Red Hat Summit, the premier open source event, reached new heights this past May by ascending to the Mile High City of Denver Colorado. The mix of Red Hat customers, enthusiasts and members of the open source community made for an ideal location for the latest OpenShift Commons Gathering. Similar to other OpenShift Commons Gathering events, it occurred as a day-0 event prior to the actual start of Red Hat Summit. But, what made this event extra special was that it also coincided with the first ever Community Day that brought together the communities driving Red Hat OpenShift, Red Hat Enterprise Linux (RHEL) and Red Hat Ansible Automation Platform in one location. Community Day at Red Hat Summit was chock full of everything that one could expect when bringing together several vibrant communities: keynotes, announcements, use cases and, most importantly, collaboration.
Included in the festivities were a series of workshops led by members of several OpenShift Commons Special Interest Groups (SIGs) . These interactive sessions associated with some of the most active SIGs each featured SIG leaders, Red Hat Consulting and Red Hat’s User Experience team and enabled members of the community to share their experiences, triumphs, challenges and future plans for each topic.
The SIGs that participated in these workshops included those that one might expect to find these days: Platforms, AI and Edge. A topic area that is cross-cutting and plays a role in each of the aforementioned SIGs is security. Andy Braren, Sean Rickerd, Michelle DiPalma and I represented the OpenShift Commons Security SIG for a workshop focused specifically on the security aspects of OpenShift, including the platform and the surrounding ecosystem, along with best practices, methodologies and teams. Enhancing the security capabilities of OpenShift at a platform level is just the tip of the iceberg, especially considering the range of applications being explored and how they are being used. As OpenShift and Kubernetes continue the journey of becoming a standard offering within organizations big and small, security plays an even greater role as organizations continue evolving their IT practices and technology in a challenging landscape.
Now, recall when I mentioned that these workshops were interactive — I was not exaggerating. The Security SIG workshop was a far cry from a “death by slides” session. Building upon the overwhelming success of the Security Breakout at the OpenShift Commons Gathering at KubeCon EU in March 2024, many of the same principles and themes were replicated stateside. At the core was the use of electronic surveys which not only enabled real-time feedback, but were used as conversation starters for specific topics.
Think of it like a powder keg with each survey question sparking an explosion of insightful conversation. Participants who chose to provide an answer used their phones, laptops, or any other device to provide their input. The results were shared with the audience in real time and participants were encouraged to voice their reasoning for the answers they provided. This approach generated not only a large amount of data for the results that were gathered, but more importantly, sparked conversations amongst participants and strengthened the community as a whole. It was an incredible experience to witness these honest and transparent discussions. The atmosphere helped participants not feel alone in their journey and to learn from the experts and the community.
The results are in: Exploring the feedback from the community
From both the survey results and the associated conversations, one thing is clear: security continues to be an important topic for those in the OpenShift Commons community. Not only were there great discussions between the attendees and the facilitators, but the core tenets of OpenShift Commons held true as participants from various organizations shared their thoughts and experiences with each other. By enabling this type of partnership, organizations learn how to better make use of OpenShift and solve real-world business challenges.
