The Red Hat Enterprise Linux (RHEL) web console is a simplified web-based management tool that lets you manage many aspects of RHEL more efficiently. For more information on the web console and how to get started with it, refer to the Managing systems using the RHEL 9 web console documentation.
RHEL versions 9.2 and 8.8 have a number of new features and enhancements related to the web console, including:
- Support for a dark visual theme
- Several improvements to user and group management capabilities
- The ability to enable network-bound disk encryption on the root filesystem
- Root user account logins are disabled by default on new installs of 9.2+
- Support for configuring virtual watchdog devices on virtual machines
- The ability to insert and remove virtual CD-ROM media on running virtual machines
- The ability to select frequently-used combinations of policies and sub-policies for system-wide crypto policies
- Support for creating Podman pods
- The ability to view disk read and write rates on individual devices
Support for a dark visual theme
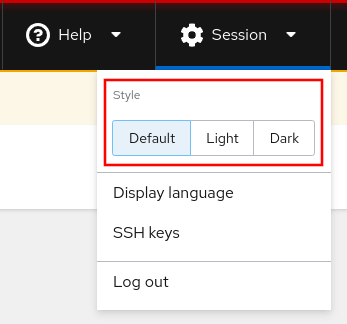
The web console now supports a dark visual theme, which is preferred by many people.

By default, the web console will attempt to detect if your system is configured to use a dark theme, and if so, it will also use the web console dark theme. You can also specify which theme you would like to use by clicking the Session drop down menu in the top right corner of the interface.
Several improvements to user and group management capabilities
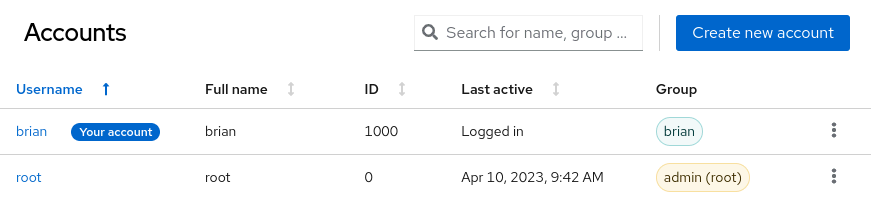
The web console has an updated interface for viewing the list of user accounts on the system, which now supports searching and sorting, as shown in the following screenshot.
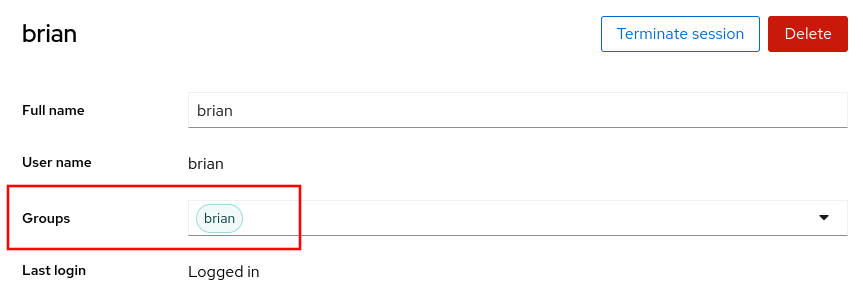
When editing a user account, you can also now add and remove users from groups.
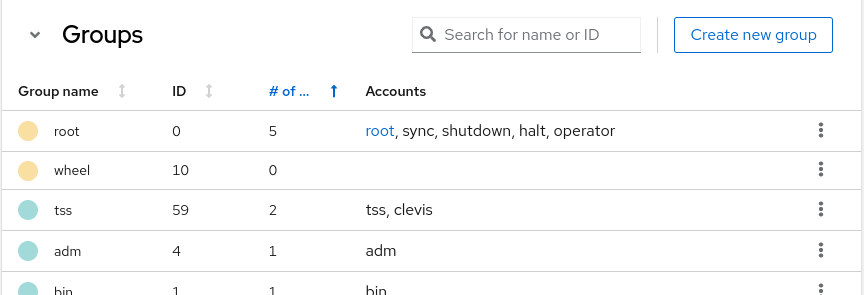
In addition, you can now also view information about the groups on the system, and create new groups.
