Things can be pretty scary out there today. There are a lot of things that could occur that make even the calmest amongst us take pause. Everything we do is a series of risk-based decisions that we hope leads to happy outcomes. “Should I get out of bed today?”, “Should I eat this sushi they are selling in this gas station?”, “Can you hold my beverage?”. The challenges of modern-day existence can be very daunting.
With this blog, I’m sharing how I’d advise organizations to consider IT-related risks and how Red Hat Product Security aims to help customers make informed decisions with data.
In the world of information security, we have a few tools to help us make informed decisions. When looking at potential problems we think of them in terms of potential risks that could happen that would impact our business. First, when we need to understand what could possibly happen, we look at the impact of a potential threat. IF I don’t have any ice available on this hot summer day, I COULD have a dissatisfactory chilly-beverage experience. That sounds pretty bad, right? I’d be very disappointed if that risk (the inadequate supply of ice) was unable to slake my summer-y, adventure-fueled thirst (the impact or possible bad outcome).
The lack of frozen water might not be my only problem in venturing outside. Do I have sunscreen? Do I have my trusty adventure hat? What if it rains? What if it gets windy and I get a non-frosty-beverage-induced chill? It’s a great idea to maybe track these problems (risks) and the potential bad outcomes (impacts) down in something like my handy, dandy notebook (or a risk register).
Once you’ve written down what you feel is a solid list of things that could happen, you might notice that some of the problems are bigger or smaller than others. Getting sunstroke from lack of appropriate protection is bad, far worse than say not having a coaster for this quickly-warming drink. Some of these problems are measurable (quantifiable) while others are more about how you feel about it (aka “the feels”) (qualifiable). Either approach is valid depending on what the data is and what decisions you’d like to make, but you want to make sure you’re using the same measuring stick so that your analysis is consistent. The whole “comparing apples to oranges” debate of the ages, you know?
As you’re thinking about how bad these items could be, it is important to think about it in three dimensions:
-
Does this problem allow someone to look at something they shouldn’t? (Confidentiality)
-
Does this problem make it so people that should see the data cannot? (Availability)
-
Does this problem alter the data in a manner it should not be? (Integrity)
So you’ve got a list. You have some scale to measure how bad the outcomes potentially could be. Another element to look at is the likelihood or probability of those bad possible outcomes actually happening. While you may be naturally afraid of sharks, the realistic chance one will swim up to your back porch, take off it’s snorkel mask, and start nibbling on you is very, very unlikely (....I hope). Flipping to a new page in your handy dandy notebook you can plot each risk on an X/Y scale as shown here:
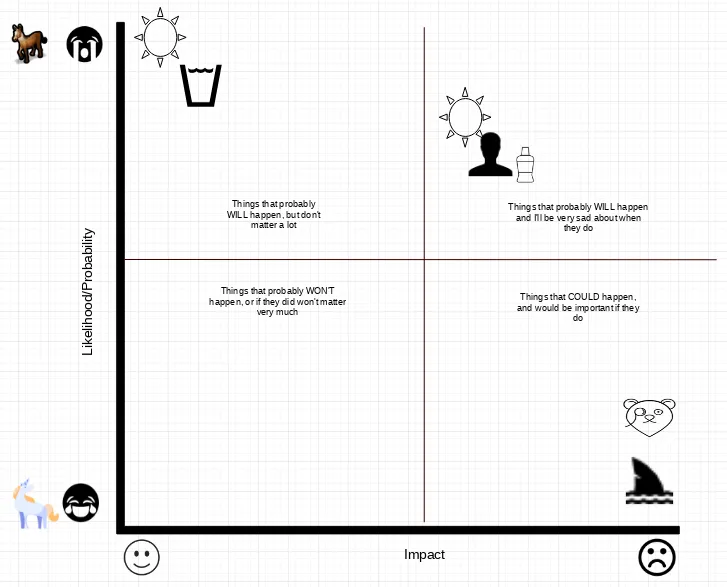
Here in this chart, we’ve plotted the likelihood and impact of not having a coaster, getting sunstroke, and the aforementioned toothy visitor.
To throw more wacky wildlife analogies into this discussion, ideally this gets you thinking about the threat - a hairy, scary bear coming and eating your sandwich, what the vulnerability is - there is a hole in your bear-proof fence, and what the impact would be if that threat exploits that vulnerability - you has no more tasty sammich since the shark and bear teamed up on you to gobble it up nom nom nom, plus you’re also out of ice and your beverage is getting dangerously close to room-temperature! (The horror!)
Risk = Threat x Vulnerability
So this is where you break out science and math to help you decide what to do. There is a concept of a “single loss expectancy” (SLE), in layman’s terms this is “what is the cost if this bad thing happens once?” So back to our busy and hot back porch example, we have lost one sandwich (tragic, I know). That doesn’t sound too bad. What if this terrible series of events unfolds every day, then you look at your risk in terms of “annualized rate of occurrence” (ARO). Every day is a pretty intense probability (like 100%, which sounds like a lot). With those two points of data, we can then state what our “annual loss expectancy” (ALE) is.
ALE = SLE x ARO
So for our example, that’s one sandwich (perhaps also an additional investment in anti-shark spray and bear-netting) multiplied by 365 days. So that’s quite a large pile of deli meats, cheeses, and bread, don't you agree?