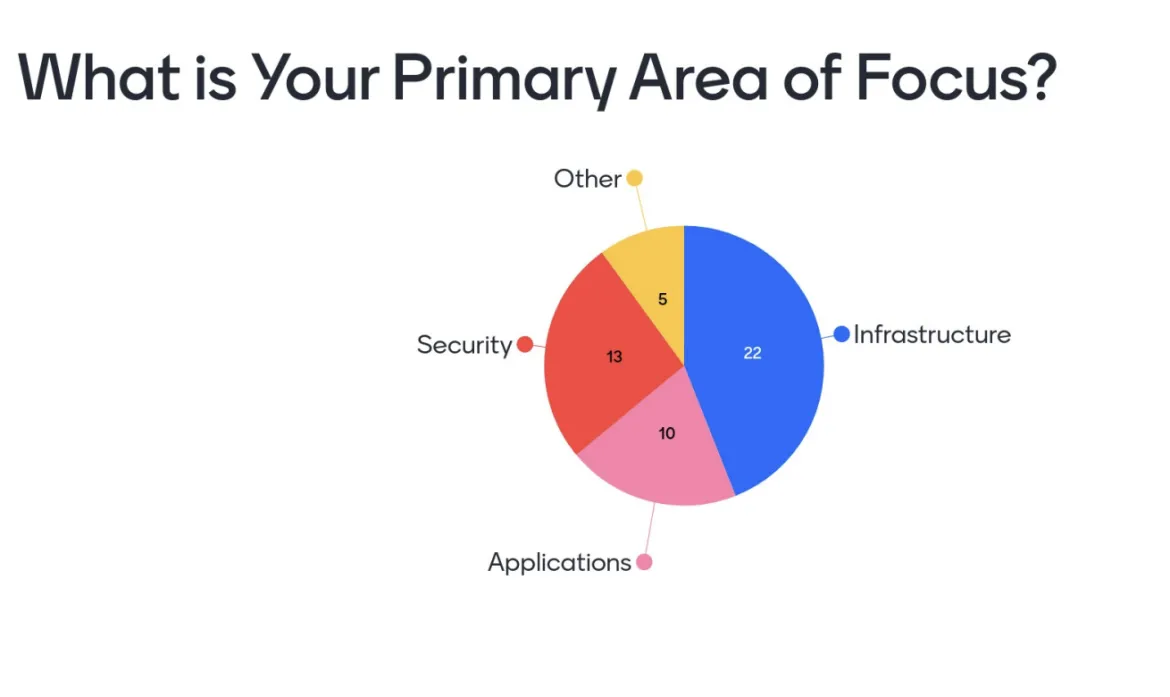
It should not come as a surprise, but in many cases, OpenShift is introduced within an organization from an infrastructure perspective and involves integrating the platform with existing systems and resources, such as monitoring, logging and IT service management (ITSM). That’s why it was especially refreshing to see other personas, particularly from the security perspective, also participate in the workshop.
As organizations look to improve their overall security posture, it is important that security is involved as early in the process as possible so that the platform is designed and implemented with security considerations in mind. Increased participation by security teams may be a side effect of how security-related concerns are viewed within an organization. It was interesting to see that most attendees shared that their organization's security posture was only "fair." One attendee even shared how their organization engages in a practice known as “security theater,” which is an impression of employing security practices instead of following through and actually implementing them within their environment. A cautious tale for all of the attendees.
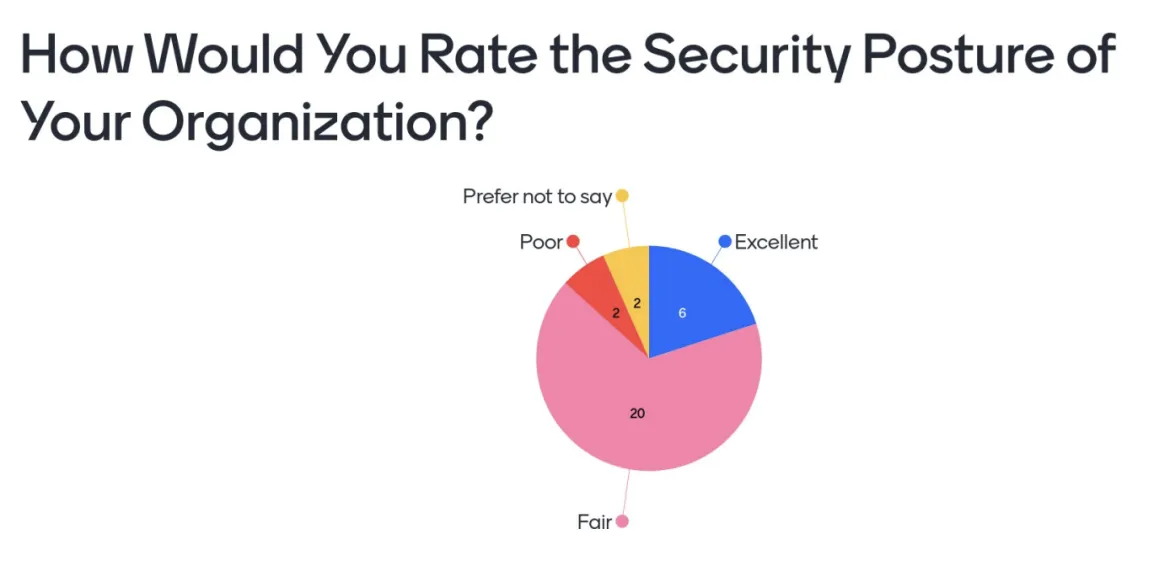
It was not all doom and gloom, however. One participant who specified an “excellent” rating provided an in-depth account of the steps that their organization takes to address security including providing blessed images for development teams to use, enabling continuous scanning of images and even sending “mock” phishing emails to ensure that employees remain vigilant of the ever-changing security landscape. Their tale proved to be a memorable goal post for others to strive for as they harden their own security policies.