Ability to enable network-bound disk encryption on the root filesystem
The web console previously supported configuring LUKS encrypted filesystems to bind to a Tang server in order to enable automatic unlocking of encrypted filesystems. However, when configuring this on a root filesystem, the web console previously required users to complete several steps from the command line.
RHEL 8.8 and 9.2 now support configuring the root filesystem to bind to a Tang server from the web console without having to complete any steps manually from the command line. For more information on network-bound disk encryption, refer to the Configuring automated unlocking of encrypted volumes using policy-based decryption documentation.
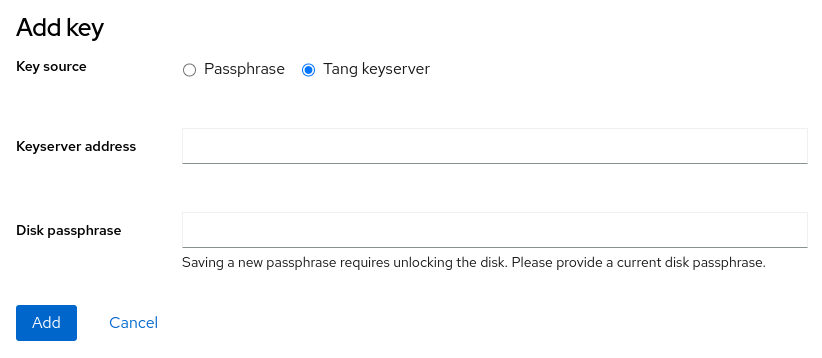
To bind a LUKS encrypted root filesystem to a Tang server, click on Storage in the web console menu. In the right hand menu, click on the drive that contains your root filesystem, press the drop down next to the partition that contains the root filesystem and click on the Encryption tab.
Next, click on the plus sign next to Keys.

You can then select Tang keyserver as the Key source, and type in the keyserver address and existing LUKS passphrase.
Root user account logins disabled by default on new installs of 9.2+
When the web console is installed on RHEL 9.2 or later, it will automatically configure the system to not allow the root user to login to the web console via the Cockpit web server (the cockpit.socket systemd unit). Note that this does not apply to existing RHEL 9.0 or 9.1 systems running the web console that are upgraded to RHEL 9.2 (although after upgrading to 9.2 you can manually configure these existing systems to not allow the root user to login).
The /etc/cockpit/disallowed-users file specifies which users are not allowed to login. On new installations of the cockpit-ws package on RHEL 9.2 or later, this file will be configured to specify the root user account.
# cat /etc/cockpit/disallowed-users # List of users which are not allowed to login to Cockpit root
If you would like to allow the root user to login to the web console, you can edit this file and remove the line for the root user.
Support for configuring virtual watchdog devices on virtual machines
The web console now supports configuring virtual watchdog devices on virtual machines. One common use case for KVM virtual watchdog devices is related to the RHEL High Availability Add-On. For more information see Support Policies for RHEL High Availability Clusters - sbd and fence_sbd.
To configure a virtual watchdog device on a virtual machine (VM), click on Virtual Machines in the web console menu, and then click on the name of a VM in the Overview section. You can see if the VM has a watchdog configured.
