This blog will highlight the new security features in the most recent release of Red Hat OpenStack Platform. Here are the security features you can expect in Red Hat OpenStack Platform 17.1.
Encrypted memcached
When using memcached, tokens and authentication responses are stored in the cache as raw data. If the cache is compromised, tokens and authentication responses become readable. Encrypting memcached content alleviates this concern. The OpenStack services that support memcached protection include Aodh, Barbican, Cinder, Glance, Gnocchi, Heat, Ironic, Neutron, Nova, and Panko; all services that use keystone middleware for authentication.
Secure Role-Based Access Control (SRBAC)
OpenStack's SRBAC is a security model that enables organizations to secure their OpenStack deployments by imposing strict and granular access control policies. It benefits various use cases, including data center security, compliance and auditing, multi-tenancy, and workload isolation, while providing advantages like granular control, simplified administration, enhanced security, improved workflow, and scalability.
SRBAC expands granular Role-Based Access Control of authorization across OpenStack services, providing increased functionality, improved auditability, and a reduced attack surface. This is a long-desired request for OpenStack, where OpenStack operators often want to provide a read-only view for specific users (such as auditors). Finally, SRBAC provides a read-only role for projects in Red Hat OpenStack Platform 17.1 (note: this is a day-one decision).
Fernet tokens benefits for end users
The benefits of using Fernet tokens may not be immediately apparent, but they confirm that the user's information is protected and that their experience is fast, convenient, and secure. Fernet tokens help provide the security of the Keystone user's sensitive information by encrypting it in transit, protecting it from potential threats.
Fernet tokens can be generated quickly and easily, making it easy for users to access their application without waiting for lengthy authentication processes. A primary advantage of Fernet tokens is that once Keystone generates them, they can be decrypted locally by another service. For other token types, the other service must talk to Keystone to validate the token presented by the user. Fernet tokens save the receiving service that extra round trip to Keystone.
Federation with OpenID Connect
Federation in OpenStack refers to the ability to authenticate and authorize users across different domains or systems. In the context of OpenStack, federation typically involves using an external identity provider (IdP) to manage user authentication and authorization rather than relying solely on the internal OpenStack identity service (Keystone).
One way to implement federation in OpenStack is through OpenID Connect (OIDC), an authentication protocol built on top of the OAuth 2.0 protocol. With OIDC, an external IdP can be used to authenticate users and assign roles based on mapping rules.
Once federation is configured and enabled in OpenStack, users can log into OpenStack using their credentials from the external IdP. Keystone can use the information provided by the IdP to authorize the user's access to resources in OpenStack.
Overall, federation with OpenID Connect in OpenStack can provide a more seamless and secure user authentication and authorization experience by allowing users to log in using their existing credentials and reducing the need for users to manage multiple sets of login credentials.
Federal Information Processing Standards (FIPS)-140 (ISO/IEC 19790) Mode
Enable strong encryption that meets the ISO/IEC 19790 level, also known as FIPS 140-3 in Red Hat OpenStack Platform (this is a day-one decision).
FIPS is a set of cryptographic standards developed by the U.S. National Institute of Standards and Technology (NIST) that is widely recognized as a security benchmark. FIPS mode verifies that cryptographic algorithms and modules used within OpenStack adhere to approved standards, providing a high level of assurance for encryption, digital signatures, and secure communications. This helps protect sensitive data such as user credentials, private keys, and communication channels against unauthorized access and tampering.
Many industries, especially those dealing with sensitive information like healthcare, finance, and government, have specific regulatory requirements that mandate using FIPS-certified cryptographic systems. Running OpenStack in FIPS mode helps organizations meet these compliance obligations, demonstrating that the system follows approved cryptographic standards.