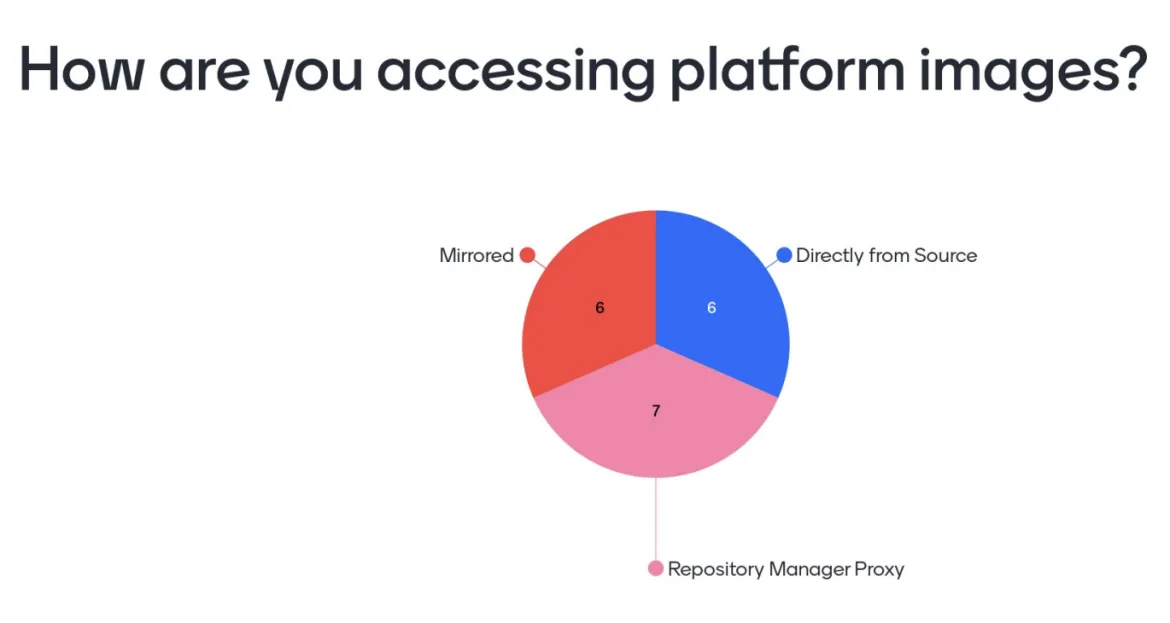
Moving toward the OpenShift-specific security topics, most of the discussions centered around the content that comprises an OpenShift environment, including the base platform itself, operators and end user workloads. Since many of the attendees work within organizations that have strict security standards in place for how content and network traffic is handled, especially from external sources, it was not surprising to see that most are indirectly accessing content to support the platform—whether it be through an HTTP-based proxy, artifact/content repository proxy or sourcing a complete disconnected copy of the resources needed.
