Quantum and post-quantum, what does it mean?
Quantum computing is an emerging technology that uses superposition, entanglement and interference to manipulate the state of a qubit (quantum bit) — this allows a quantum computer to evaluate multiple possibilities at the same time because it can hold the existence of opposing values in parallel (like Schrödinger’s cat experiment).
This is exciting for the prospects it can provide in computing and at the same time terrifying in the volume of attacks and security breaches it could contribute to. Quantum computing will make attacks possible that are not currently practically achievable. For example, RSA-2048 could take more human lifetimes to crack with traditional computing resources than humans will exist. With quantum computing, however, cracking classical cryptography like RSA-2048 becomes not only possible, but achievable within a reasonable period of time.
While quantum computers do not yet exist in a manner widely accessible, continued improvements and advancement in the quantum computing space increase the probability of existing, widespread cryptography being broken and compromised.
The basis of many core functions for governments, banks and personal privacy are built on cryptography’s ability to facilitate protection of sensitive data from exposure and maintain its authenticity and integrity throughout its life. When the basis of global trust (cryptography) becomes broken, societies and life-essential capabilities are impacted.
The history of cryptography is a war between cryptographers and cryptanalysts. However, since the advent of information technology, much of our cryptographic capabilities have not evolved; we’ve adapted to computational advances by simply increasing the key size to make it significantly more difficult, more resource intensive, and require more time to decrypt protected information. Quantum computers fundamentally change this paradigm. Key size increases will not be enough to prevent adversaries from accessing sensitive data.
"Post-quantum" is the term used to describe technologies that are capable of providing security guarantees which are resistant to the threat quantum computing presents. Without going into significant detail on how quantum computing can break classical cryptography, post-quantum cryptography must resist classical attacks as well as entirely new classes of attacks that take advantage of the capabilities and properties inherent to quantum computing (entanglement, superposition and interference).
What is Red Hat doing to adopt post-quantum cryptography?
Red Hat is engaged with various industry groups and open source projects to understand the performance, scalability and security impact that post-quantum cryptographic functions and their quantum-resistant algorithms have. Red Hat will evaluate and test these algorithms, as implemented by crypto-libraries, for incorporation into Red Hat products and projects.
Red Hat is committed to providing customers with functional, quantum-resistant security capabilities as the industry evolves, develops and begins integrating these new cryptographic functions. As the National Institute of Standards and Technology (NIST) continues working to select quantum-resistant algorithms and related protocols are approved by standards bodies (i.e. NIST, Internet Engineering Task Force (IETF), and others), these will be made broadly available for use.
The NIST approval process includes evaluating the maturity of the algorithm and corresponding implementations on a case-by-case basis. This may include monitoring activities by those groups and projects to identify gaps or delayed progress in adopting and integrating approved algorithms and corresponding libraries, and engaging as appropriate to continue advancement in that area.
Many world governments have proposed initial timelines for software manufacturers to provide post-quantum cryptographic functions. The dependency ecosystem that provides cryptographic functions is inherently complex, however, and the order of operations in making these changes globally will take significant time and testing in order to verify that existing transactions, communication protocols, protection mechanisms and signing flows are all still functional.
Red Hat anticipates that the proposed timelines will shift as cryptographic functions are approved and packages and libraries begin incorporating these functions within their existing release cycles. Red Hat has collected requirements and timeline expectations from the United States (US), Czech Republic, Germany, France and other governments to make sure that the event-driven roadmap addresses and is aligned with the defined outcomes of these government bodies.
