As your business modernizes its cloud technology, it’s important to scale your cloud environments securely. Azure Red Hat OpenShift (ARO) supports your security needs at scale. With shared responsibility between Red Hat and Microsoft, ARO can help your organization boost cloud security in several ways.
Through ARO’s built-in security features your organization can simplify software deployment and reduce operational complexity with automated security maintenance and ongoing monitoring. The Red Hat Site Reliability Engineering (SRE) team automates, manages and monitors your platform so your business can focus on value-driven tasks without the burden of manually applying security updates and patches. As our SRE teams would say, “We make infrastructure boring.”
We continuously look for ways to improve security standards for customers, and recently we implemented several new security features.
Cybersecurity vulnerabilities (CVEs) and upgrades
Customers are able to take advantage of the benefits of the work the Red Hat Security team provides. The Red Hat security team looks at CVEs, identifies the severity, and if appropriate, provides errata for them. Red Hat Errata helps users determine what updates are available and how important they are based on analysis by Red Hat engineering. A majority of these Erratas will be provided via a version upgrade which can be applied to the clusters through either automated or manual tooling provided as part of Azure Red Hat OpenShift. The automated method leverages the recently released Managed Upgrade Operator. To configure the operator, all you have to do is apply a YAML file with a scheduled time at which you’d like the upgrade to take place and the operator will do the rest. For more details around how to configure the operator, refer to this document.
Cluster configuration upgrades
We continually work with Microsoft and customer security teams on implementing security best practices.
Two recently released features based on customer and Microsoft feedback include Storage and Egress Lockdown.
Storage Lockdown adds increased security to the storage accounts. This was done by changing the configuration of the storage account to force the use of a higher TLS version and a newer storage account version. It also checks to make sure the storage account is private and encryption is turned on. This feature is available for all Azure Red Hat OpenShift customers. Learn more about Storage lockdown.
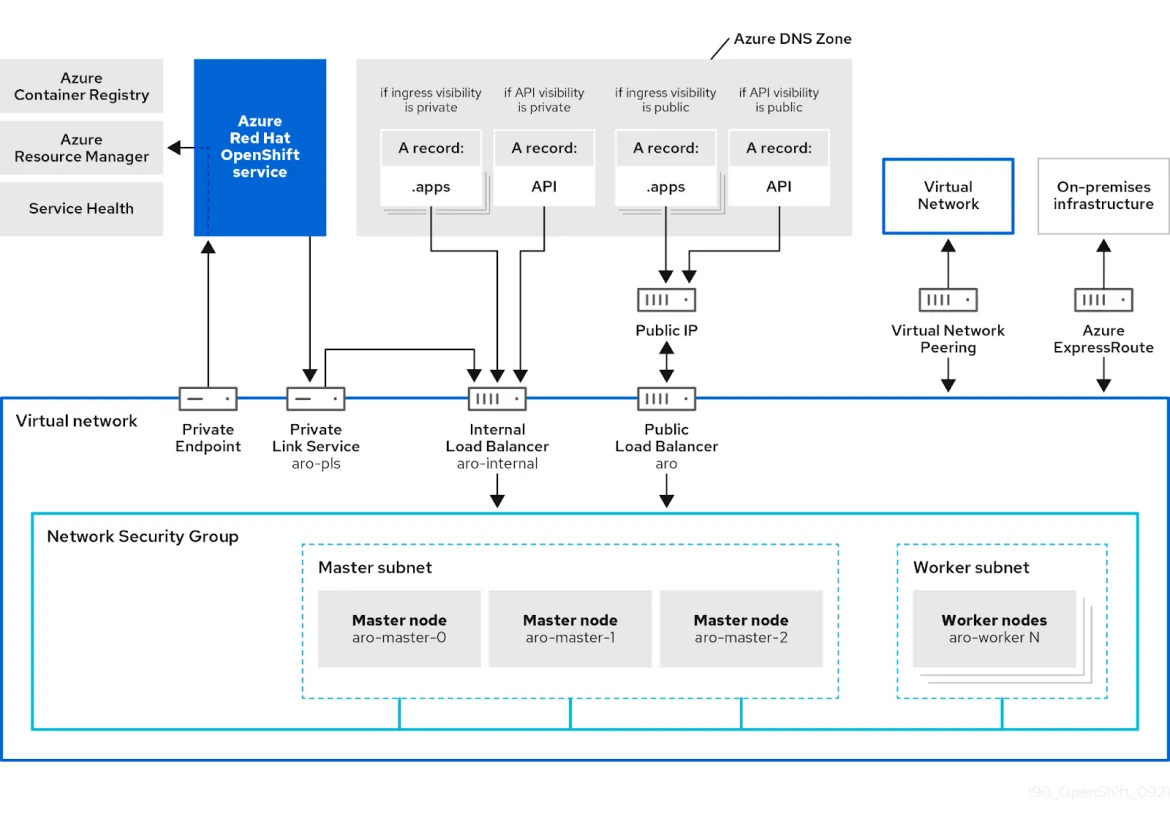
We also received feedback that while private clusters were private (no ingress allowed), customers wanted to limit the remaining dependency on Egress traffic. This dependency’s primary purpose was for the cluster to communicate with Azure endpoints (for example to the Azure container registry). To enhance the security of these deployments, we created a private endpoint which would provide access to the Azure resources, so clusters can be deployed without a path to the Internet, for minimal deployment scenarios. You will notice in the diagram below [1] a private endpoint which provides the cluster access to the service. This private endpoint provides exclusive access to the specific resources that the cluster depends on.