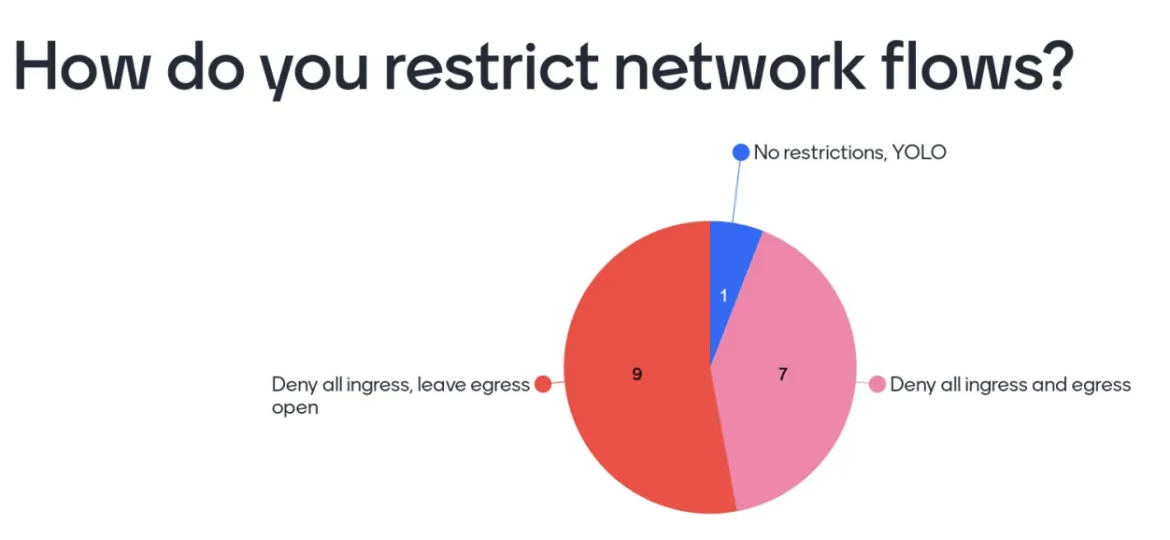
Aside from limiting where content is sourced from, most did respond that they are applying some form of either ingress or egress filtering at the networking level, restricting the types of requests that can be made to and from resources running within the platform.
However, the most fascinating responses and the resulting discussions from the survey questions posed were related to the areas where attendees were currently facing challenges, or in all honesty, struggling entirely.
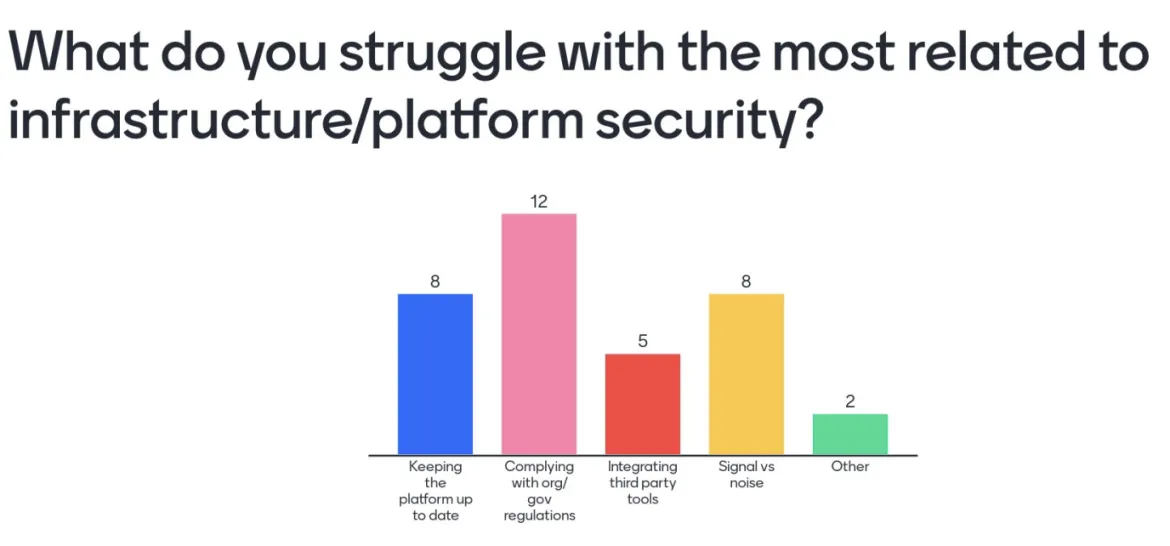
Given that the security landscape continuously evolves, organizational policies and/or government/industry mandates have attempted to react accordingly which has placed additional onus on those managing OpenShift. The combination of these additional policies that these organizations and users must comply with along with just trying to gain a grasp for how to best manage security-related concerns have become a serious burden that has not only consumed a large amount of their time, but limited the set of features and capabilities that can be delivered.