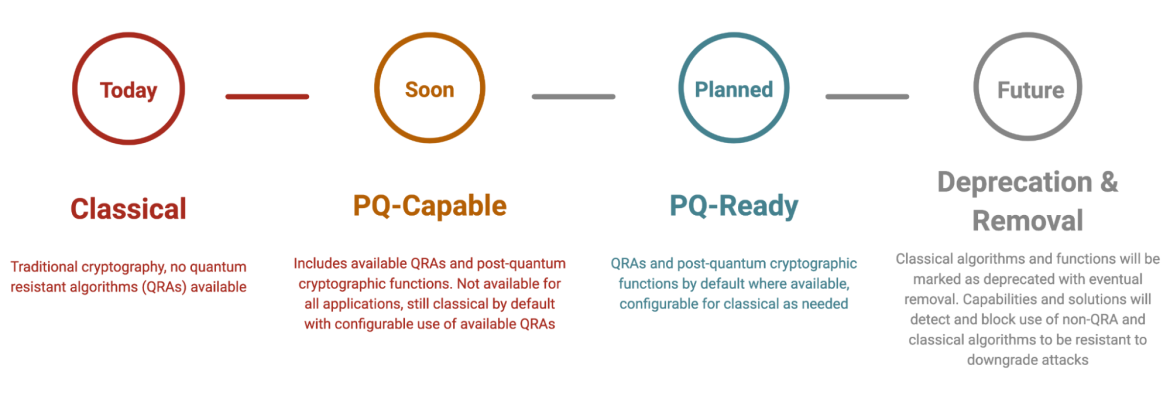
Red Hat’s phases of post-quantum cryptography inclusion
As part of Red Hat’s ongoing efforts to address quantum computing and quantum resistance in Red Hat products and their upstream projects, Red Hat plans to roll out these efforts in three initial phases. Additional phases may be added later to identify deprecation and eventual removal of classical cryptography with enforcement to prevent attackers from forcing systems to switch to less-secure cryptography, referred to as downgrade attacks.
For the purposes of these phases, references to post-quantum cryptographic functions are inclusive of quantum-resistant algorithms, which may be symmetric or asymmetric but still subject to approval by the aforementioned standards bodies.
Classical is the phase at which a given product or service does not include any post-quantum cryptographic functions.
Post-Quantum Capable (PQ-capable) is the phase at which a given product or service includes some post-quantum cryptographic functions. Post-quantum cryptographic functions may not be available for all applications and/or may not be configured to be default; classical cryptography and algorithms are still available for all applications and may be the default.
Post-Quantum Ready (PQ-ready) is the phase at which a given product or service includes post-quantum cryptographic functions by default for most applications, with classical cryptography and algorithms available to be configured by users who still need to retain classical methods for interoperability. PQ-Ready also supports approved hybrid schemes (classical and post-quantum) as they are available. Hybrid schemes combine the use of classical and post-quantum algorithms. In the event that a classical algorithm is defeated, the system remains secured through post-quantum algorithms. Should a post-quantum algorithm be defeated, the system remains secured through classical algorithms.
In the next article of this series, you’ll learn what to expect of Red Hat products as they begin adoption of post-quantum cryptographic functions and what you can do to assist your organization in achieving crypto-agility with Red Hat.
More information
If you have additional questions, please reach out to your Red Hat account manager. Red Hat is committed to supporting customers in achieving and maintaining post-quantum security.
執筆者紹介
Emily Fox is a DevOps enthusiast, security unicorn, and advocate for Women in Technology. She promotes the cross-pollination of development and security practices.
I am currently the Team Lead and Product Owner for the Red Hat Enterprise Linux Crypto Team. I joined Red Hat in 2007 and have covered several Software Development roles in the Identity Management and Security areas.
類似検索
チャンネル別に見る
自動化
テクノロジー、チームおよび環境に関する IT 自動化の最新情報
AI (人工知能)
お客様が AI ワークロードをどこでも自由に実行することを可能にするプラットフォームについてのアップデート
オープン・ハイブリッドクラウド
ハイブリッドクラウドで柔軟に未来を築く方法をご確認ください。
セキュリティ
環境やテクノロジー全体に及ぶリスクを軽減する方法に関する最新情報
エッジコンピューティング
エッジでの運用を単純化するプラットフォームのアップデート
インフラストラクチャ
世界有数のエンタープライズ向け Linux プラットフォームの最新情報
アプリケーション
アプリケーションの最も困難な課題に対する Red Hat ソリューションの詳細
オリジナル番組
エンタープライズ向けテクノロジーのメーカーやリーダーによるストーリー
製品
ツール
試用、購入、販売
コミュニケーション
Red Hat について
エンタープライズ・オープンソース・ソリューションのプロバイダーとして世界をリードする Red Hat は、Linux、クラウド、コンテナ、Kubernetes などのテクノロジーを提供しています。Red Hat は強化されたソリューションを提供し、コアデータセンターからネットワークエッジまで、企業が複数のプラットフォームおよび環境間で容易に運用できるようにしています。
言語を選択してください
Red Hat legal and privacy links
- Red Hat について
- 採用情報
- イベント
- 各国のオフィス
- Red Hat へのお問い合わせ
- Red Hat ブログ
- ダイバーシティ、エクイティ、およびインクルージョン
- Cool Stuff Store
- Red Hat Summit


