Automation can help increase efficiency, save time, and improve consistency, which is why Red Hat Enterprise Linux (RHEL) includes features that help automate many tasks. Two technologies that work together to improve your container workflow are RHEL system roles and the Red Hat Insights image builder. Recently, Insights image builder introduced the ability to define a first boot configuration script that gets run the first time a system boots up from an image. This first boot script can be utilized for a variety of use cases, including to configure a newly created host with RHEL system roles.
In this article, I demonstrate how to use an Insights image builder first boot script to run the timesync, fapolicyd, journald, and cockpit system roles to configure several aspects of systems provisioned from the image.
Creating the blueprint with Insights image builder
A RHEL system role is a collection of Ansible content providing consistent workflows, and streamlining the execution of otherwise manual tasks.
Insights image builder enables you to create a custom RHEL image for a variety of platforms, including cloud providers, virtual machines, and bare metal. Images can be customized with custom packages, file system layouts, and OpenSCAP compliance policies. You can access the Insights image builder from the Red Hat Hybrid Cloud Console. To try the first boot script configuration, enable Preview mode at the top of the screen (this feature will transition out of Preview status soon, so this step is temporary).
Start by creating a new blueprint. Select the version of RHEL and target environments you want to use for the image.
On the registration step of image builder, it's recommended that the system be registered with Red Hat when using RHEL system roles in the first boot script. This enables the system roles to install additional packages as necessary. For example, the fapolicyd system role installs packages required for fapolicyd. If the Register later option is selected, most of the system roles would fail, unless all the required packages are also included in the image.
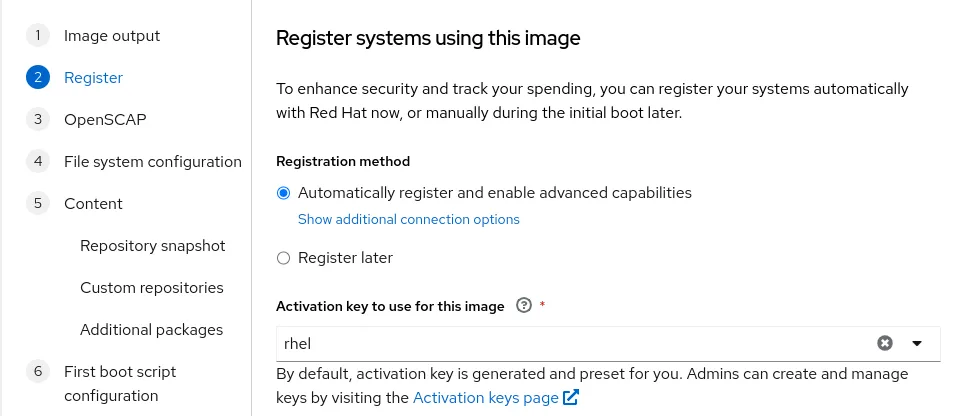
Additional settings can be configured within Insights image builder related to the OpenSCAP compliance policy and file system configuration.
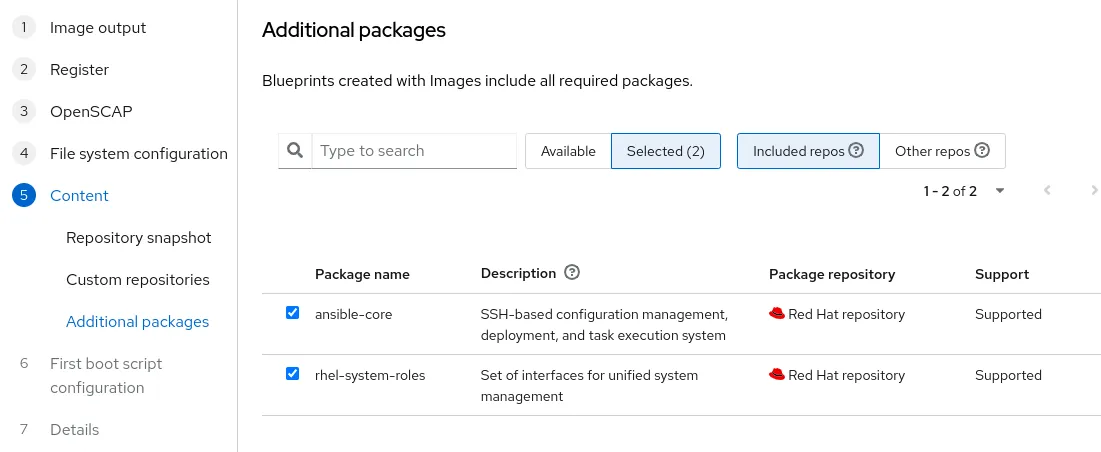
To use RHEL system roles in your first boot configuration script, the ansible-core and rhel-system-roles packages must be added to the image during the Content step.