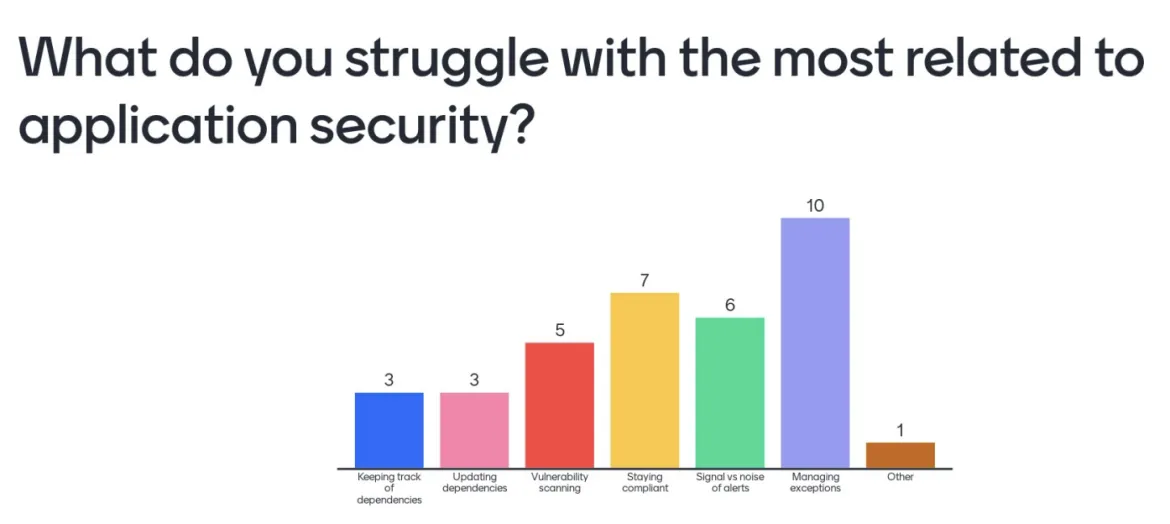
From an application perspective, while there was some overlap in the types of responses as compared to those provided from an infrastructure lens, a pattern that emerged in the responses was that it appeared that instead of security requirements and policies being adhered to directly from the source, say an industry regulation or government mandate, it was ability to adequately manage expectations that were being placed upon each team. This could be anything and everything related to both the previously described areas of concerns, but also the typical bureaucracy that is present in any enterprise organization.
These responses were only just a small portion of the overall set of survey questions posed during the session.
Better securing OpenShift today and tomorrow
As the security landscape continues to evolve, OpenShift and its ecosystem of solutions will evolve with it. One point that was made clear at OpenShift Commons Gathering is that security remains a key priority for those looking to build a platform from both an infrastructure and application perspective. By collaborating as a community through the OpenShift Commons Security SIG, we can work together to continually improve OpenShift's security features.
If you are interested in participating in the OpenShift Security SIG, you can join the conversation on the OpenShift Commons Slack workspace, and you can explore and join our live sessions at https://commons.openshift.org!
Sobre los autores
Andrew Block is a Distinguished Architect at Red Hat, specializing in cloud technologies, enterprise integration and automation.
Sean Rickerd, a distinguished professional in the technology and security domain, seamlessly blends his extensive career journey with a commitment to excellence. From his early days at SUSE to his current role as Principal Technical Marketing Manager at Red Hat, Sean's writing reflects a dedication to continuous learning. With a focus on authoring about cutting-edge fields like DevSecOps and Kubernetes security, he stands at the forefront of driving innovation and elevating security practices.
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Programas originales
Vea historias divertidas de creadores y líderes en tecnología empresarial
Productos
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Servicios de nube
- Ver todos los productos
Herramientas
- Training y Certificación
- Mi cuenta
- Soporte al cliente
- Recursos para desarrolladores
- Busque un partner
- Red Hat Ecosystem Catalog
- Calculador de valor Red Hat
- Documentación
Realice pruebas, compras y ventas
Comunicarse
- Comuníquese con la oficina de ventas
- Comuníquese con el servicio al cliente
- Comuníquese con Red Hat Training
- Redes sociales
Acerca de Red Hat
Somos el proveedor líder a nivel mundial de soluciones empresariales de código abierto, incluyendo Linux, cloud, contenedores y Kubernetes. Ofrecemos soluciones reforzadas, las cuales permiten que las empresas trabajen en distintas plataformas y entornos con facilidad, desde el centro de datos principal hasta el extremo de la red.
Seleccionar idioma
Red Hat legal and privacy links
- Acerca de Red Hat
- Oportunidades de empleo
- Eventos
- Sedes
- Póngase en contacto con Red Hat
- Blog de Red Hat
- Diversidad, igualdad e inclusión
- Cool Stuff Store
- Red Hat Summit



