Prerequisites
Okta provides several paid offerings to customers. You can review them on the Okta page.
In this tutorial, I am using a developer account with the Okta platform. You can get a trial account here: https://developer.okta.com/signup/.
Along with this, you need the Openshift Container Platform environment for identity provider configuration.
Okta Configuration
Let’s first start with Okta configuration.
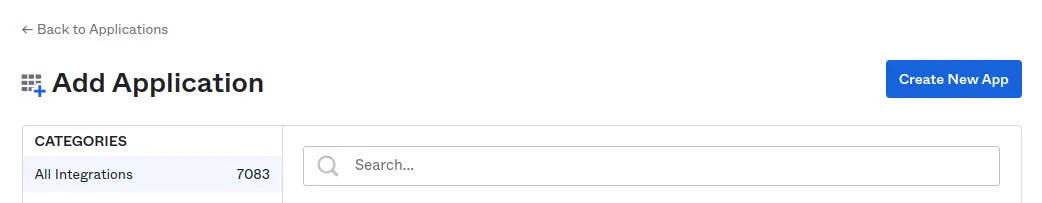
After you have logged into the Okta portal, go to the “Application” tab and click “Add Application”. This opens a new window:
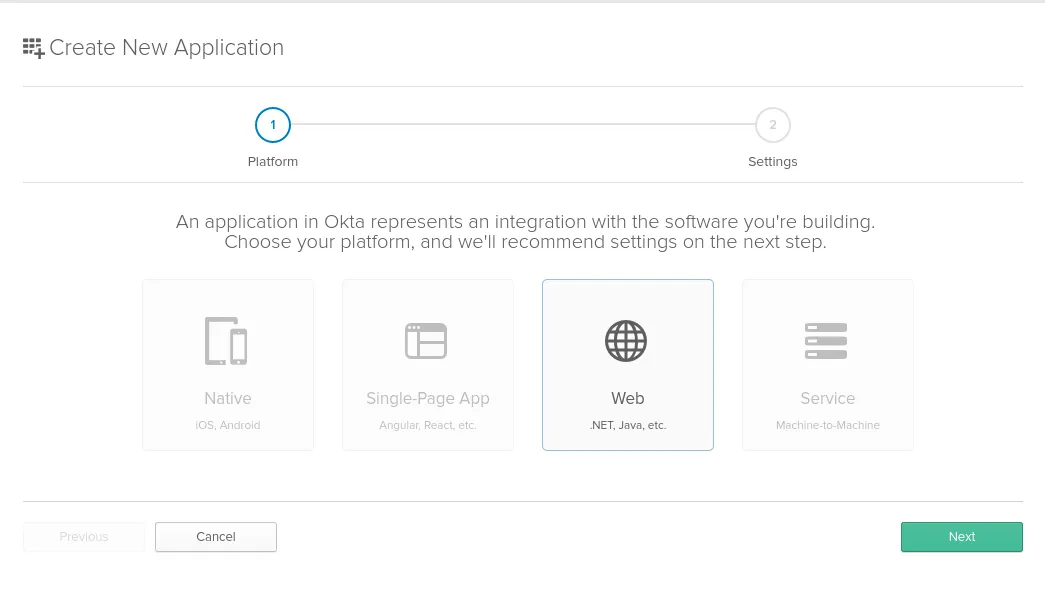
 Click “Create New App”. This opens a new window:
Click “Create New App”. This opens a new window:
Select the “Web” option and click “Next”:
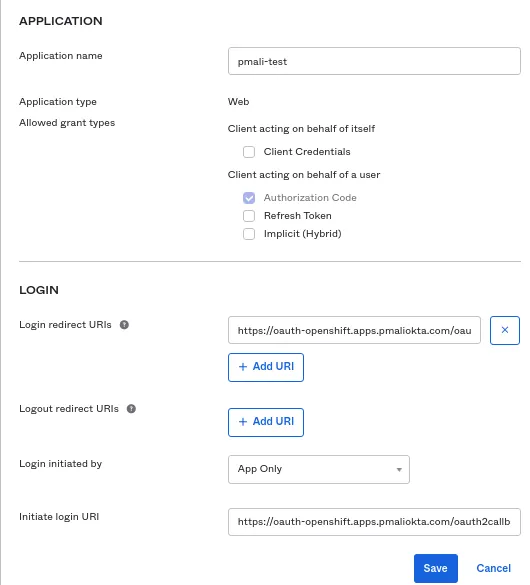
Add the details as below on the newly open window.
Set an “Application name”.
In the Login section, set “Login redirect URIs” and “Initiate login URI” as:
https://oauth-openshift.apps.<cluster-name>.<cluster-domain>/oauth2callback/
<idp-provider-name>
For example: https://oauth-opeshift-apps.pmaliokta.com/oauth2callback/okta
Here, make a note that <idp-provider-name> is the name that we are going to use in the OpenShift configuration to refer to the identity provider.
Click “Save”.
