Early in my sysadmin story, there were few things that felt quite as intimidating as my first Linux install. After all of the hard work (and it was hard work at the time) figuring out how to install things, I was faced with that black terminal with a simple login: prompt.
Today, the Linux experience is a lot easier than it was then, but that login prompt can still be daunting. Lucky for you, I'm here to help you figure out several ways to get to a command prompt on your new Red Hat Enterprise Linux (RHEL) system (and most Linux systems today).
Access your physical or virtual console
If you're at the physical console (or in the case of a virtual machine, the virtual console), you'll either get a login prompt (if the system defaults to the multi-user.target) or a nice GNOME login window (if it defaults to the graphical.target).
Using text mode (or multi-user.target)
If you're used to a friendly graphical user interface (GUI) greeting you at first boot, the text-mode login may look a little foreign, but you've got this.
For many reasons, your system may be configured to boot to a text login. This is called multi-user mode. If you install Linux using the minimal package set, it won't have a graphical mode at all. You can also set the system to default to multi-user, even if a GUI is there.
Getting to a prompt is easy. Just enter your username (don't forget it's case-sensitive; gangrif and Gangrif are not the same). Press Enter, and then type your password. Don't panic if you do not see any stars or other input as you type; Linux doesn't display any password placeholder characters.

Using the GUI (or graphical.target)
If you installed your system using the defaults, it should include the X Window System, which is the GUI included with RHEL. The login looks as you might expect. Just select your username in the list to be prompted for your password. Type the password (you will see dots as you enter your password here, unlike at the text login) and press the Sign In button.
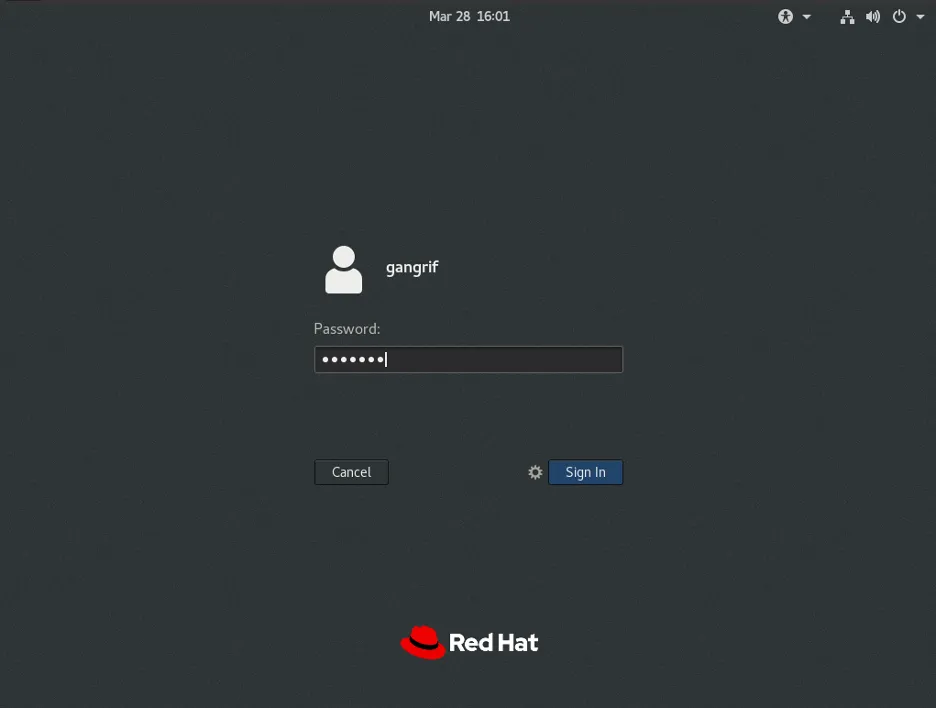
This process gets you to the desktop, but you're not at a command prompt yet, and that's the goal here. Click on the Activities menu in the upper-left.

Now click on the Terminal icon in the side menu in GNOME shell.

This step launches the GNOME Terminal, and now you're at a command prompt.

