Prerequisites
Okta provides several paid offerings to customers. You can review them on the Okta page.
In this tutorial, I am using a developer account with the Okta platform. You can get a trial account here: https://developer.okta.com/signup/.
Along with this, you need the Openshift Container Platform environment for identity provider configuration.
Okta Configuration
Let’s first start with Okta configuration.
After you have logged into the Okta portal, go to the “Application” tab and click “Add Application”. This opens a new window:
 Click “Create New App”. This opens a new window:
Click “Create New App”. This opens a new window:
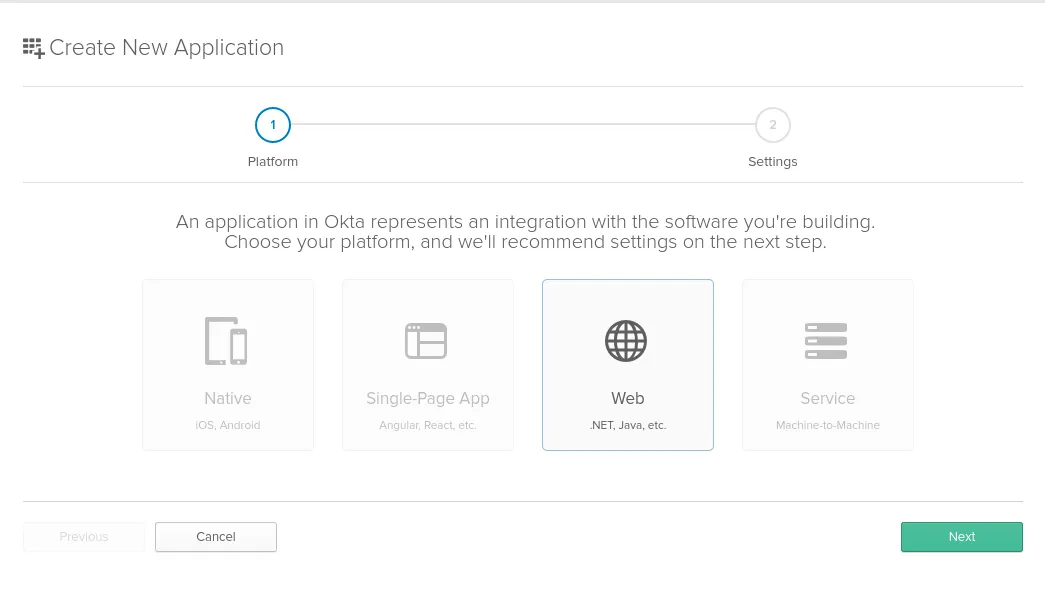
Select the “Web” option and click “Next”:
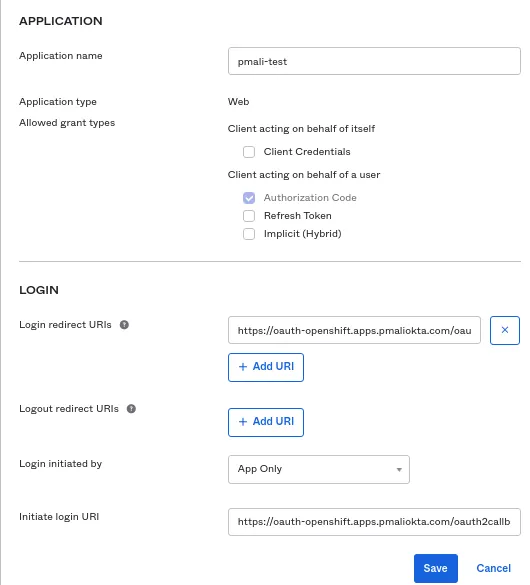
Add the details as below on the newly open window.
Set an “Application name”.
In the Login section, set “Login redirect URIs” and “Initiate login URI” as:
https://oauth-openshift.apps.<cluster-name>.<cluster-domain>/oauth2callback/
<idp-provider-name>
For example: https://oauth-opeshift-apps.pmaliokta.com/oauth2callback/okta
Here, make a note that <idp-provider-name> is the name that we are going to use in the OpenShift configuration to refer to the identity provider.
Click “Save”.