Figure 1 - Network topology of Azure Red Hat OpenShift
Some customers may elect to connect to additional registries or other external resources; this may be recommended for some use cases, as these can provide access to additional Red Hat Operators but this traffic would flow through the VNet peering and Azure Express route. Learn more about Egress Lockdown.
Compliance and certifications
Microsoft Azure offers a range of compliance solutions, and by using Azure Red Hat Openshift, customers get the benefits of Azure’s compliances coupled with Red Hats, combined to provide a large range of options.. Through the collaboration with Microsoft Azure, we have obtained numerous certifications inside their cloud, including PCI DSS, FedRAMP, HIPAA and many more. Visit the Azure compliance page for more information on these.
Red Hat also provides a full set of compliance tooling for additional security needs. Red Hat Advanced cluster Management provides management and controls via built-in policies which can be enforced upon Azure Red Hat OpenShift clusters. Red Hat Advanced Cluster Security (ACS) for Kubernetes provides a native Kubernetes security approach, adding an additional native layer of security to applications on the platform..
If you are looking to get started with Azure Red Hat OpenShift, read this blog to learn how to deploy the product through the Azure portal.
Sobre o autor
Navegue por canal
Automação
Últimas novidades em automação de TI para empresas de tecnologia, equipes e ambientes
Inteligência artificial
Descubra as atualizações nas plataformas que proporcionam aos clientes executar suas cargas de trabalho de IA em qualquer ambiente
Nuvem híbrida aberta
Veja como construímos um futuro mais flexível com a nuvem híbrida
Segurança
Veja as últimas novidades sobre como reduzimos riscos em ambientes e tecnologias
Edge computing
Saiba quais são as atualizações nas plataformas que simplificam as operações na borda
Infraestrutura
Saiba o que há de mais recente na plataforma Linux empresarial líder mundial
Aplicações
Conheça nossas soluções desenvolvidas para ajudar você a superar os desafios mais complexos de aplicações
Programas originais
Veja as histórias divertidas de criadores e líderes em tecnologia empresarial
Produtos
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Red Hat Cloud Services
- Veja todos os produtos
Ferramentas
- Treinamento e certificação
- Minha conta
- Suporte ao cliente
- Recursos para desenvolvedores
- Encontre um parceiro
- Red Hat Ecosystem Catalog
- Calculadora de valor Red Hat
- Documentação
Experimente, compre, venda
Comunicação
- Contate o setor de vendas
- Fale com o Atendimento ao Cliente
- Contate o setor de treinamento
- Redes sociais
Sobre a Red Hat
A Red Hat é a líder mundial em soluções empresariais open source como Linux, nuvem, containers e Kubernetes. Fornecemos soluções robustas que facilitam o trabalho em diversas plataformas e ambientes, do datacenter principal até a borda da rede.
Selecione um idioma
Red Hat legal and privacy links
- Sobre a Red Hat
- Oportunidades de emprego
- Eventos
- Escritórios
- Fale com a Red Hat
- Blog da Red Hat
- Diversidade, equidade e inclusão
- Cool Stuff Store
- Red Hat Summit