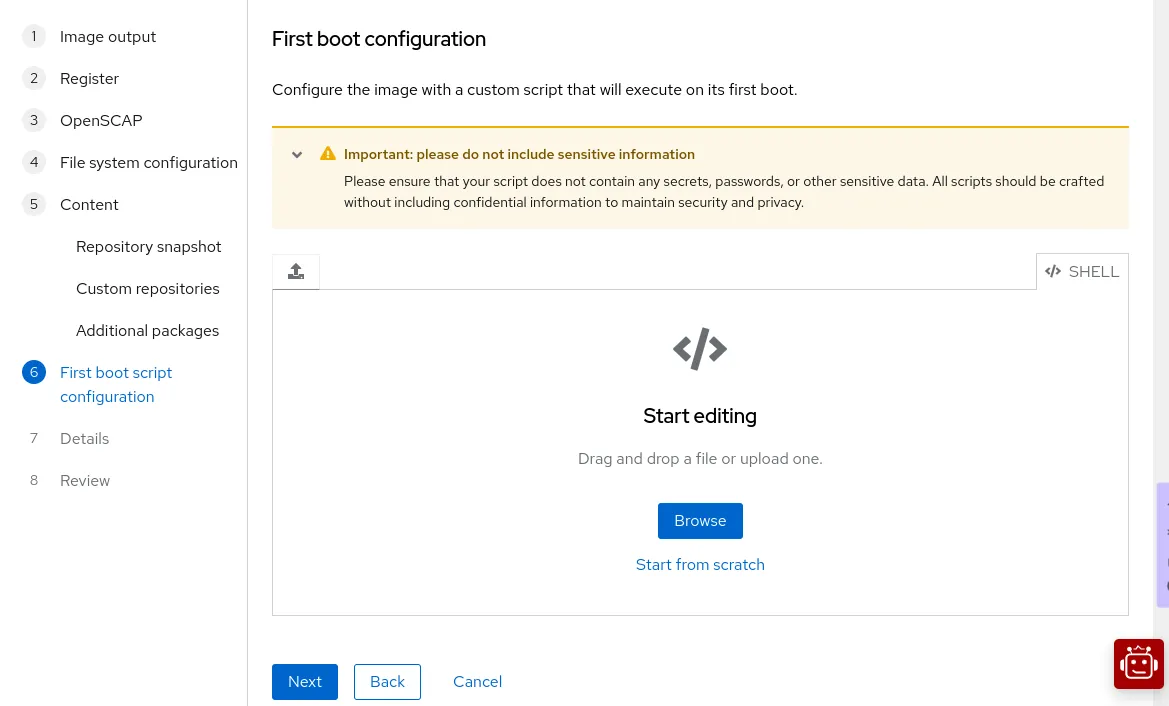
On the First boot configuration step, you can upload a first boot script, or just paste it into the editor. Do not include sensitive information in your first boot configuration.
Here's my example script:
#!/usr/bin/ansible-playbook -i localhost,
- name: Run RHEL system roles
hosts: localhost
connection: local
tasks:
- name: Run timesync RHEL system role
vars:
timesync_ntp_servers:
- hostname: ntp1.example.com
iburst: true
- hostname: ntp2.example.com
iburst: true
import_role:
name: redhat.rhel_system_roles.timesync
- name: Run fapolicyd RHEL system role
vars:
fapolicyd_setup_integrity: sha256
import_role:
name: redhat.rhel_system_roles.fapolicyd
- name: Run journald RHEL system role
vars:
journald_persistent: true
import_role:
name: redhat.rhel_system_roles.journald
- name: Run cockpit RHEL system role
vars:
cockpit_manage_firewall: true
import_role:
name: redhat.rhel_system_roles.cockpit
This uses RHEL system roles to configure two NTP servers with the timesync system role, enables fapolicyd including SHA256 integrity checking, configures systemd to have persistent logging for the journal, and enables the RHEL web console on the system (which includes a firewall configuration that allows connections to the RHEL web console).