The next window shows you the Client ID and Client secret:
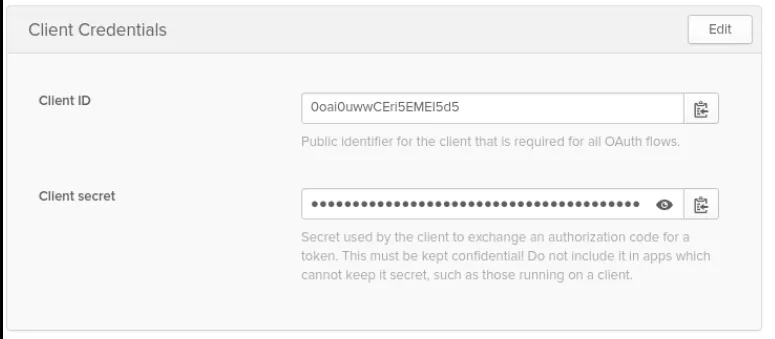 To view the Client secret, click the eye icon.
To view the Client secret, click the eye icon.
Store this Client ID and Client secret somewhere safe; they are needed when we configure OCP IDP configuration.
Here, Okta basic configuration is complete. Let’s move to Openshift Container Platform configuration.
OpenShift Container Platform Configuration
Let’s start with creating an Okta secret with the following command:
$ oc create secret generic openid-okta-secret --from-literal=clientSecret=6LKCbxG5ZpzAKNyUFsxUFnRv6D4purjnlVnM4ECl -n openshift-config
Here, the secret value is the client secret created in the Okta application.
Below is the OAuth configuration for the Okta identity provider:
apiVersion: config.openshift.io/v1
kind: OAuth
metadata:
name: cluster
spec:
identityProviders:
- mappingMethod: claim
name: okta
openID:
claims:
email:
name:
- name
preferredUsername:
- preferred_username
clientID: 0oai0uwwCEri5EMEI5d5
clientSecret:
name: openid-okta-secret
extraScopes:
- profile
issuer: https://dev-3523509.okta.com
type: OpenID
You can save the above CR in a file called okta-idp.yaml and use “oc apply -f okta-idp.yaml” to apply the configuration.
Points to note:
clientID: It’s a value created from an Okta application.
clientSecret: It’s a value created from an Okta application.
Issuer: Okta host name
After applying the configuration, check the pod status by executing the “oc get pods -n openshift-authentication” command and make sure the pod status is “Running”.
Then open a browser and navigate to the web console.
NOTE: You can obtain the link to the web console by executing “oc get routes -n openshift-console” from the OpenShift CLI.
Log in to the OpenShift web console using the Okta IDP.
After you have logged into the OCP dashboard, you can see the Okta username in the upper right of the dashboard. You can also verify using CLI with the following command:
$ oc get user
NAME UID FULL NAME IDENTITIES
pmali@redhat.com 86f10f6a-5a22-4873-8813-f145766890b0 Pravin M okta:00ui0qh30snvW6SPq5d5
Thanks for Reading
Hopefully, this article helps you configure basic Okta integration with OCP. For more information, be sure to check out Red Hat’s documentation on OpenID.
저자 소개
채널별 검색
오토메이션
기술, 팀, 인프라를 위한 IT 자동화 최신 동향
인공지능
고객이 어디서나 AI 워크로드를 실행할 수 있도록 지원하는 플랫폼 업데이트
오픈 하이브리드 클라우드
하이브리드 클라우드로 더욱 유연한 미래를 구축하는 방법을 알아보세요
보안
환경과 기술 전반에 걸쳐 리스크를 감소하는 방법에 대한 최신 정보
엣지 컴퓨팅
엣지에서의 운영을 단순화하는 플랫폼 업데이트
인프라
세계적으로 인정받은 기업용 Linux 플랫폼에 대한 최신 정보
애플리케이션
복잡한 애플리케이션에 대한 솔루션 더 보기
오리지널 쇼
엔터프라이즈 기술 분야의 제작자와 리더가 전하는 흥미로운 스토리
제품
- Red Hat Enterprise Linux
- Red Hat OpenShift Enterprise
- Red Hat Ansible Automation Platform
- 클라우드 서비스
- 모든 제품 보기
툴
체험, 구매 & 영업
커뮤니케이션
Red Hat 소개
Red Hat은 Linux, 클라우드, 컨테이너, 쿠버네티스 등을 포함한 글로벌 엔터프라이즈 오픈소스 솔루션 공급업체입니다. Red Hat은 코어 데이터센터에서 네트워크 엣지에 이르기까지 다양한 플랫폼과 환경에서 기업의 업무 편의성을 높여 주는 강화된 기능의 솔루션을 제공합니다.