You invest in some countermeasures: the anti-shark spray, some bear netting, and those little tents you put over outdoor food to keep the bugs off of them (and a bag of ice from the local A&P down the street). So that costs you, like $3.50 a year. To get fancier, let’s say this travesty of sandwich abuse (and lukewarm drinks) goes on for several years. So you have dozens of dollars wrapped up in trying to stop these animal hooligans. Sounds like we might want to evaluate if we’re spending the right amount for the value we’re receiving.
COST_of_COUNTERMEASURE = ALE_ORIGINAL - ALE_NOW
You generally should not spend more money to protect something than what this is worth to you (now to be fair, things like human safety and not breaking the law will typically override this calculus) but it may be cheaper to just stop doing this risky activity than it would be to continue doing it and paying to protect it.
When you’re thinking about these risks in your handy dandy notebook or on your porch, there are several techniques that can help you deal with it. There are four ways any risk can be addressed:
-
You can try and correct it and make it go away (but this can be expensive) - Buy an electric bear & shark-proof fence with teeny-tiny mesh so they can’t slip in.
-
You can try to reduce it to make it smaller and less scary - make the hole in the fence smaller, so the bear has to work harder to get in and maybe he’s too tired to eat the whole sandwich, so you still have a bear-slobbery half left.
-
You can transfer the risk and make it someone else’s problem- sell the house and hope the buyer doesn’t go out back during the home inspection.
-
Or...you can accept the risk and just live with it - I, for one, welcome our new shark-riding bear overlords.
You can NEVER eliminate ALL risk from something. Even if you correct/remediate a problem, there could be other factors or exploits that are unknown at that time, or you might not have enough time/effort/money to purge the problem entirely. Working smarter, you can temper how you address a problem; maybe by selectively applying mitigations where the resource or performance costs are too high (or accepting the risk if the cost is too painful) or doing a risk-based analysis and applying fixes to critical assets first, then working your way down to less important (or inconsequential) systems. As the poet once said, “If you chose not to decide, you still have made a choice.”
Now all this merry conversation around ice and bears and landsharks is all well and good, but you might say “Self, what does this all do to help ME?”
From Sandwiches to Security
Well here is the turn: Red Hat Product Security works to provide you clear factual data as we understand it, to help you understand how big those bears are, how fast those sharks are swimming, and how hot it is outside so that you can be armed to know how much ice you’ll need to hit that perfect 50-70 degrees Fahrenheit of frosty wet goodness and how much mayo you might need for that sub sandwich (hint...none). Red Hat can help you understand what a vulnerability is, and give you options to address it, but ultimately you know your sandwich best, and your preferred sandwich is different than your neighbor’s or that guy’s down the street.
Once embargoes are lifted, Red Hat publishes our security data and metrics openly for everyone to see. Each vulnerability is clearly labeled using industry-standard tools and measurements like Common Vulnerabilities and Exposures (CVE), Common Weakness Enumeration (CWE), and Common Vulnerability Scoring System (CVSS). We publish that data in both human-readable and machine-readable formats like Open Vulnerability and Assessment Language (OVAL) and Common Vulnerability Reporting Framework (CVRF).
We work to describe the problem and provide our assessment of the severity of the issue by providing an additional impact rating on top of a score like CVSS. Our engineers look at each flaw from the vantage point of our products based on the components and how those packages are used and configured. We have the experience to know when a flaw is just a little guppie and when it truly is a megalodon that will ruin your day. On top of that, we have our internal Customer Security Awareness program that layers on additional data, context, and tools to help you quickly decide what you need to do within the context of your operating and business environment.
Hopefully, this helps you understand where and how you should react and be able to articulate YOUR business’ risk to YOUR stakeholders so the next time that bear-shark combo swims by you can act quickly and confidently with your response.
Christopher Robinson oversees product security assurance at Red Hat.
Sobre el autor
Christopher Robinson, better known as CRob to his colleagues, is a former Product Security Program Architect at Red Hat.
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Programas originales
Vea historias divertidas de creadores y líderes en tecnología empresarial
Productos
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Servicios de nube
- Ver todos los productos
Herramientas
- Training y Certificación
- Mi cuenta
- Soporte al cliente
- Recursos para desarrolladores
- Busque un partner
- Red Hat Ecosystem Catalog
- Calculador de valor Red Hat
- Documentación
Realice pruebas, compras y ventas
Comunicarse
- Comuníquese con la oficina de ventas
- Comuníquese con el servicio al cliente
- Comuníquese con Red Hat Training
- Redes sociales
Acerca de Red Hat
Somos el proveedor líder a nivel mundial de soluciones empresariales de código abierto, incluyendo Linux, cloud, contenedores y Kubernetes. Ofrecemos soluciones reforzadas, las cuales permiten que las empresas trabajen en distintas plataformas y entornos con facilidad, desde el centro de datos principal hasta el extremo de la red.
Seleccionar idioma
Red Hat legal and privacy links
- Acerca de Red Hat
- Oportunidades de empleo
- Eventos
- Sedes
- Póngase en contacto con Red Hat
- Blog de Red Hat
- Diversidad, igualdad e inclusión
- Cool Stuff Store
- Red Hat Summit