[ Free eBook: Manage your Linux environment for success. ]
Remote access over Secure Shell (SSH)
That's all great if you're at the actual console, but what if you're remote? Good news. Linux in text-mode configuration offers an almost identical experience when accessing the system remotely. It's one of the reasons I love Linux so much.
There's not much you can do from the console that you can't also do remotely. There are many options for the client-side here, and I cannot cover them all. I will assume you are accessing your system from another Linux terminal. All you need to know is your username, password, and the remote system's IP address (or hostname). From a Bash shell, just type the following:
$ ssh gangrif@192.168.122.61
The authenticity of host '192.168.122.61 (192.168.122.61)' can't be established.
ED25519 key fingerprint is SHA256:FnYX5btiPuKlcFlfqvlU2wJiWvWmPjLPvmod4GbuKgk.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.122.61' (ED25519) to the list of known hosts.
gangrif@192.168.122.61's password:
Activate the web console with: systemctl enable --now cockpit.socket
Register this system with Red Hat Insights: insights-client --register
Create an account or view all your systems at https://red.ht/insights-dashboard
Last login: Mon Mar 28 16:02:09 2022
The first time you connect to a new system over SSH, you are asked if you would like to accept the remote system's fingerprint. Your SSH client will save this fingerprint and prevent you from connecting if it changes. Explaining how this exchange works is beyond the scope of this article, though.
And that's it! Now you're on the remote system. I do recommend one more thing: SSH password authentication, like I just demonstrated, is OK, but it opens your system up to brute-force password attempts. This configuration is fine for a lab or study environment, but you may want to harden SSH and disable password authentication if you're managing real servers.
But then how do you authenticate to your system? You use key-based authentication. This approach uses a public and private key pair. Generating one is as simple as using the command ssh-keygen. You can choose to set a password for the key pair. The password locks the local private key, not the remote server. You can then copy your public key to the remote system with ssh-copy-id or do it manually. You can read Using ssh-keygen and sharing for key-based authentication in Linux for more on this topic.
Exit or log out of the terminal
Whichever method you use to get to a terminal, there are a few ways to disconnect from it properly. You can type either exit or logout and press Enter. Or you can press CTRL+D on your keyboard. If you're at the console and have a terminal window open, you can also just close it, but I consider it better to log out with one of the commands or keyboard shortcuts above.
Wrap up
Whether you're taking a certification exam or managing a Linux system, terminal access is essential. If your system boots to the command-line interface (CLI) by default, access is as simple as logging in. A GUI environment requires a login and then browsing to the Terminal application. Remote access over SSH gives a very similar experience to a CLI login. Don't forget to configure SSH key-based authentication if you're managing production systems.
Sobre el autor
Nate is a Technical Account Manager with Red Hat and an experienced sysadmin with 20 years in the industry. He first encountered Linux (Red Hat 5.0) as a teenager, after deciding that software licensing was too expensive for a kid with no income, in the late 90’s. Since then he’s run everything from BBS’s (remember those?) to derby hat’s containing raspberry pi’s, to Linux systems in his basement, or in enterprise-class data-centers.
He runs his own blog at undrground.org, hosts the Iron Sysadmin Podcast, and when he’s not at a command line, he’s probably in the garage tinkering on his Jeep, or out on the trails.
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Programas originales
Vea historias divertidas de creadores y líderes en tecnología empresarial
Productos
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Servicios de nube
- Ver todos los productos
Herramientas
- Training y Certificación
- Mi cuenta
- Soporte al cliente
- Recursos para desarrolladores
- Busque un partner
- Red Hat Ecosystem Catalog
- Calculador de valor Red Hat
- Documentación
Realice pruebas, compras y ventas
Comunicarse
- Comuníquese con la oficina de ventas
- Comuníquese con el servicio al cliente
- Comuníquese con Red Hat Training
- Redes sociales
Acerca de Red Hat
Somos el proveedor líder a nivel mundial de soluciones empresariales de código abierto, incluyendo Linux, cloud, contenedores y Kubernetes. Ofrecemos soluciones reforzadas, las cuales permiten que las empresas trabajen en distintas plataformas y entornos con facilidad, desde el centro de datos principal hasta el extremo de la red.
Seleccionar idioma
Red Hat legal and privacy links
- Acerca de Red Hat
- Oportunidades de empleo
- Eventos
- Sedes
- Póngase en contacto con Red Hat
- Blog de Red Hat
- Diversidad, igualdad e inclusión
- Cool Stuff Store
- Red Hat Summit