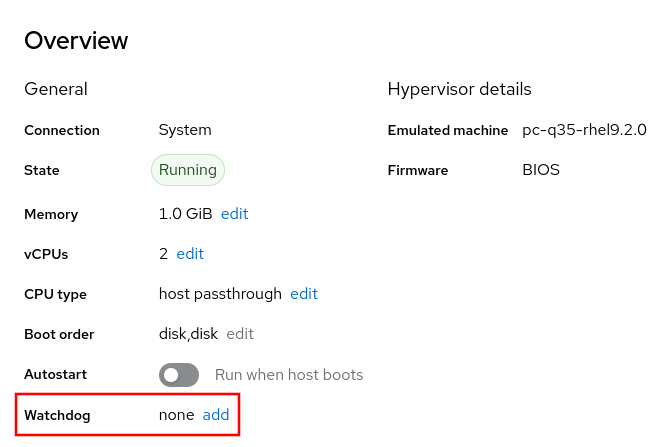
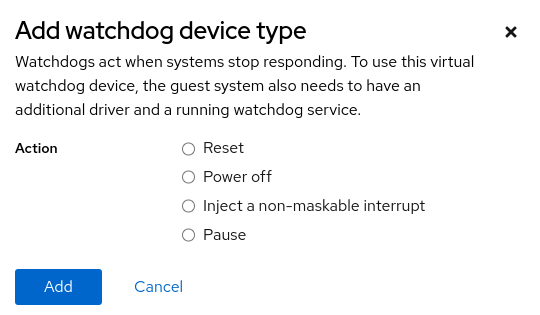
To add a watchdog device, click on the add button. This will then bring up a menu that allows you to specify the watchdog device action.
Ability to insert and remove virtual CD-ROM media on running virtual machines
You can now insert and remove virtual CD-ROM media on a running VM within the web console. Previously, VM’s had to be shut down to complete these tasks.
To manage the virtual CD-ROM media on a VM, click on Virtual Machines in the web console menu, and then click on the name of the VM that you would like to work with.
Find the cdrom device, and click on the Insert button to insert an ISO image into the virtual CD-ROM device.

If there is already an ISO image inserted into the virtual CD-ROM device, you’ll see an Eject button.
Ability to select frequently used combinations of policies and sub-policies for system-wide crypto policies
The system-wide crypto policy support in the web console has been enhanced so you can select frequently used combinations of policies and sub-policies. For more information on system-wide crypto policies, refer to the Using system-wide cryptographic policies documentation.
To select which policy you would like to use, click on Overview in the web console menu. Under the Configuration card, you’ll see a Crypto policy section that shows the currently configured policy.

You can click on the currently enabled policy (Default in the above screenshot) to bring up the menu that allows you to select the desired policy.
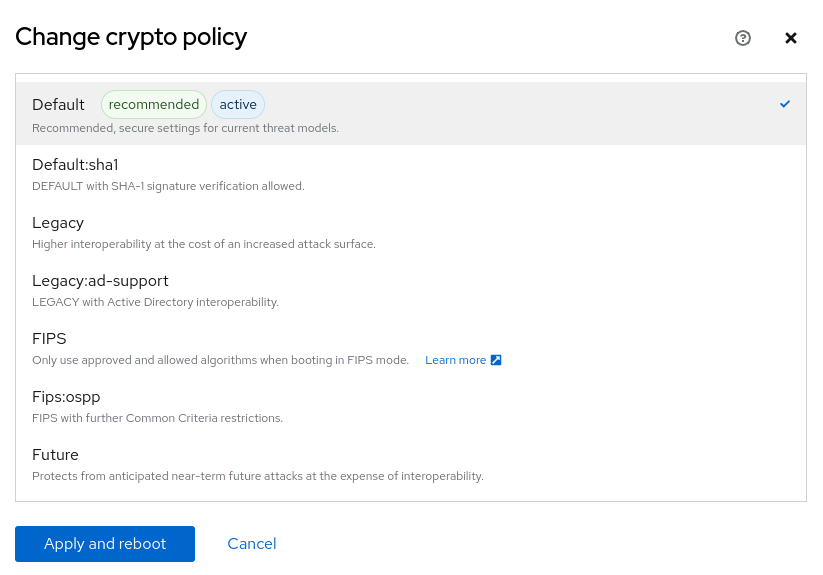
Newly available policy and sub-policies combinations are Default:sha1, Legacy:ad-support, and Fips:ospp.
Support for creating Podman pods
The web console now supports creating Podman pods (a group of containers) in addition to Podman containers. For more information on Podman pods, refer to the Working with pods documentation.
To create a Podman pod, start by clicking on Podman containers in the web console menu. You’ll now see a Create pod button in addition to the Create container button. When you click on Create pod, you’ll be prompted to configure the pod name, owner, port mappings and volumes.