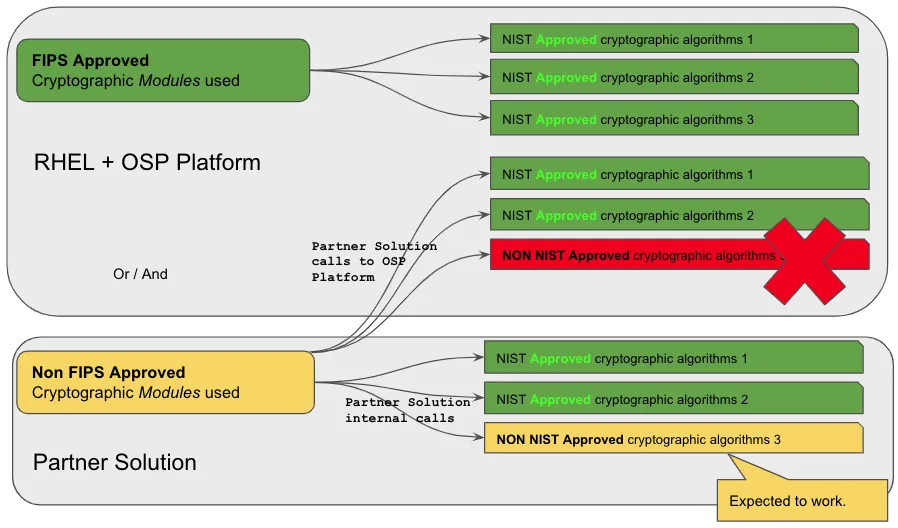
Deploying Red Hat OpenStack Platform in FIPS-140 mode impacts third-party solutions deployed alongside it. Let’s take a look:
Partners and customers running solutions in or on top of Red Hat OpenStack Platform are impacted by the switch to OpenStack strong encryption. A third-party solution that brings its own security within can be what the customer wants as long as they use their own cryptographic libraries and modules within their solution (the yellow boxes). The moment the third-party solution wants to interact with the platform or operating system by making a cryptographic call, it must use FIPS-level cryptography, or the call will fail.
Delivering FIPS-140 (ISO/IEC 19790) support for Red Hat OpenStack Platform is a part of the overall platform FIPS enablement, but you must carefully test your environment with all its non-Red Hat components to allow smooth operations.
Besides switching the underlying RHEL to use FIPS-approved cryptographic algorithms, as of Red Hat OpenStack Platform 17.1, there are just four OpenStack-related parameter changes that are applied to the deployments in FIPS-140 mode:
# Set ISCSI Chap algorithms to specifically disallow MD5
IscsidCHAPAlgorithms: 'SHA3-256,SHA256,SHA1'
# Set SnmpdReadonlyUserAuthType to not be 'MD5'
SnmpdReadonlyUserAuthType: 'SHA'
# Add RabbitAdditionalErlArgs for FIPS
RabbitFIPS: true
# Override gcomm_cipher for FIPS
MysqlGaleraSSLCipher: 'ECDHE-RSA-AES256-GCM-SHA384'
Wrap up
Find more information here about Red Hat Compliance Activities and Government Standards support (Red Hat Enterprise Linux 9 section is relevant to Red Hat OpenStack Platform 17.1).
Here is more information about FIPS-140 in Red Hat Enterprise Linux and its cryptographic profiles.
執筆者紹介
チャンネル別に見る
自動化
テクノロジー、チームおよび環境に関する IT 自動化の最新情報
AI (人工知能)
お客様が AI ワークロードをどこでも自由に実行することを可能にするプラットフォームについてのアップデート
オープン・ハイブリッドクラウド
ハイブリッドクラウドで柔軟に未来を築く方法をご確認ください。
セキュリティ
環境やテクノロジー全体に及ぶリスクを軽減する方法に関する最新情報
エッジコンピューティング
エッジでの運用を単純化するプラットフォームのアップデート
インフラストラクチャ
世界有数のエンタープライズ向け Linux プラットフォームの最新情報
アプリケーション
アプリケーションの最も困難な課題に対する Red Hat ソリューションの詳細
オリジナル番組
エンタープライズ向けテクノロジーのメーカーやリーダーによるストーリー
製品
ツール
試用、購入、販売
コミュニケーション
Red Hat について
エンタープライズ・オープンソース・ソリューションのプロバイダーとして世界をリードする Red Hat は、Linux、クラウド、コンテナ、Kubernetes などのテクノロジーを提供しています。Red Hat は強化されたソリューションを提供し、コアデータセンターからネットワークエッジまで、企業が複数のプラットフォームおよび環境間で容易に運用できるようにしています。
言語を選択してください
Red Hat legal and privacy links
- Red Hat について
- 採用情報
- イベント
- 各国のオフィス
- Red Hat へのお問い合わせ
- Red Hat ブログ
- ダイバーシティ、エクイティ、およびインクルージョン
- Cool Stuff Store
- Red Hat Summit