After your script is added, proceed through the rest of the Insights image builder steps to create the blueprint, and then to build an image from the blueprint.
Deploy and test the image
The steps to provision a system from the image vary depending on the target platform. For more information, refer to the Insights image builder documentation.
Once a system is provisioned from your image, log in to the system to verify that the first boot script using the RHEL system roles has properly configured it. The first boot script is implemented using a oneshot type systemd service named custom-first-boot.service.
If you log in to the system very quickly after it is provisioned, the first boot script might not have finished running yet. You can see the status of the script with the systemctl status custom-first-boot command. In the following example, the script is still running, which you can identify by the Active line:
# systemctl status custom-first-boot
• custom-first-boot.service - Run first boot script
Loaded: loaded (/etc/systemd/system/custom-first-boot.service; enabled; preset; disabled)
Active: activating (start) since Thu 2024-08-08 16:46:46 EDT; 31s ago
Main PID: 1230 (custom-first-bo)
[...]
Once the script completes, the output on the Active line changes:
# systemctl status custom-first-boot
• custom-first-boot.service - Run first boot script
Loaded: loaded (/etc/systemd/system/custom-first-boot.service; enabled; preset; disabled)
Active: inactive (dead) since Thu 2024-08-08 16:48:46 EDT; 18s ago
Main PID: 1230 (code=exited, status=0/SUCCESS)
[...]
Aug 08 16:48:14 localhost.localdomain systemd[1]: custom-first-boot.service: Deactivated successfully.
Aug 08 16:48:14 localhost.localdomain systemd[1]: Finished Run first boot script.
[...]
If you need to troubleshoot a script, use the journalctl -u custom-first-boot command to see more information.
For my example, I was able to verify that the configuration I'd specified was implemented, starting with the NTP server configuration:
# cat /etc/chrony.conf | grep ntp server ntp1.example.com iburst server ntp2.example.com iburst
I also verified that fapolicyd was installed and running with the systemctl status fapolicyd command and that the SHA256 integrity mode was configured:
# cat /etc/fapolicyd/fapolicyd.conf | grep integrity integrity = sha256
I also verified the persistent systemd journal configuration:
# cat /etc/systemd/journald.conf.d/99-linux-system-roles-journald.conf | grep Storage Storage=persistent [root@localhost ~]# ls -al /var/log/journal/34167acd7c444a32b2448e5f198b4dff/ total 8192 drwxr-sr-x+ 2 root systemd-journal 28 May 16 16:48 . drwxr-sr-x+ 3 root systemd-journal 46 May 16 16:48 .. -rw-r-----+ 1 root systemd-journal 8388608 May 16 16:53 system.journal
And finally, I verified that I could successfully access the RHEL web console on port 9090:
Combined technologies for better administration
The Insights image builder first boot configuration functionality opens up many exciting possibilities, including the ability to have RHEL system roles configure newly provisioned hosts at first boot. I only demonstrated a few of the available system roles in this article, so look through the list of available RHEL system roles to find the ones most useful in your environment. When you're ready to create your own custom RHEL image, head over to Insights image builder and get started!
关于作者
Brian Smith is a Product Manager at Red Hat focused on RHEL automation and management. He has been at Red Hat since 2018, previously working with Public Sector customers as a Technical Account Manager (TAM).
更多此类内容
产品
工具
试用购买与出售
沟通
关于红帽
我们是世界领先的企业开源解决方案供应商,提供包括 Linux、云、容器和 Kubernetes。我们致力于提供经过安全强化的解决方案,从核心数据中心到网络边缘,让企业能够更轻松地跨平台和环境运营。