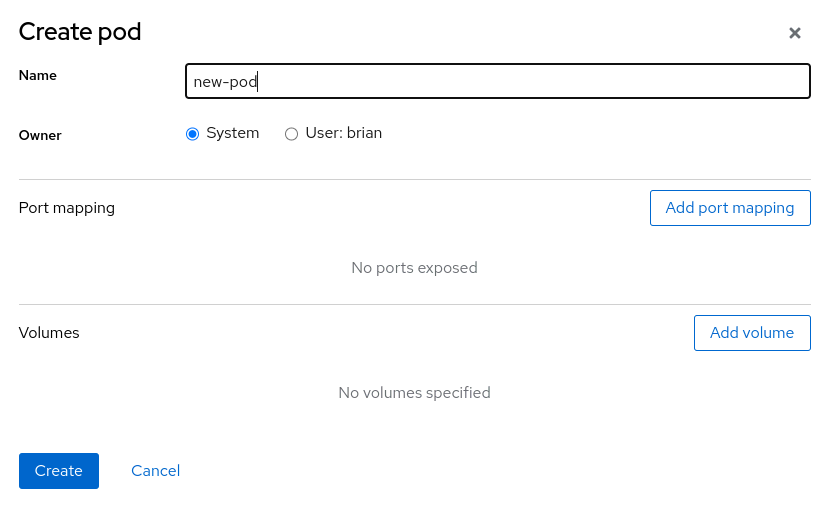
Once the pod has been created, you’ll then see a Create container in pod button that can be used to create one or more containers within the pod.
Ability to view disk read and write rates on individual devices
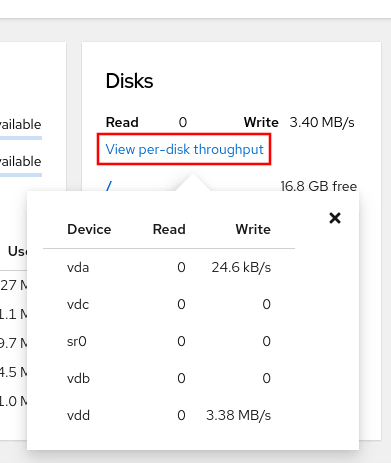
The web console can now display read and write rates on individual disk devices, which can help with understanding how disks are being utilized and assist with troubleshooting potential performance issues.
To view the current read and write rates on individual disk devices, click on Overview in the web console menu, and then click on View metrics and history under the Usage card.
Under the Disks card, you’ll see a View per-disk throughput link, which will show the current per-disk metrics.
Learn more
RHEL 9.2 and 8.8 include a number of exciting enhancements and new features related to the web console. If you’d like to try the RHEL web console, check out our interactive self-paced labs that allow you to experiment with and learn more about it:
Sobre el autor
Brian Smith is a product manager at Red Hat focused on RHEL automation and management. He has been at Red Hat since 2018, previously working with public sector customers as a technical account manager (TAM).
Más como éste
More than meets the eye: Behind the scenes of Red Hat Enterprise Linux 10 (Part 6)
Red Hat Enterprise Linux now available on the AWS European Sovereign Cloud
The Overlooked Operating System | Compiler: Stack/Unstuck
Linux, Shadowman, And Open Source Spirit | Compiler
Navegar por canal
Automatización
Las últimas novedades en la automatización de la TI para los equipos, la tecnología y los entornos
Inteligencia artificial
Descubra las actualizaciones en las plataformas que permiten a los clientes ejecutar cargas de trabajo de inteligecia artificial en cualquier lugar
Nube híbrida abierta
Vea como construimos un futuro flexible con la nube híbrida
Seguridad
Vea las últimas novedades sobre cómo reducimos los riesgos en entornos y tecnologías
Edge computing
Conozca las actualizaciones en las plataformas que simplifican las operaciones en el edge
Infraestructura
Vea las últimas novedades sobre la plataforma Linux empresarial líder en el mundo
Aplicaciones
Conozca nuestras soluciones para abordar los desafíos más complejos de las aplicaciones
Virtualización
El futuro de la virtualización empresarial para tus cargas de trabajo locales o en la nube
