuSecure team to build upon proven Red Hat platforms including Red Hat Enterprise Linux (RHEL), Red Hat OpenShift and Red Hat Ansible Automation Platform. This allows you to build on trusted Red Hat platforms and deploy your solutions with, and into enterprises already using, leading enterprise open source technologies. By decoupling encryption layers and using our trusted platforms, you can better adapt to post-quantum cryptography while limiting the disruption to existing systems.
Contact Red Hat today to learn more about the state of post quantum cryptography standards and the tools that help you experiment with these emerging standards today, identify your high-value systems that depend on cryptography, and start prioritizing and planning for your own enterprise transition. Visit red.ht/ic to learn more.
À propos de l'auteur
Contenu similaire
Parcourir par canal
Automatisation
Les dernières nouveautés en matière d'automatisation informatique pour les technologies, les équipes et les environnements
Intelligence artificielle
Actualité sur les plateformes qui permettent aux clients d'exécuter des charges de travail d'IA sur tout type d'environnement
Cloud hybride ouvert
Découvrez comment créer un avenir flexible grâce au cloud hybride
Sécurité
Les dernières actualités sur la façon dont nous réduisons les risques dans tous les environnements et technologies
Edge computing
Actualité sur les plateformes qui simplifient les opérations en périphérie
Infrastructure
Les dernières nouveautés sur la plateforme Linux d'entreprise leader au monde
Applications
À l’intérieur de nos solutions aux défis d’application les plus difficiles
Programmes originaux
Histoires passionnantes de créateurs et de leaders de technologies d'entreprise
Produits
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Services cloud
- Voir tous les produits
Outils
- Formation et certification
- Mon compte
- Assistance client
- Ressources développeurs
- Rechercher un partenaire
- Red Hat Ecosystem Catalog
- Calculateur de valeur Red Hat
- Documentation
Essayer, acheter et vendre
Communication
- Contacter le service commercial
- Contactez notre service clientèle
- Contacter le service de formation
- Réseaux sociaux
À propos de Red Hat
Premier éditeur mondial de solutions Open Source pour les entreprises, nous fournissons des technologies Linux, cloud, de conteneurs et Kubernetes. Nous proposons des solutions stables qui aident les entreprises à jongler avec les divers environnements et plateformes, du cœur du datacenter à la périphérie du réseau.
Sélectionner une langue
Red Hat legal and privacy links
- À propos de Red Hat
- Carrières
- Événements
- Bureaux
- Contacter Red Hat
- Lire le blog Red Hat
- Diversité, équité et inclusion
- Cool Stuff Store
- Red Hat Summit