The next window shows you the Client ID and Client secret:
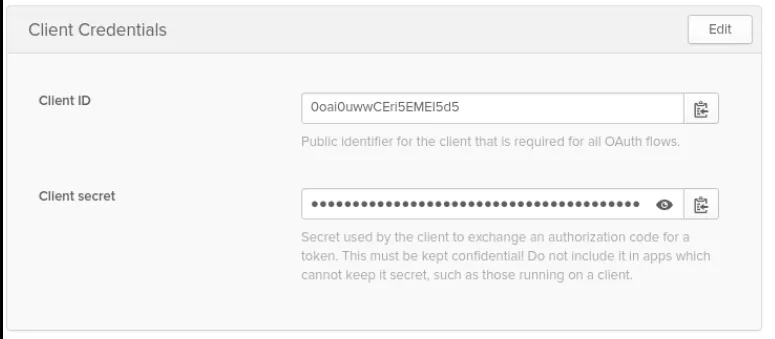 To view the Client secret, click the eye icon.
To view the Client secret, click the eye icon.
Store this Client ID and Client secret somewhere safe; they are needed when we configure OCP IDP configuration.
Here, Okta basic configuration is complete. Let’s move to Openshift Container Platform configuration.
OpenShift Container Platform Configuration
Let’s start with creating an Okta secret with the following command:
$ oc create secret generic openid-okta-secret --from-literal=clientSecret=6LKCbxG5ZpzAKNyUFsxUFnRv6D4purjnlVnM4ECl -n openshift-config
Here, the secret value is the client secret created in the Okta application.
Below is the OAuth configuration for the Okta identity provider:
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
name: cluster
spec:
identityProviders:
- mappingMethod: claim
name: okta
openID:
claims:
email:
name:
- name
preferredUsername:
- preferred_username
clientID: 0oai0uwwCEri5EMEI5d5
clientSecret:
name: openid-okta-secret
extraScopes:
- profile
issuer: https://dev-3523509.okta.com
type: OpenID
You can save the above CR in a file called okta-idp.yaml and use “oc apply -f okta-idp.yaml” to apply the configuration.
Points to note:
clientID: It’s a value created from an Okta application.
clientSecret: It’s a value created from an Okta application.
Issuer: Okta host name
After applying the configuration, check the pod status by executing the “oc get pods -n openshift-authentication” command and make sure the pod status is “Running”.
Then open a browser and navigate to the web console.
NOTE: You can obtain the link to the web console by executing “oc get routes -n openshift-console” from the OpenShift CLI.
Log in to the OpenShift web console using the Okta IDP.
After you have logged into the OCP dashboard, you can see the Okta username in the upper right of the dashboard. You can also verify using CLI with the following command:
$ oc get user
NAME UID FULL NAME IDENTITIES
pmali@redhat.com 86f10f6a-5a22-4873-8813-f145766890b0 Pravin M okta:00ui0qh30snvW6SPq5d5
Thanks for Reading
Hopefully, this article helps you configure basic Okta integration with OCP. For more information, be sure to check out Red Hat’s documentation on OpenID.
Sull'autore
Ricerca per canale
Automazione
Novità sull'automazione IT di tecnologie, team e ambienti
Intelligenza artificiale
Aggiornamenti sulle piattaforme che consentono alle aziende di eseguire carichi di lavoro IA ovunque
Hybrid cloud open source
Scopri come affrontare il futuro in modo più agile grazie al cloud ibrido
Sicurezza
Le ultime novità sulle nostre soluzioni per ridurre i rischi nelle tecnologie e negli ambienti
Edge computing
Aggiornamenti sulle piattaforme che semplificano l'operatività edge
Infrastruttura
Le ultime novità sulla piattaforma Linux aziendale leader a livello mondiale
Applicazioni
Approfondimenti sulle nostre soluzioni alle sfide applicative più difficili
Serie originali
Raccontiamo le interessanti storie di leader e creatori di tecnologie pensate per le aziende
Prodotti
- Red Hat Enterprise Linux
- Red Hat OpenShift
- Red Hat Ansible Automation Platform
- Servizi cloud
- Scopri tutti i prodotti
Strumenti
- Formazione e certificazioni
- Il mio account
- Supporto clienti
- Risorse per sviluppatori
- Trova un partner
- Red Hat Ecosystem Catalog
- Calcola il valore delle soluzioni Red Hat
- Documentazione
Prova, acquista, vendi
Comunica
- Contatta l'ufficio vendite
- Contatta l'assistenza clienti
- Contatta un esperto della formazione
- Social media
Informazioni su Red Hat
Red Hat è leader mondiale nella fornitura di soluzioni open source per le aziende, tra cui Linux, Kubernetes, container e soluzioni cloud. Le nostre soluzioni open source, rese sicure per un uso aziendale, consentono di operare su più piattaforme e ambienti, dal datacenter centrale all'edge della rete.
Seleziona la tua lingua
Red Hat legal and privacy links
- Informazioni su Red Hat
- Opportunità di lavoro
- Eventi
- Sedi
- Contattaci
- Blog di Red Hat
- Diversità, equità e inclusione
- Cool Stuff Store
- Red Hat Summit